As developers, we're a prime target for social engineering scams. Hacking people is much easier than hacking infrastructures, and developers have access to things that are especially appealing to attackers.
While this article isn't strictly about coding - or even computers at all! - every dev should know how to avoid social engineering scams to keep themselves and their projects safe.
Target audience:
- Developers
- Everyone else, too
Be Careful With Sharing on Social Media
Does something about this tweet look concerning?
If you guessed "answering this question pretty much gives a hacker everything they need to reset your password" - then yep. Correct.
Gone are the days when tech-savvy people avoided having any online identity. Now, your Twitter name is your full name, and your workplace is in your bio (because what kind of dev doesn't love showing off?). With your name and workplace, attackers can guess your work email. If you start throwing in personal info like answers to security questions - it's over.
Even if your workplace doesn't have security questions, chances are your passwords are based on your personal info such as pet names anyway. 79% of users admit to having personal info in their passwords... and that's just the ones who admit to it.
Check out CUPP. CUPP is a tool where you can input someone's name, pet name, child name, DOB, etc. and generate a list of potential passwords. It works. Quite well.
In short: be careful with the info your share online!
Enable 2FA and Integrate it Into Your Projects
Wherever possible, enable 2FA on services you use, such as your Google account, bank accounts, Slack, etc. While 2FA isn't perfect, it's pretty close.
If you're working on a project that requires personal login and deals with any sensitive information, please consider coding a 2FA option into your app. Here are some resources:
- Just use Google Sign-In instead, maybe?
- Google Authenticator
- Authy
- The Pitfalls Of Developing Your Own 2FA
Don't Get Phished
Phishing is still the most popular form of social engineering. 92% of malware is delivered via email, and 95% of attacks on enterprise networks are the result of successful spear phishing.
Many developers are still operating on the archaic belief that phishing emails are poorly written, have terrible grammar and are obviously fake. Unfortunately, phishing emails have evolved significantly in the past few years. Nowadays, many phishing emails will be excellently written and almost indistinguishable from a legitimate email.
Here are some of the most common phishing scams lately:
Spear Phishing
Spear phishing involves selectively targetting employees, and developers are especially vulnerable. Spear phishers will discover information about you, and then selectively use it against you.
One of the most classic examples of spear phishing is sending fake invoices to people in finance teams. Lately, however, attackers have been expanding their reach by farming employee's social media accounts and sending them tailored email scams.
Here's a fun story.
So, I had to take a day off from work to take my dog to the vet. The team was short-staffed already, so I was feeling a little guilty.
I posted a pic of my dog on Instagram with the caption "Taking Lucy to the vet today. Feeling guilty about missing work though!"
About an hour later, I got this email from my boss:
"Hi [my name],
Hope Lucy is okay! But if you miss another day of work I might have to fire you. LOL.
Please send $15,000 to this client before COB today.
[client details]
Regards,
[boss' name]"
I was planning on transferring the amount, but it completely slipped my mind before the end of the day. I called my boss in panic apologizing for not paying the client in time.
He asked me what on Earth I was talking about.
Terrifying, right?
Spear phishing takes many forms and is becoming progressively more sophisticated with the rise of social media.
To protect yourself from spear phishing, consider the following:
- Was I expecting this email from this person? Have we discussed the matter through other channels previously?
- Does the email convey a sense of urgency?
- Does the email demand action from me?
- Can I confirm the authenticity of this email through other channels?
Also, check the sender's email address for any potential typos - e.g., replacing an "i" with an "l", or an "m" with "rn". Even if the email address is perfect, remember that spoofing addresses is simple and that there's no guarantee the email came from the shown source.
Impersonating Services
This is the most well-known form of phishing. It involves posing as a business, often styling emails to look like what that business would typically send. Here's an example with Dropbox:

Source: https://www.mailguard.com.au/blog/dropbox-phishing-180302
Fun fact: this form of phishing is how hackers got into John Podesta's email account!
To protect yourself from this type of phishing, consider the following:
- Does the email convey a sense of urgency, or demand action from me?
- Does anything look off about the sender?
- When I hover over links in the email, does the popup box show that they point to a strange location?
Smishing
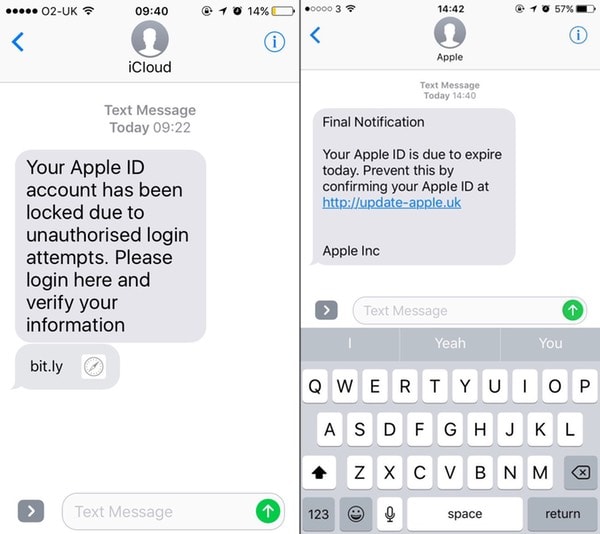
Source: https://www.welivesecurity.com/2016/11/10/apple-id-smishing-evolves-lure-victims/
Smishing (SMS phishing) is similar to standard phishing emails, but over SMS instead. Smishing texts will usually impersonate companies and encourage you to click on a link or give away your personal info.
Smishing attacks are difficult to detect, which is why the general advice is never to follow links you receive over text.
Vishing
Vishing ("voice" and "phishing") involves phishing through phone calls. Of course, this isn't a big deal to us, because what kind of developer seriously answers the phone nowadays? Just send me a text, FFS.
Most vishing relies on spoofing the caller ID to appear as a legitimate source. In a recent scam, attackers have been spoofing Apple. Phone calls coming from these scammers appear entirely legitimate, featuring "Apple Inc" as the caller name, and even showing Apple's logo. Victims would be prompted to share their personal information, and potentially make credit card purchases.
To avoid vishing, consider:
- Was I expecting this phone call?
- Does the call convey a sense of urgency, or demand action from me?
- Is the caller asking for my personal information?
Socialshing
Okay, I made that word up. But social media phishing is beginning to become a big deal. Here are some of the tactics to watch out for:
LinkedIn Contact Compromise:
In this attack, a hacker has already compromised one of your contacts. Through the contact, they leverage the trust you have and send you a message asking you to follow a link.
The Infamy Video:
A compromised contact, usually on Facebook, will send you a message with a link. They'll claim the link is a video of you doing something embarrassing, with a very high view count. If you click on the link, it'll redirect you to a fake Facebook login page.
Twitter Baiting:
An attacker will find a Twitter comment thread where a legitimate company is interacting with some users. The attacker will set the same display name and profile picture as the company, then insert themselves into the thread, usually encouraging users to click on a malicious link.
Automate, Automate, Automate
Where possible, try to integrate automation into your security practices. Humans can only be so aware, and there's a lot of awesome apps out there that help fill the gaps. Enable 2FA, install a password manager if you haven't already, and scan your networks regularly.
Stay Safe!
The world is a scary place, and everyone is out to get you. Try to stay up to date on the latest phishing scams, as attackers are continually learning and are never too far behind us.
Happy hacking!
This post was originally published on explainhownow.com






Top comments (20)
I have a simple rule: Does this account have any way to get to my money? if yes, apply 2FA.
I feel that in 2019 services like Google or Microsoft, that have a payment method attached to it and more or less are our digital identity holders, should encourage 2FA to the point of rewarding it.
Just on point 👌
Being an ex-hacker myself, I would say that my job would require 70% of social engineering skills, and the rest is tech skills.
Aside from that, the likelihood of performing any attack (esp. on a big company) with only tech skills is just soooooo low.
"... as a ..." really ! how many non ex hackers do you know ? be careful this is a phishy question :)
a friend of mine bugged me to chip in on a kickstarter for an open-source yubikey alternative, and it has turned out to be one of the best purchases i've ever made. no longer am i held hostage to the whims of my own stupidity when it comes to poor infosec - though i suppose i might change my opinion if i ever happen to wake up after a particularly celebratory night to discover i lost my keys and keychain :P
it works very well for me as i am not a very organized person, and i think maintaining a centralized password app requires a degree of discipline. alongside that is my personal experience with dashlane - which might rival firefox's "allow notifications?" as one of the most downright annoying things i've ever had to put up with on a desktop. like alot of folks i know, i keep my keys - and my usb 2fa - on a caribiner, so (knock on wood) it's pretty convenient on top of the physical layer of security it provides. despite it not being widely accepted yet, it does work with google, and that's all i need to access alot of my services thanks to SSO logins and whatnot.
Oh nice, the Yubikey is awesome! I really want one but honestly, I'm ditsy AF sometimes and would probably lose it.
that's why you should get two :D one that travels with you and one in a safe place at home
Loved this post, congratulations! However I think there is maybe a small paragraph missing about in person social engineering. Many companies have been compromised in the past by having a hacker simply pose as a janitor and access a terminal in the company or simply see the logins written on post-it notes on the screen.
Good point! Thanks for the comment. May update the article later to write a bit on that.
Looking forward to it! Keep up the good work I need to find the time to write more articles on security as well.
I love made up words! Another really great post. I have not heard of CUPP before i'm going to have to check that out! I'm always curious about phishing email trends. I always encourage people, no matter what their job is, to share with the IT/Security team the common themes or trends they are seeing. Trying to keep an open communication channel is so important for spotting, detecting, mitigating and preventing phishing.
Thanks for your comment Spencer! And you're absolutely right. Earlier this year I worked for a company here in Australia that's known for having a great security culture. They have multiple teams dedicated to educating employees within the company on security trends, especially phishing, and they always encourage employees to send fishy looking stuff to these teams. It works really well.
Sweet post! Your website looks cool too, gonna check out the articles later. I'd like to scan my network, but not sure where to start. Any advice?
Awesome question! If you're cool waiting about a week I can make my next post on that?
Wow that'd be sweet, I'll look out for it!
dev.to/kathyra_/scan-networks-for-...
As promised!
Wonderful, I’ll check it out. Thanks!!
So interesting, love this article. People need to realize that the reason most scam mails are poorly written is because they're very smartly targeted at a particular demographic.
Once the scammers come for you, they're going to put as much effort into tailoring the messaging for you!
Btw maybe you could also mention using a Password Manager? Solves the issue of leaking pet names and private information etc.
Thanks for your comment! :))
I did mention password managers in the automation section. Personally, I love them, but I didn't want to make it a key focus because a lot of people work for companies where password managers aren't allowed (which I think is stupid, but that's another issue entirely).
I come to live rather than keep careful.
Vishing? I had never heard of the term? I thought the actual term was phreaking.