This weekend I participated in VishwaCTF 2022 organised by VIIT Cyber Cell between 3/19(Sat) 19:30 ~ 3/21(Mon) 19:30 GMT+9.
This blog post contains the writeups for the challenges I solved, and I will go into detail about how I solved them.
Table of Contents
OSINT
Platypus Perry (500 points)
This challenge was an emotional rollercoaster, where I experienced the downs of multiple incorrect submissions and the highs of being the first to solve the challenge.
The challenge is the following,
Here, we are given the file Hire-me.mp3.
The challenge description says Agent John got some information that a group of people hid a bag of LSD on a dog. He needs to find the dog before it reaches the dealer., which is a pretty ambiguous challenge description but tells us that we should be looking for a dog.
When I listened to Hire-me.mp3, I couldn't make out anything meaningful, so I opened it up on Audacity.
It sounded like it was in reverse, so I reversed the audio and amplified it.
This processed audio file can be found in Hire-me-rev.mp3.
I listened to the audio and wrote down the letters, which gave me,
nierbrustiushcihwgnihtemosulletthgimlabmobdivadyugruo
Since the audio was in reverse, I assumed this text might also be in reverse, so I went ahead and reversed the text,
ourguydavidbombalmighttellusomethingwhichsuitsurbrein
And I added spaces to the text,
our guy david bombal might tell u something which suits ur brein
Now we know the next step would involve David Bombal, who is a well-known guy in the infosec community and has a lot of websites and accounts associated with him.
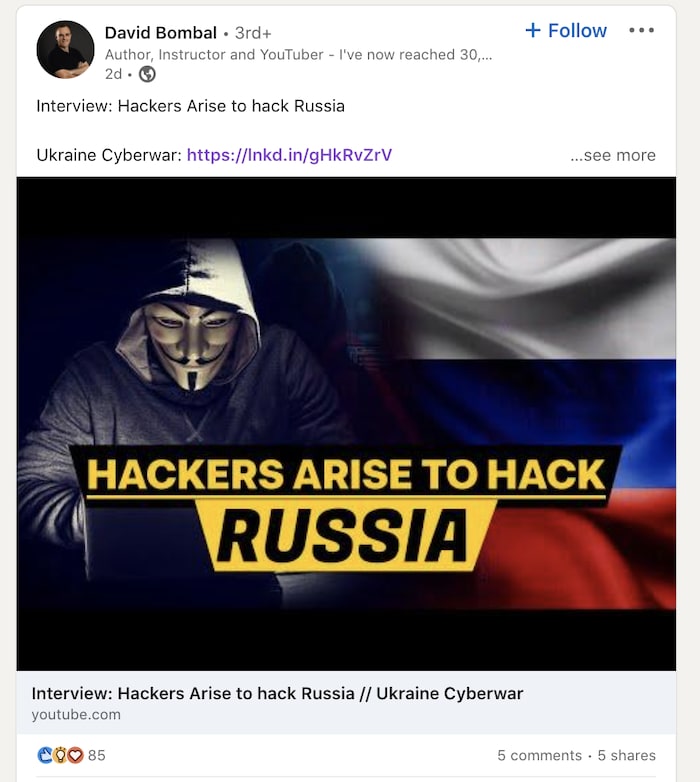
The hint in the challenge says Hint : David is Linked IN with some "Russian Hacks", which hints to looking up his LinkedIn, and find something related to Russian Hacks.
His LinkedIn looks like the following,
If we look closely, there is indeed a post related to Russian Hacks.
And in the comments, I saw the following comment.
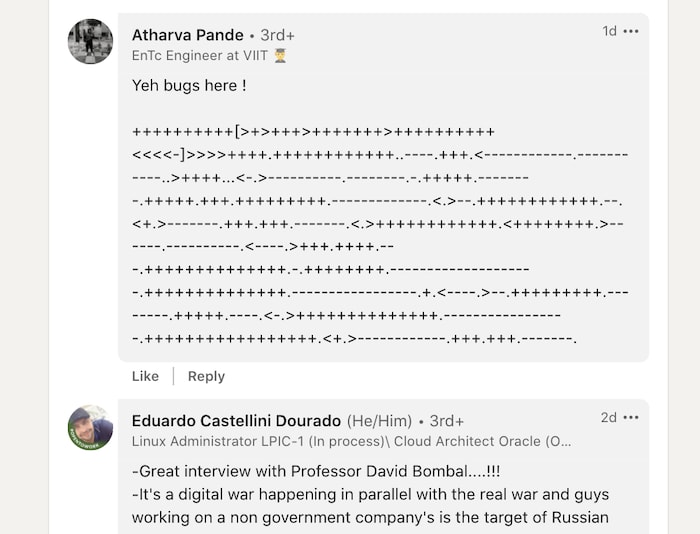
I went ahead and checked Atharva Pande's LinkedIn,
This person was from Vishwakarma Institute of Information Technology, which is a gold sponsor for VishwaCTF so I assumed the comment this person made was one of the clues to this challenge.
I isolated the cipher-like section of Atharva Pande's comment, and put it into brainfk.txt
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++++.++++++++++++..----.+++.<------------.-----------..>++++...<-.>----------.--------.-.+++++.--------.+++++.+++.+++++++++.-------------.<.>--.++++++++++++.--.<+.>-------.+++.+++.-------.<.>++++++++++++.<++++++++.>------.----------.<----.>+++.++++.---.++++++++++++++.-.++++++++.--------------------.++++++++++++++.-----------------.+.<----.>--.+++++++++.--------.+++++.----.<-.>++++++++++++++.-----------------.+++++++++++++++++.<+.>------------.+++.+++.-------.
I wasn't exactly sure what type of cipher it was using, so I copied and pasted it into Google to get some hints.
So apparently, it was using Brain F*ck, so I went ahead to a Brain F*ck Decoder.
Decoding this gave me the following URL,
https://www.mediafire.com/file/q7ka3dhesrzftcd/bkchd.rar/file
Accessing this Media Fire Link gave me the following,
I went ahead and downloaded bkchd.rar, but unfortunately, it was password protected.
I tried to crack this .rar file using John the Ripper. A couple of hours passed, but no password candidate was found.
At this time, a new hint was added,
Now I know that the password length is 5 characters, which drastically reduces the brute-forcing time.
So I downloaded rockyou.txt from here, unzipped it, and isolated all the 5 character passwords into rock5.txt with,
$ grep -E '^.{5}$' rockyou.txt > rock5.txt
So now I just needed to use rock5.txt as the wordlist for John the Ripper.
I went ahead and made the hash using
$ sudo rar2john bkchd.rar > rarhash
And crack with John using rock5.txt as the wordlist,
$ john --wordlist=rock5.txt rarhash
After a few minutes, John has found the password, which is
idgaf
I went ahead and opened bkchd.rar with the password idgaf, and inside was the following picture.
I checked for steganographic messages using Steganography Online
,
As shown above, some text was contained in this image, which I put into decodedsteg.txt.
this ( guy's pet love dem fries, thats your final pin@ @ @@@ @@ D @ @ @ @@@@ @ @@ @@@ @@ @ @ @ @ @@ @@ @@ @@@@@@@ @ @ @ @ @ @ @ H @ @@ @@ @@@@ @@ @@@ @ @@@@
I didn't know what this was supposed to mean and assumed it was saying that this guy's pet, more specifically, the dog is what we're supposed to look for.
So I did a reverse image on Google using bkchd.png.
However, nothing much came up except for other men with tattoos. So I went Yandex to do a reverse image search.
By looking for his distinctive beard and tattoo through the reverse image search results, I noticed that most of them had the name Polish Viking on them, so I assumed that was his nickname.

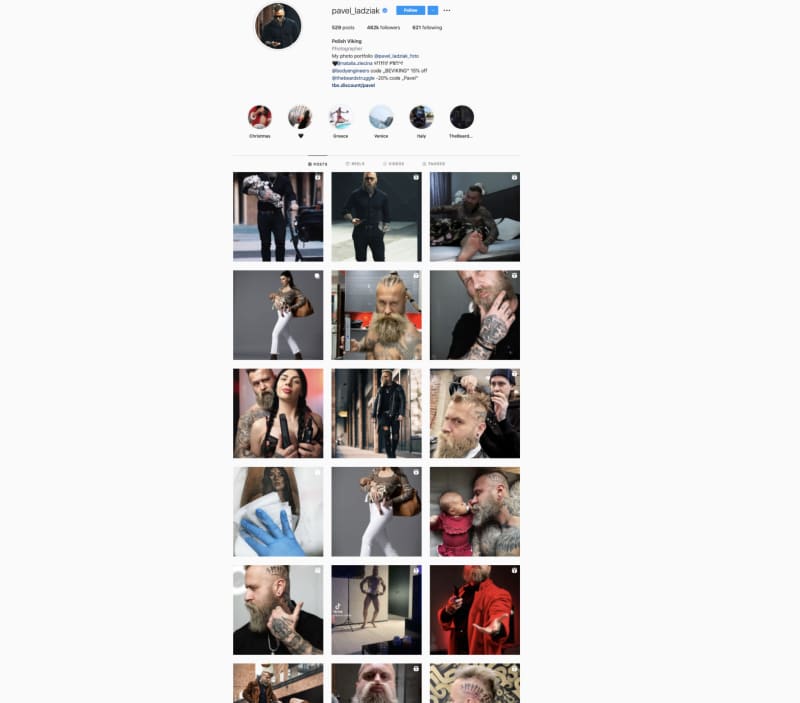
So I looked up Polish Viking,
and found his Instagram and name, which was pavel_ladziak.
I went to Google and changed the language settings to Polish to get the most out of the results, and looked up pavel ladziak dog, which showed me that his dog was a toy dog with white and beige coloration.
I dug through his Instagram, and found a few pictures with his dog,
However, I could not find the name of his dog. I was thinking to look through his followings list to find his dog, but I assumed that his wife might be more likely to tag their dog in the pictures.
So I went ahead to his wife's account.
So I dug through her pictures with their dog in it, and came across this picture.
I saw that she tagged her dog in that picture, which has the Instagram username iamthemisio
I went to the dog's account and saw the following,
The dog's name is Misio Zdzisio, and as the challenge was to find a dog and the flag format was vishwaCTF{Firstname_Lastname}, the flag for this challenge would be,
vishwaCTF{Misio_Zdzisio}
I cried tears of joy when I inputted this flag and finally got correct, because I failed multiple times with flags like vishwaCTF{David_Bombal}, vishwaCTF{Atharva_Pande} and vishwaCTF{Pavel_Ladziak}.
This challenge was an emotional rollercoaster. Every time I thought I got the flag, it turns out it wasn't the flag, but rather only a step in obtaining the flag. Thus, finally getting correct was extremely satisfying, especially because I was the first to solve the challenge.
I experienced an important life lesson while doing this challenge, which is to keep trying even if you fail because those failures will lead your way to success.
The Library (449 points)
The challenge is the following,
And we are given two images files Howtodm.jpg and Troubleshoot.jpg.
The challenge mentions Note : The attached files are NOT hints or steps to the challenge, they are guides to message the bot and troubleshooting., so we know that these are simply instruction pictures.
I DMed Hello to the The Librarian, and gave me the following reply,
So now I need to use OSINT to find the answer to Tommy is to call on Miss Glen at what time?. I searched this into Google,
and the top-most result is this Partners in Crime Wikipedia. Since this bot was called The Librarian, I automatically assumed that I am supposed to look for things related to fiction, so this Partners in Crime by Agatha Christie was the most likely candidate for the answer.
I saw that Tommy is one of the main characters, and searching this name on the Wikipedia page returned many results.
To narrow it down, I searched for Miss Glen, and found out that she only appears in The Man in the Mist.
Also, the only time that is mentioned in The Man in the Mist was 6.10 pm, therefore I assumed this would be the answer. The bot said to Give me the time in 12 hr format (HH:MM) (without am/pm), so I tried patterns like 6:10 and 06:10. Turns out 06:10 was the correct answer.
The bot gave the next question, and when I saw Son of Neptune, I immediately assumed that it was related to Rick Riordan because I read a lot of Percy Jackson in my childhood and knew that the protagonist, Percy Jackson is the son of Greek god Poseidon, who is referred to as Neptune in Roman mythology.
And searching this title up on Wikipedia has confirmed my assumption.
The question mentions He is also acknowledged in mythology to guide a voyage to retrieve what?, with an emphasis on the what, so I assumed that we're supposed to look for the object Percy Jackson has retrieved in his quests.
I went ahead to Riordan Fandom site about Percy Jackson's Quests, and saw that there were multiple objects that Percy Jackson had to retrieve.
The bot didn't say anything specific about the object, so I decided to try each possible object like master bolt, golden fleece, flying chariot, etc. from the Riordan Fandom site about Percy Jackson's Quests.
As the bot responded to golden fleece, that was the answer to this question. For the next question, the bot mentions In this classic, the names of the creation and creator are often confused.. I immediately assumed that the bot was talking about Frankenstein, because I remember in literature class that the English teacher always talked about how "Frankenstein is not the name of the monster, but it's the name of the creator, who is Victor Frankenstein."
The bot says Give me the name of the university where the creator studied, so I assumed that I was supposed to look for the university where Victor Frankenstein studied. I opened up Victor Frankenstein on Wikipedia, and searched university. There were multiple instances of the string university in this Wikipedia article, and I saw that the History section of the article was the most relevant.
I tried various patterns like university at Ingolstadt, ingolstadt, ingolstadt university and University of Ingolstadt, and turns out University of Ingolstadt was the correct answer.
The bot then gave me the following image.
Also, the bot only asks us What is the name of the dragon?.
As it mentions dragon, I assumed that this would be related to fantasy fiction. So I went to Google images and searched fantasy language. Among the results, I found a text similar to the one the bot gave us,
By digging deeper into the similar images section, I found out that this language was called Cirth, which is a script of runes created by Daeron from Lord of the Rings. I found a translation sheet here,
And I went ahead and translated half of the text by hand,
STAND BY THE GREY STONE HWEN THE THRVSH KNOCKS AND THE SETTING SUN
At this point, I decided to input this text to Google and see if it can auto-complete it for me.
Therefore, the full decoded text should be
Stand by the grey stone when the thrush knocks, and the setting sun with the last light of Durin's Day will shine upon the key-hole
I couldn't find anything related to dragons from this text, so I decided to look up dragons in lord of the rings instead, and came across the Tolkien Wiki page about Dragons.
I didn't know which dragon, so I decided to try them all,
Therefore, smaug was the answer to this question. Now for the final question, the following images were given.
I know that this is a Pigpen Cipher, and deciphering the first picture would give,
NISYTETPRISTNUFO
However, the bot did not respond to that, so I thought the second image might contain more information. I did a reverse image search, and the webpage for the Architect of the Capitol came up.
So apparently, this architecture was called the Rotunda. The bot says These Symbols might make you feel pretty Lost, but not as much as a severed hand right in the before the image. Thus, I decided to look up severed hand in rotunda on Google, and the first result, which was a Wikipedia page on The Lost Symbol looked pretty relevant as it says Solomon's severed right hand in the middle of the Capitol Rotunda. Also because the bot capitalizes Symbols, I knew this was referring to The Lost Symbol.
So I looked up the lost symbol cipher on Google, and saw that most of them had the keyword magic squares in them.
I looked up the lost symbol cipher magic squares, and came across this website that talks in detail about the cipher used in the book. I saw that the Pig-pen part was correct, but the cipher used in The Lost Symbol uses one additional step, which was the magic square.
So I went ahead and arranged NISYTETPRISTNUFO into a 4x4 square,
And I rearranged the letters as shown in the website.
The rearranged text would be,
OSINTISPRETTYFUN
Which makes sense, so I went ahead and sent this text to the bot,
Therefore, the flag is,
vishwaCTF{b00ks_d0_b3_1nt3r3st1ng!}
Rocket Raccoon (286 points)
The challenge is the following,
We are given the username racckoonn, so I started by looking up this name on InstantUsername,
I went ahead and started with racckoonn's Instagram
I looked through their pictures, and found this image.
So I went to the https://www.youtube.com/channel/UCDurVPcUypifNkJVrHxJ3vQ,
However, there are no videos. So I assumed that I will have to use the username JohnsonM3llisa for further investigation. I went to InstantUsername again, and looked that username up.
I went ahead and started with JohnsonM3llisa's Twitter.
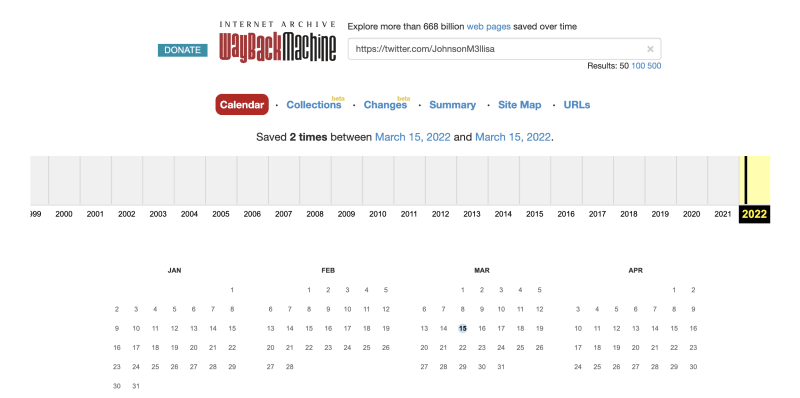
This tweet caught my eye, and I immediately assumed that I was supposed to use the Wayback Machine to look at the deleted Tweets.
So I went ahead and searched their Twitter account on the Wayback Machine, and saw that there were snapshots on March 15, 2022.
I opened up the snapshot on March 15, 2022, and saw the following,
Therefore, the flag is,
Vishwactf{R4cc00ns_4r3_Sm4rt}
Misc
I don't need sleep, I need answers (418 points)
The challenge is the following,
The challenge asks Discord profile pictures are circular. But are they?, so I assumed that we are supposed to investigate the The Librarian's Discord profile picture. Also, it tells us to refer to The Library challenge, which the write-up be found here. . So I opened up Discord on Chrome, because I assumed this challenge will require us to use Inspect element. I right-clicked on The Librarian's profile icon to select Profile.
Clicking Profile showed the following,
I then went to Inspect elements, and found the source of the profile picture which was,
https://cdn.discordapp.com/avatars/953173381962948618/1b83941f7abbdfa15344f485e0c39677.webp?size=240
Opening this up showed the following,
I saw that the flag was in the corners of the profile picture, but couldn't make out the words due to its low resolution. So, I changed size=240 to size=480 which revealed the flag,
Therefore, the flag is,
vishwaCTF{h3h3_sn3akyy}
Forensics
So Forgetful! (250 points)
The challenge is the following,
And we are given the file Ghost.pcap. I used tcp.stream in the filters, and looked at the packets. Packet 112, which uses HTTP caught my attention because it uses POST. I looked into that packet and saw the following,
I went to Export Objects > HTTP and selected packet 112,
And I saved it as a .txt text file, which contained,
userid=spiveyp&pswrd=S04xWjZQWFZ5OQ%3D%3D
I couldn't find anything information related to the website where these credentials were used, and the challenge didn't specify any server to log in to. Therefore, I assumed that the password S04xWjZQWFZ5OQ%3D%3D itself would be the flag (after processing it more). The %3D%3D at the end of the flag looked like Base64 in URL,
So I converted it to the standard Base64 format by replacing %3d with =, to give,
S04xWjZQWFZ5OQ==
Finally, I went to CyberChef to convert it from Base64, which gave,
KN1Z6PXVy9
Therefore, I assumed that this would be the flag,
vishaCTF{KN1Z6PXVy9}
And submitting it confirmed that this was the flag.
The Last Jedi (250 points)
The challenge is the following,
And we are given Y0D4.jpg,
First of all, I decided to check the contents of this file by using,
$ cat Y0D4.jpg
The last section showed Sacred archives/Dont open/Is_This_Really_It.jpg, so I knew there was a file hidden inside Y0D4.jpg.
So I used Stegextract on Y0D4.jpg, and it extracted a Y0D4.rar file.
Y0D4.rar was not password protected, and showed the following folders and files,
Is_This_Really_It.jpg was a contained in Y0D4.rar,
So I ran Stegextract on Is_This_Really_It.jpg, and it extracted a ASCII text file that contained the string flag:{H1DD3N_M34N1NG}.
Therefore, the flag is
vishwaCTF{H1DD3N_M34N1NG}
Cryptography
John the Rocker (250 points)
The challenge is the following,
And we are given idrsa.id_rsa.docx. I tried opening this on Word, but gave me the following error,
So I converted this to a .txt file and put it into idrsa.id_rsa.txt. After converting it to a .txt file, the contents were visible,
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,115D424076ADCE7E40ACC1E44E4E791A
flkT1+aCoQZ4YBHg2VRW3x4HzlEKFwqQ+ePMzEi2BIREHXDtHR1+QUrYRSQLzP4E
jDSkmPWPoTvTXRAyXKrQL8FzkvYDcP9hjkzt41tjsRHz2nkI9K+WFm8DNi6qVS9H
J/yWZdvUED6XwwxTFe6D01GwU7yc7xheE4GlIBazk68Q0tNuH34H8T+hnfkTyNA6
BJL861zNhZNIoWm/352vYydnT/HynugCGn+TIu88C+tLBpcLdLSh50OgTiZ8QK2A
Z82PoPfD1ziVmg7E4BIY1/1qJnNxCMTzUG4PbjLpdkRxHu5aOGzbGZK4K0inDNfr
B7ZedUOCSUTN0VGl5/spDO506vSOjzGL9/iDhYNBRvn4hW3VlPE6nRXAQ78r4Z49
ou0r2x7WvzrpFOPXjvlNHUFyWF9x5ZWsqNnr3PFL2wlCVvGq2z/mWvFdmy0tr6nV
FjEpOwrKMt0hvTcCwry8FKAyPDFafpZq4fg90Jd9xCYWJIZMxuEPOY0jfcSC7QOy
woOhMMCFA3mbJJWOAOKynZdx/7fe/0+Q0XMlljDNXNGNqKRqS9OUhKH967FYxw4W
AQHrN2NdT5WoXJhbDu67Z2jb89LAFR+uBlaxauLSYEFatKmAp/IXR4yTX4yn6Ur2
mlrJ6abOjmi+/LcvMN+qCx7pB//MR2HUxcOWdgA5nuXiYBdiSKj8h0Sq3IVVjDFd
Oj1t0D9m6AUsV32qbiXwiiCkOOMHVZH+6sc1ZMKNwR1WGvFBNyR0DVxlXAzyR7zP
nRUXCLihj696lm+Ywe6xsDOPJMl4RHOAvf+cj3fkI3WKhfhTUhoLrEZmIFDNhKrn
JCe4m9p+aNuPSuXL07bxKbYT6D4wlVE4OlkwZyAfc5R/cfE5JYFgwoIW5RJC9nh1
ru/aBj+464986pteEfI0e3nAuDquEvs37Oxv77n/AdW7QmySIb7RrpUfOCcq+rBt
4zg1cS5i2TX1l25h036E45Rn+efM9QBKQEChhgqfLZ9rbQqqm1coOok4sZZ1tWap
7352duKI9fzMq35P9u4T168sYSvZoa2hK7eZZ3KA/MK8u6B1yFiB1E2rEZGnVeOU
KLt1IFxygxZl9yO5yb4pa8tl6yKO46+OYmCe9ie7FkOEeq85a0xm0OB3HVxL/40/
116u2fJCRoDBjNZ1J4ujYwYUpWEfVoN26KRRiyRMJbHX9QwuW6k+b1OjLgjU2IaR
4BgG6xBTmM3fRQZhWbJ+06ibWDcIRdZOP02iksp/LdJtqtuYIWf2epUx3oBMrSN/
bFDUmLDzfSUCvz4MdZNp8FE1ElM2NK9PWYPe3XA5lzjkl9jxWD7M4WKLTjQJu9P0
PB4x+nHPj5j6XONZ74IbM1f7S4oRuhBCs5hPMgxDr7xSa0ROFsTauCeQ6N22JwIk
GzMpmzBzJtL5/SzFCuN148sMUOASnXLSYd79dB15M0nVRo6Iz9mytF/QVuci+8h+
6luGQBgih+L5ghx1qvUXwNyU+Id9fZYRA8pH2hy5pPWVsaws/1cLOc5PBzOaql7G
90iM4IyzSN2AO8/6HnSJ9tZSCG5cdRq+r1ROF30QnvnUowsbq0eeT4TVfb+kCaHx
-----END RSA PRIVATE KEY-----
Therefore, this was a RSA private key and I assumed the objective was to crack this RSA private key. Also, the name of the challenge was John the Rocker, so I assumed that this was a reference to John the Ripper and I had to use John the Ripper to crack the RSA private key.
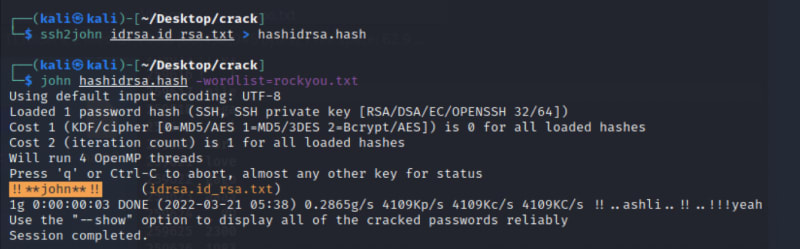
I first made the hash file of idrsa.id_rsa.txt using,
$ ssh2john idrsa.id_rsa.txt > hashidrsa.hash
Then specified rockyou.txt as the wordlist using,
$ john hashidrsa.hash -wordlist=rockyou.txt
After a few minutes, John the Ripper found the password, which was !!**john**!!
The challenge didn't have any further instructions, so I assumed that the flag would be,
vishaCTF{!!**john**!!}
and submitting it confirmed that this was the flag.
Final thoughts
Some of the problems were quite challenging (especially Platypus Perry), but I really enjoyed doing them as I learnt many new things from them. I'd like to thank the organisers of VishwaCTF for organising this CTF and giving me the opportunity to learn many new things!
The original writeup and their corresponding files can be found on my Github

















































































Latest comments (0)