Introduction
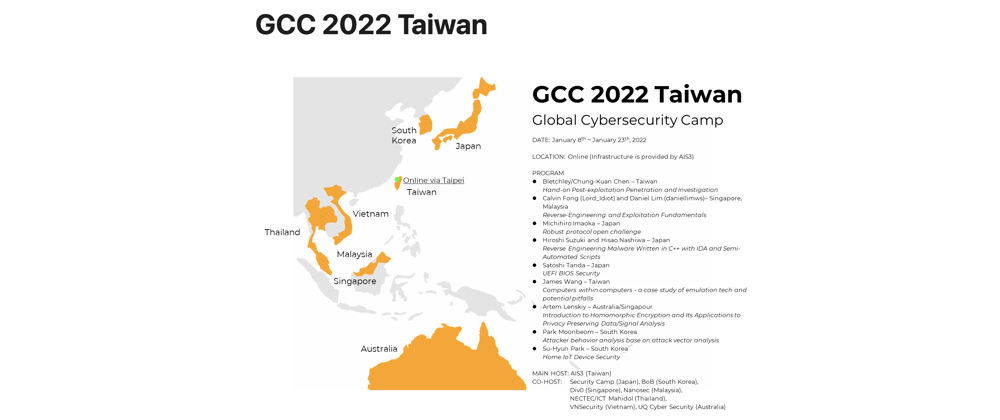
Global Cybersecurity Camp (GCC) is an annual cybersecurity event where security communities and passionate students across Asia participate. This year's GCC 2022 Taiwan went on between 8/1/2022 ~ 23/1/2022. This post is about GCC 2022 Taiwan's Group Work Progress and Outcome.
Mission of GCC
Strengthen the security community across Asia and nurture future global leaders. Annually, the best 48 students (maximum) from member countries gather in one of the participating countries for a week to exchange experience, forge a life-long friendship, and learn from the best cybersecurity professionals.
Group Work
Group Work is part of the GCC program, and went on throughout the course of GCC. Each group was composed of around 9 students and a tutor.
I tutored the Japanese programs and the Group Work for GCC 2022 Taiwan, and documented the progress and outcome of Group 1's Group Work in this post.
This post is broken up into five sections. The first section, Brainstorming, looks into the thought and brainstorming process of our group project. The second section, Investigating our research topic, looks into the investigation process of our project after deciding our research topic. The third section, Putting everything together, looks into the process of putting our ideas and research together to create the presentation. The fourth section, Post-GCC, looks into the outcomes of the GCC group work, and how the group work has allowed us to form long lasting bonds. The final section, Conclusion, gives the concluding remarks of the group work.
Table of contents
Brainstorming
January 8, 2022
In the first meeting, we did a self-introduction and shared our interests. We also elected our leaders. Students in this group had a diverse range of interests, ranging from VR, cryptography, Bluetooth, etc. We looked at possible topics, which include:
Students showed interest in Log4J, ECC, and Bluetooth. However, other groups were planning to do a topic in Log4J, so we decided to remove Log4J from our possible topics. We wanted to do a topic that could integrate everyone’s interests, so we decided on IoT.
However, IoT is a very vast topic so we had to narrow it down. We decided to conduct a vote to see what everyone’s interests were based on the layers. The lower layer indicates the hardware, etc. the middle layer indicates the OS, etc. and the high layer indicates the user applications, etc.
From the vote, we saw that the majority of the students were interested in the higher layer. We conducted another vote to see if students were interested in particular areas of information security, which include Cloud, Bluetooth, and Man in the middle.
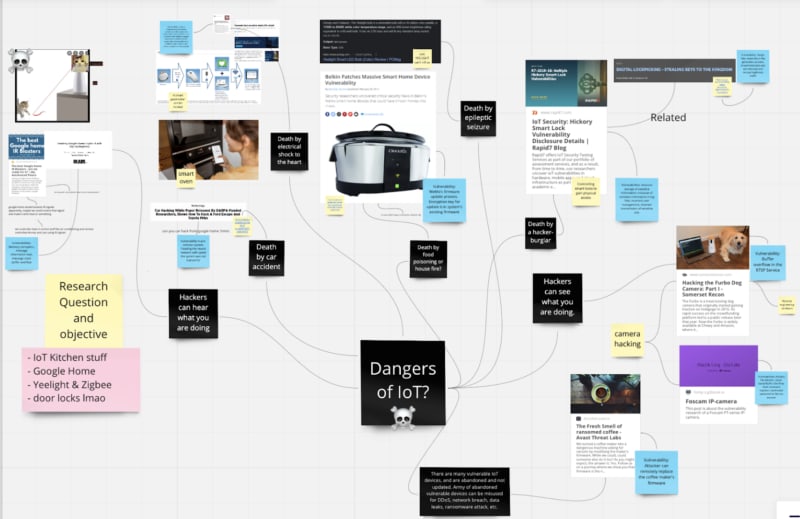
Because the meeting time was limited, we decided to create a Miro board so students can share their ideas at their convenience.
January 10, 2022
Students have investigated the topics related to IoT and added ideas and related articles to the Miro board. These include:
- BlueBorne
- TEE
- Encryption between the cloud and IoT device
- XML, SQL injection
- Amazon Alexa’s vulnerabilities
- Remote code execution on IP camera firmware
January 12, 2022
During this meeting, students filled the Miro board with ideas, related articles and made connections to each other's ideas. Some of the ideas include:
- Hacking IoT smart bulbs such as Yeelight
- Running custom code on a Google Home Mini
- Hacking routers & IoT devices with Routersploit
- Breaking Google Home with SQLite
- Zigbee
- Searching for victims on Shodan
We conducted another vote to see which layers of IoT we might want to focus on.
Additionally, we have created another vote to see which articles and ideas we found the most interesting. Many of the students showed interest in Google Home and Yeelight due to the possibility that an attacker can disturb or damage someone physically. We came up with example scenarios, like how an attacker can play a certain frequency and decibel of sound to damage the victim, and flash the lightbulb on and off to cause disturbance to the victim.
Many of the students were interested in the real-life implications of a compromised IoT device, so we decided to narrow down our topic to “IoT devices and real-life implications: How IoT home devices can kill you”. We conducted a vote to finalize our topic decision.
Initially, we came up with the idea of demonstrating the exploit on IoT devices. However, we thought this would be difficult because everyone was far apart, and we would not be able to get the vulnerable IoT devices in time. Therefore, we decided to go with an investigation-based topic, as this will allow everyone to contribute even if we were all physically apart. In the end, we decided to investigate IoT security from online resources and find out how they can cause real-life damage and possibly kill someone.
We found the vulnerabilities for each IoT device and added them to the Miro board to investigate further.
Investigating our research topic
January 13, 2022
We voted on whether to do “one device, in-depth research” or “many devices, surface research”.
Based on this vote, we decided to research shallow and wide. Thus we decided to pick three devices, where three students would be responsible for one of the three devices. This way students can contribute equally and apply their knowledge and interests.
Through our investigation, we found out that IoT devices can be easily hacked, but killing someone with one was more difficult than we initially thought. For example, we thought a compromised pacemaker could deliver a deadly electrical shock to the victim and instantly kill them but discovered that it was not feasible as it requires physical tampering. Therefore, we decided to focus more on the indirect ways the IoT devices can kill a victim.
We decided to update our title to “How IoT Home Devices can ruin your life and ultimately kill you”.
The group members for each device were randomly selected, with volunteers taking up the role of Intro & Outro and the General Preventative measure.
Every member listed their top 3 choices for their devices. We finalized our decisions to Cookware, Smart Lock, and Pacemaker.
We decided that each of the students would do research at their convenience. To stay consistent with our topic “How IoT Home Devices can ruin your life and ultimately kill you”, we decided to channel our research efforts to the following:
January 20, 2022
Before the meeting, everyone had gathered information about their selected devices and added them to the Miro board. During this meeting, each student made connections to each other's research and gave comments and feedback to one another.
For the cookware, students have investigated the following in-depth:
-
The WeMo kitchenware
- Overview: WeMo manages various IoT devices, ranging from light switches, security cameras, and smart kitchenware.
- Vulnerabilities: Private key used for future encryption hardcoded in the firmware, and firmware update does not validate SSL certificate of central server which makes it vulnerable to MITM attacks.
- Real-life implications: The attacker could manipulate the temperature which can cause a fire and kill the victim.
-
Coffee Maker
- Overview: Smart coffee maker that can be controlled through an app connected by Wi-Fi.
- Vulnerabilities: Uses a simple binary protocol with almost no encryption, authorization or authentication. Malicious firmware can be put into the coffee maker.
- Real-life implications: Annoyance and injury caused by boiling water splashing at the victim.
For the SmartLock, students have investigated the following in-depth:
- Overview: A smart lock that can be locked / unlocked using a smartphone app.
- Vulnerabilities: Log files that may include sensitive information are accessible without rooting the device.
- Possible mitigations: Integration of Android Keystore system or Apple’s keychain services to securely store data, encryption of app data, frequent purging of temporarily stored data, etc.
- Real-life implications: Attackers can break into your home and steal even more personal data and hardware devices. The victim can also be physically harmed.
For the PaceMaker, students have investigated the following in-depth:
- Overview: The IoT pacemaker helps control heartbeats in patients with arrhythmia by sending an electric pulse upon anomaly detection. The pacemaker uses a Home Monitoring Unit (HMU) that connects it to the vendor server, where the data can be viewed remotely by doctors.
- Vulnerabilities: The CardioMessenger II-S HMU manufactured by BIOTRONIK has several vulnerabilities, including improper authentication that does not properly enforce mutual authentication with the BIOTRONIK Remote communication infrastructure, cleartext transmission of sensitive information, missing encryption of sensitive data, storing passwords in a recoverable format. Researchers were also able to set a breakpoint before the encryption to find the key.
- Possible attack scenario: The attacker can access the JTAG to the device, or dump the memory to get the device's key to intercept and decrypt the communication between the pacemaker and the HMU.
- Real-life implications: Attackers can impersonate the doctor or patient, and prevent/modify communication between each other which can lead to the patient's death.
For the general preventative measures, students have investigated the following:
- What the consumer can do: Update, patch, don’t buy devices that don’t have active development and support, disconnect devices from the internet when not in use, use an IoT security box like Bitdefender Box, restrict physical access to devices to prevent tampering, and use strong passwords.
Putting everything together
January 21, 2022
For the presentation time, we decided to allocate 1 minute to the introduction, 9 minutes to each device, 1 minute to the general preventive measures, and 1 minute to the conclusion. We decided that each student would speak for around 3 minutes in the presentation.
Students had finished writing the script, and we provided feedback on each other’s script.
After we had finished writing the script, we had fun coming up with crazy and creative ways how IoT devices can kill the victim.
We have conducted a vote to decide the primary color of the slides’ theme. The majority of the students voted on the purple and navy theme, so we have decided to go with the navy theme.
After finishing the slides, we had a cosplay party at GatherTown. We challenged ourselves to see if we can cosplay our favorite anime and game characters using the limited color and dress options on GatherTown. We found out that pink and orange were not available on Gather, which made it difficult to cosplay as certain characters.
January 22, 2022
We finalized our slides and rehearsed our presentation. Our presentation was 30 minutes, and every student had the chance to speak for at least 3 minutes.
We also gave each other some feedback regarding the presentation rehearsal,
January 23, 2022
Before the Group Work final presentation, we decided to do another round of rehearsals. This time, we overcame all the problems we faced in the last rehearsal.
In the final presentation, we were all able to hear each other clearly, the transition was smooth, and we were able to showcase our work and convey our passion to the audience. The Q&A session gave students the opportunity to discover and propose new solutions to the current IoT security problem.
Post-GCC
Having fun on GatherTown
After GCC ended, we decided to make a Discord group with all group 1 members + other group members.
We all gathered for a group picture, and we dressed up as Mario characters using the following recipe on Gather.
We took pictures in various locations around the GCC GatherTown. Here’s a picture of everyone in the park,
Here’s a picture of everyone gathering around the dining table,
Here’s a picture of everyone gathering around the fountain,
Here’s a picture of everyone dancing on top of the building that imitates Taipei 101 inside Gather,
Here’s a picture of everyone dancing in the garden’s bushes,
We have organized another group picture meeting, and organized a GatherTown chase game using an Arduino BadUSB keystroke injector which made avatars move and dance randomly. The objective of this group picture time was for everyone to surround the randomly moving avatar and take a group picture. The difficulty was increased by including the “G” key in the random movements, which made the avatar walk through people so it cannot be trapped forever.

A BadUSB that isn't so bad: Making a keystroke injector in Arduino that automates GatherTown movements
Lena ・ Feb 7 '22
In 2 hours, students have successfully trapped the avatar multiple times and taken pictures by surrounding it from all four directions, driving it into narrow alleyways, and cornering it with bushes and other objects.
By playing around GatherTown, we found that GatherTown could be a bit glitchy sometimes and people can walk through walls given the right circumstances, and thus developed GatherTown “cheats”.
CTF participation and projects
Group members have participated in the AIS3 EOF Final CTF and worked together on Discord. We also exchange CTF information, share write-ups, and teach each other.
Language practice sessions
We organized weekly English + Japanese casual discussion sessions on Discord to practice our English and Japanese speaking skills. We also help translate and teach languages to each other.
Casual discussions and games
Students have casual discussions with each other, such as what they are interested in, what they want to do in the future, etc. Students also play games together.
Culture exchange
Some students were considering studying or working in places where other students were located. We regularly exchange information such as university exchange programs, environment and culture, as well as tips for living in another country. We also frequently share pictures of interesting things we find in our location.
Sharing experience and information
We share various information, ranging from cybersecurity career experiences, academic experiences, internship information, projects, cybersecurity events, etc.
Conclusion
In conclusion, this group work was extremely successful, where everybody was able to contribute, have their opinions heard, and have their interests integrated into the project. This team’s greatest strength was strong communication and teamwork, where everyone’s opinions were heard and everyone was able to contribute equally. Additionally, the Miro Board has allowed everyone to freely express their ideas and allowed students to make connections and build on each other’s ideas.
We all had a lot of fun during the group work, such as coming up with creative ways IoT devices can kill a victim, doing cosplay parties on GatherTown, and exploring areas and playing around in Gather. With all the picture-taking throughout the Gather chasing game, we were all able to appreciate the details and work that was put into GCC 2022 Taiwan GatherTown.
Finally, one of the greatest outcomes of this group project was the bond that the group members formed, and we continue to inspire each other after GCC ended. We continue to participate in activities, teach each other, and share information and experiences. In the 6 months after GCC, participants started cybersecurity jobs and internships, pursued exchange programs, studied languages, participated in events, and more.



























































Top comments (0)