My picoCTF 2022 writeups are broken up into the following sections,
1. Forensics (Solved 13/13)
2. Cryptography (Solved 11/15)
3. Binary Exploitation (Solved 5/14)
4. Reverse Engineering (Solved 2/12)
5. Web Exploitation (Solved 2/12)
All my writeups can also be found on my GitHub's CTFwriteups repository
The Cryptography challenges I solved in picoCTF 2022 are the following,
Table of Contents
100 points
basic-mod1
The challenge is the following,
We are also given the file message.txt which contains,
54 211 168 309 262 110 272 73 54 137 131 383 188 332 39 396 370 182 328 327 366 70
I followed what the challenge said, and applied mod 37 to each of the numbers,
17 26 20 13 3 36 13 36 17 26 20 13 3 36 2 26 0 34 32 31 33 33
The number to character map used here is,
A: 0
B: 1
C: 2
D: 3
E: 4
F: 5
G: 6
H: 7
I: 8
J: 9
K: 10
L: 11
M: 12
N: 13
O: 14
P: 15
Q: 16
R: 17
S: 18
T: 19
U: 20
V: 21
W: 22
X: 23
Y: 24
Z: 25
0: 26
1: 27
2: 28
3: 29
4: 30
5: 31
6: 32
7: 33
8: 34
9: 35
_: 36
After I mapped the numbers to their respective characters, I got,
R 0 U N D _ N _ R 0 U N D _ C 0 A 8 6 5 7 7
Therefore, the flag is,
picoCTF{R0UND_N_R0UND_C0A86577}
basic-mod2
The challenge is the following,
We are also given the file message.txt which contains,
145 167 233 272 344 91 395 393 433 92 77 414 344 318 420 263 87 186 96 103 91 354 161
I followed what the challenge said, and applied mod 41 to each number and took the modular inverse using this Online Modular Multiplicative Inverse Calculator,
28 14 22 30 18 32 30 12 25 37 8 31 18 4 37 29 33 28 3 2 32 30 27
The number to character map used here is,
A: 1
B: 2
C: 3
D: 4
E: 5
F: 6
G: 7
H: 8
I: 9
J: 10
K: 11
L: 12
M: 13
N: 14
O: 15
P: 16
Q: 17
R: 18
S: 19
T: 20
U: 21
V: 22
W: 23
X: 24
Y: 25
Z: 26
0: 27
1: 28
2: 29
3: 30
4: 31
5: 32
6: 33
7: 34
8: 35
9: 36
_: 37
After I mapped the numbers to their respective characters, I got,
1 N V 3 R 5 3 L Y _ H 4 R D _ 2 6 1 C B 5 3 0
Therefore, the flag is,
picoCTF{1NV3R53LY_H4RD_261CB530}
credstuff
The challenge is the following,
We are also given the file leak.tar. I uncompressed this, and gave a text files usernames.txt and passwords.txt.
The challenge told us to look for the user cultiris, which was on line 378 of usernames.txt. I looked at line 378 of passwords.txt.
cultiris's password was cvpbPGS{P7e1S_54I35_71Z3}. I assumed this was a ROT cipher, so I went over to CyberChef and applied the ROT 13 cipher.
Therefore, the flag is,
picoCTF{C7r1F_54V35_71M3}.
morse-code
The challenge is the following,
We are also given the file morse_chal.wav. Writing down the dot and dashes from the audio, I got the following,
.-- .... ....- --... / .... ....- --... .... / ----. ----- -.. / .-- ..--- ----- ..- ----. .... --...
I looked at the Morse code table,
I used this to translate the morse code, which gave me,
wh47 h47h 90d w20u9h7
Therefore, the flag is,
picoCTF{wh47_h47h_90d_w20u9h7}
rail-fence
The challenge is the following,
We are also given the file message.txt which contains,
Ta _7N6DE7hlg:W3D_H3C31N__BD4ef sHR053F38N43D47 i33___NC
The challenge tells us that this was encrypted using the rail fence with 4 rails, so I went to Dcode.fr Rail Fence Cipher and decrypted it using 4 rails.
Decoding this gave me,
The·flag·is:·WH3R3_D035_7H3_F3NC3_8361N_4ND_3ND_EB4C7D74
Therefore, the flag is,
picoCTF{WH3R3_D035_7H3_F3NC3_8361N_4ND_3ND_EB4C7D74}
substitution0
The challenge is the following,
We are also given the file message.txt which contains,
UHQKRNWLFIYJBTODCZVAXEGSMP
Lrzrxdot Jrwzutk uzovr, gfal u wzuer utk vauarjm ufz, utk hzoxwla br alr hrrajr
nzob u wjuvv quvr ft glfql fa guv rtqjovrk. Fa guv u hruxafnxj vquzuhurxv, utk, ua
alua afbr, xtytogt ao tuaxzujfvav—on qoxzvr u wzrua dzfpr ft u vqfrtafnfq dofta
on efrg. Alrzr grzr ago zoxtk hjuqy vdoav truz otr rsazrbfam on alr huqy, utk u
jotw otr truz alr oalrz. Alr vqujrv grzr rsqrrkftwjm luzk utk wjovvm, gfal ujj alr
uddruzutqr on hxztfvlrk wojk. Alr grfwla on alr ftvrqa guv erzm zrbuzyuhjr, utk,
auyftw ujj alftwv ftao qotvfkrzuafot, F qoxjk luzkjm hjubr Ixdfarz noz lfv odftfot
zrvdrqaftw fa.
Alr njuw fv: dfqoQAN{5XH5717X710T_3E0JX710T_7H755H1U}
I saw the UHQKRNWLFIYJBTODCZVAXEGSMP, and assumed that this maps to ABCDEFGHIJKLMNOPQRSTUVWXYZ, so I substituted these captial letters using CyberChef.
ABCDEFGHIJKLMNOPQRSTUVWXYZ
Hrzrxdot Lrwzutk uzovr, gfal u wzuer utk vauarjm ufz, utk hzoxwla br alr hrrajr
nzob u wjuvv quvr ft glfql fa guv rtqjovrk. Ia guv u hruxafnxj vquzuhurxv, utk, ua
alua afbr, xtytogt ao tuaxzujfvav—on qoxzvr u wzrua dzfpr ft u vqfrtafnfq dofta
on efrg. Tlrzr grzr ago zoxtk hjuqy vdoav truz otr rsazrbfam on alr huqy, utk u
jotw otr truz alr oalrz. Tlr vqujrv grzr rsqrrkftwjm luzk utk wjovvm, gfal ujj alr
uddruzutqr on hxztfvlrk wojk. Tlr grfwla on alr ftvrqa guv erzm zrbuzyuhjr, utk,
auyftw ujj alftwv ftao qotvfkrzuafot, I qoxjk luzkjm hjubr Jxdfarz noz lfv odftfot
zrvdrqaftw fa.
Tlr njuw fv: dfqoCTF{5UB5717U710N_3V0LU710N_7B755B1A}
So I substituted the lower case too, so the substitution letter set was,
UHQKRNWLFIYJBTODCZVAXEGSMPuhqkrnwlfiyjbtodczvaxegsmp
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz
The substituted message looked like the following,
ABCDEFGHIJKLMNOPQRSTUVWXYZ
Hereupon Legrand arose, with a grave and stately air, and brought me the beetle
from a glass case in which it was enclosed. It was a beautiful scarabaeus, and, at
that time, unknown to naturalists—of course a great prize in a scientific point
of view. There were two round black spots near one extremity of the back, and a
long one near the other. The scales were exceedingly hard and glossy, with all the
appearance of burnished gold. The weight of the insect was very remarkable, and,
taking all things into consideration, I could hardly blame Jupiter for his opinion
respecting it.
The flag is: picoCTF{5UB5717U710N_3V0LU710N_7B755B1A}
Therefore, the flag is,
picoCTF{5UB5717U710N_3V0LU710N_7B755B1A}
substitution1
The challenge is the following,
We are also given the file message.txt which contains,
PZKh (hbutz kut pfszatx zbx kcfd) ftx f zjsx uk puqsazxt hxpatnzj puqsxznznul. Pulzxhzflzh ftx stxhxlzxi gnzb f hxz uk pbfccxldxh gbnpb zxhz zbxnt
ptxfznynzj, zxpblnpfc (fli duudcnld) hencch, fli stuvcxq-hucynld fvncnzj. Pbfccxldxh ahafccj puyxt f laqvxt uk pfzxdutnxh, fli gbxl hucyxi, xfpb jnxcih
f hztnld (pfccxi f kcfd) gbnpb nh havqnzzxi zu fl ulcnlx hputnld hxtynpx. PZKh ftx f dtxfz gfj zu cxftl f gnix fttfj uk puqsazxt hxpatnzj hencch nl f
hfkx, cxdfc xlyntulqxlz, fli ftx buhzxi fli scfjxi vj qflj hxpatnzj dtuash ftuali zbx gutci kut kal fli stfpznpx. Kut zbnh stuvcxq, zbx kcfd nh:
snpuPZK{KT3WA3LPJ_4774PE5_4T3_P001_X57444FP}
I know the flag format is picoCTF{xxx}, so I knew I had to replace snpuPZK with picoCTF. The lowercase/uppercase of the letter must be replaced, so I used the following character set map.
snpuPZKSNPUpzk
picoCTFPICOctf
Which gave me,
CTFh (hbott fot cfptatx tbx fcfd) ftx f tjpx of coqpatxt hxcatitj coqpxtitiol. Coltxhtflth ftx ptxhxltxi gitb f hxt of cbfccxldxh gbicb txht tbxit
ctxftiyitj, txcblicfc (fli doodcild) heicch, fli ptovcxq-hocyild fvicitj. Cbfccxldxh ahafccj coyxt f laqvxt of cftxdotixh, fli gbxl hocyxi, xfcb jixcih
f httild (cfccxi f fcfd) gbicb ih havqittxi to fl olcilx hcotild hxtyicx. CTFh ftx f dtxft gfj to cxftl f giix fttfj of coqpatxt hxcatitj heicch il f
hffx, cxdfc xlyitolqxlt, fli ftx bohtxi fli pcfjxi vj qflj hxcatitj dtoaph ftoali tbx gotci fot fal fli ptfcticx. Fot tbih ptovcxq, tbx fcfd ih:
picoCTF{FT3WA3LCJ_4774CE5_4T3_C001_X57444FC}
From this point onwards, I used a similar method to challenge in another CTF I did, and the details can be found here. I looked for words like fot, tbih and assumed they were for, this respectively. So I used the following character set map,
snpuPZKSNPUpzktbh
picoCTFPICOctfrhs
Which gave me,
CTFs (short for cfptarx thx fcfd) frx f tjpx of coqpatxr sxcaritj coqpxtitiol. Coltxstflts frx prxsxltxi gith f sxt of chfccxldxs ghich txst thxir
crxftiyitj, txchlicfc (fli doodcild) seiccs, fli provcxq-socyild fvicitj. Chfccxldxs asafccj coyxr f laqvxr of cftxdorixs, fli ghxl socyxi, xfch jixcis
f strild (cfccxi f fcfd) ghich is savqittxi to fl olcilx scorild sxryicx. CTFs frx f drxft gfj to cxfrl f giix frrfj of coqpatxr sxcaritj seiccs il f
sffx, cxdfc xlyirolqxlt, fli frx hostxi fli pcfjxi vj qflj sxcaritj droaps froali thx gorci for fal fli prfcticx. For this provcxq, thx fcfd is:
picoCTF{FT3WA3LCJ_4774CE5_4T3_C001_X57444FC}
From assuming words, I got,
CTFs (short for capture the flag) are a tjpe of computer securitj competitiol. Coltestalts are preseltei gith a set of challelges ghich test their
creatiyitj, techlical (ali googlilg) seills, ali problem-solyilg abilitj. Challelges usuallj coyer a lumber of categories, ali ghel solyei, each jielis
a strilg (callei a flag) ghich is submittei to al ollile scorilg seryice. CTFs are a great gaj to learl a giie arraj of computer securitj seills il a
safe, legal elyirolmelt, ali are hostei ali plajei bj malj securitj groups arouli the gorli for ful ali practice. For this problem, the flag is:
picoCTF{FT3WA3LCJ_4774CE5_4T3_C001_X57444FC}
The text started to make more sense, and at this point, I was using
snpuPZKSNPUpzktbhvcxqfadjligye
picoCTFPICOctfrhsblemaugyndwvk
Which gave,
CTFs (short for capture the flag) are a type of computer security competition. Contestants are presented with a set of challenges which test their
creativity, technical (and googling) skills, and problem-solving ability. Challenges usually cover a number of categories, and when solved, each yields
a string (called a flag) which is submitted to an online scoring service. CTFs are a great way to learn a wide array of computer security skills in a
safe, legal environment, and are hosted and played by many security groups around the world for fun and practice. For this problem, the flag is:
picoCTF{FT3WA3LCJ_4774CE5_4T3_C001_X57444FC}
Now, I just had to replace the capital letters,
snpuPZKSNPUpzktbhvcxqfadjligyeTBHVCXQFADJLIGYEW
picoCTFPICOctfrhsblemaugyndwvkRHSBLEMAUGYNDWVKQ
Which gave,
CTFs (short for capture the flag) are a type of computer security competition. Contestants are presented with a set of challenges which test their
creativity, technical (and googling) skills, and problem-solving ability. Challenges usually cover a number of categories, and when solved, each yields
a string (called a flag) which is submitted to an online scoring service. CTFs are a great way to learn a wide array of computer security skills in a
safe, legal environment, and are hosted and played by many security groups around the world for fun and practice. For this problem, the flag is:
picoCTF{FR3QU3NCY_4774CK5_4R3_C001_E57444AC}
Therefore, the flag is,
picoCTF{FR3QU3NCY_4774CK5_4R3_C001_E57444AC}
substitution2
The challenge is the following,
We are also given the file message.txt which contains,
cwaiaafqzczakailbmcwaijabbazclnbqzwaxwqowzswmmbsmtdrcaizasriqcusmtdacqcqmezqesbrxqeosunaidlciqmclexrzsunaiswlbbaeoacwazasmtdacqcqmezpmsrzdiqtliqbumezuzca
tzlxtqeqzcilcqmeprexltaeclbzjwqswliakaiurzaprblextlihaclnbazhqbbzwmjakaijanabqakacwadimdaidridmzamplwqowzswmmbsmtdrcaizasriqcusmtdacqcqmeqzemcmebucmcalsw
klbrlnbazhqbbznrclbzmcmoaczcrxaeczqecaiazcaxqelexafsqcaxlnmrcsmtdrcaizsqaesaxapaezqkasmtdacqcqmezliampcaeblnmiqmrzlpplqizlexsmtaxmjecmireeqeoswashbqzczle
xafasrcqeosmepqozsiqdczmppaezamecwamcwaiwlexqzwalkqbupmsrzaxmeafdbmilcqmelexqtdimkqzlcqmelexmpcaewlzabataeczmpdblujanabqakalsmtdacqcqmecmrswqeomecwamppae
zqkaabataeczmpsmtdrcaizasriqcuqzcwaiapmialnaccaikawqsbapmicaswakleoabqztcmzcrxaeczqeltaiqslewqowzswmmbzpricwaijanabqakacwlclerexaizclexqeompmppaezqkacasw
eqyrazqzazzaecqlbpmitmrecqeoleappascqkaxapaezalexcwlccwacmmbzlexsmepqorilcqmepmsrzaesmrecaiaxqexapaezqkasmtdacqcqmezxmazemcbalxzcrxaeczcmhemjcwaqiaeatulz
appascqkabulzcalswqeocwatcmlscqkabucwqehbqhalelcclshaidqsmscpqzlemppaezqkabumiqaecaxwqowzswmmbsmtdrcaizasriqcusmtdacqcqmecwlczaahzcmoaeailcaqecaiazcqesmt
drcaizsqaesaltmeowqowzswmmbaizcalswqeocwataemrowlnmrcsmtdrcaizasriqcucmdqyracwaqisriqmzqcutmcqklcqeocwatcmafdbmiamecwaqimjelexaelnbqeocwatcmnaccaixapaexc
waqitlswqeazcwapbloqzdqsmSCP{E6I4T_4E41U515_15_73X10R5_6SXLAL76}
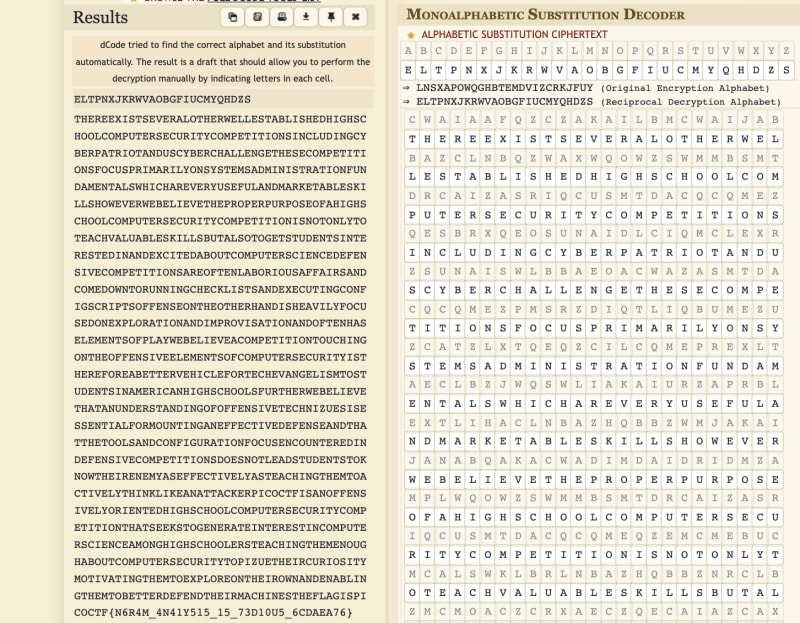
This time, it did not have spaces so guessing the words would be more difficult. I already did manual substitution in substitution0 and substitution1 so this time I decided to use an Automatic Monoalphabetic substitution decoder, which gave me,
This actually already gives the flag, but I wanted to differentiate between the lowercase and uppcase so decided to do manual substitution from here.
From the automatic substitution, it showed that it uses a character map set of,
abcdefghijklmnopqrstuvwxyz
eltpnxjkrwvaobgfiucmyqhdzs
Manual substitution gave me,
thereexistseveralotherwellestablishedhighschoolcomputersecuritycompetitionsincludingcyberpatriotanduscyberchallengethesecompetitionsfocusprimarilyonsyste
msadministrationfundamentalswhichareveryusefulandmarketableskillshoweverwebelievetheproperpurposeofahighschoolcomputersecuritycompetitionisnotonlytoteach
valuableskillsbutalsotogetstudentsinterestedinandexcitedaboutcomputersciencedefensivecompetitionsareoftenlaboriousaffairsandcomedowntorunningchecklistsan
dexecutingconfigscriptsoffenseontheotherhandisheavilyfocusedonexplorationandimprovisationandoftenhaselementsofplaywebelieveacompetitiontouchingontheoffen
siveelementsofcomputersecurityisthereforeabettervehiclefortechevangelismtostudentsinamericanhighschoolsfurtherwebelievethatanunderstandingofoffensivetech
nizuesisessentialformountinganeffectivedefenseandthatthetoolsandconfigurationfocusencounteredindefensivecompetitionsdoesnotleadstudentstoknowtheirenemyas
effectivelyasteachingthemtoactivelythinklikeanattackerpicoctfisanoffensivelyorientedhighschoolcomputersecuritycompetitionthatseekstogenerateinterestincom
puterscienceamonghighschoolersteachingthemenoughaboutcomputersecuritytopizuetheircuriositymotivatingthemtoexploreontheirownandenablingthemtobetterdefendt
heirmachinestheflagispicoSCP{E6I4T_4E41U515_15_73X10R5_6SXLAL76}
Now I just needed to substitute the uppercases,
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ
eltpnxjkrwvaobgfiucmyqhdzsELTPNXJKRWVAOBGFIUCMYQHDZS
Which gave me,
thereexistseveralotherwellestablishedhighschoolcomputersecuritycompetitionsincludingcyberpatriotanduscyberchallengethesecompetitionsfocusprimarilyonsyste
msadministrationfundamentalswhichareveryusefulandmarketableskillshoweverwebelievetheproperpurposeofahighschoolcomputersecuritycompetitionisnotonlytoteach
valuableskillsbutalsotogetstudentsinterestedinandexcitedaboutcomputersciencedefensivecompetitionsareoftenlaboriousaffairsandcomedowntorunningchecklistsan
dexecutingconfigscriptsoffenseontheotherhandisheavilyfocusedonexplorationandimprovisationandoftenhaselementsofplaywebelieveacompetitiontouchingontheoffen
siveelementsofcomputersecurityisthereforeabettervehiclefortechevangelismtostudentsinamericanhighschoolsfurtherwebelievethatanunderstandingofoffensivetech
nizuesisessentialformountinganeffectivedefenseandthatthetoolsandconfigurationfocusencounteredindefensivecompetitionsdoesnotleadstudentstoknowtheirenemyas
effectivelyasteachingthemtoactivelythinklikeanattackerpicoctfisanoffensivelyorientedhighschoolcomputersecuritycompetitionthatseekstogenerateinterestincom
puterscienceamonghighschoolersteachingthemenoughaboutcomputersecuritytopizuetheircuriositymotivatingthemtoexploreontheirownandenablingthemtobetterdefendt
heirmachinestheflagispicoCTF{N6R4M_4N41Y515_15_73D10U5_6CDAEA76}
Therefore, the flag is,
picoCTF{N6R4M_4N41Y515_15_73D10U5_6CDAEA76}
transposition-trial
The challenge is the following,
We are also given the file message.txt which contains,
heTfl g as iicpCTo{7F4NRP051N5_16_35P3X51N3_VC85A020}E
It tells us that every block of 3 got scrambled, so I rearranged each block of 3 by hand,
Therefore, the flag is,
picoCTF{7R4N5P051N6_15_3XP3N51V3_5C82A0E0}
Vigenere
The challenge is the following,
We are also given the file cipher.txt which contains,
rgnoDVD{O0NU_WQ3_G1G3O3T3_A1AH3S_a23a13a5}
I went to CyberChef and used Vigenere decode with the key CYLAB, which gave,
Therefore, the flag is,
picoCTF{D0NT_US3_V1G3N3R3_C1PH3R_y23c13p5}
200 points
diffie-hellman
The challenge is the following,
We are also given the file message.txt which contains,
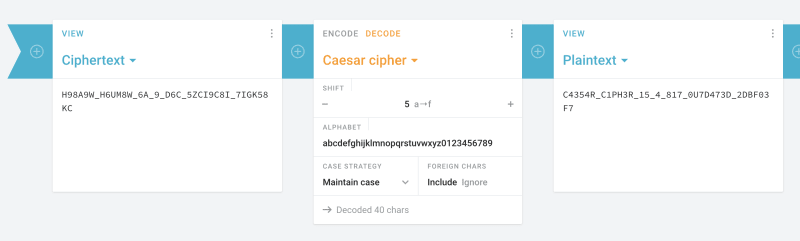
H98A9W_H6UM8W_6A_9_D6C_5ZCI9C8I_7IGK58KC
I figured out that the shift used for the Caesar cipher is 5, so I went to Cryptii's Caesar Decoder, and used a shift of 5 with the alphabet,
abcdefghijklmnopqrstuvwxyz0123456789
Which gave me,
Therefore, the flag is,
picoCTF{C4354R_C1PH3R_15_4_817_0U7D473D_2DBF03F7}


























Top comments (0)