In this guide, I'll walk you through setting up ALB authentication at a high level, demonstrating how you can leverage this serverless approach to handle user login flows. This solution can significantly streamline your authentication implementation.
Unlock the Hidden Power of Application Load Balancer Authentication
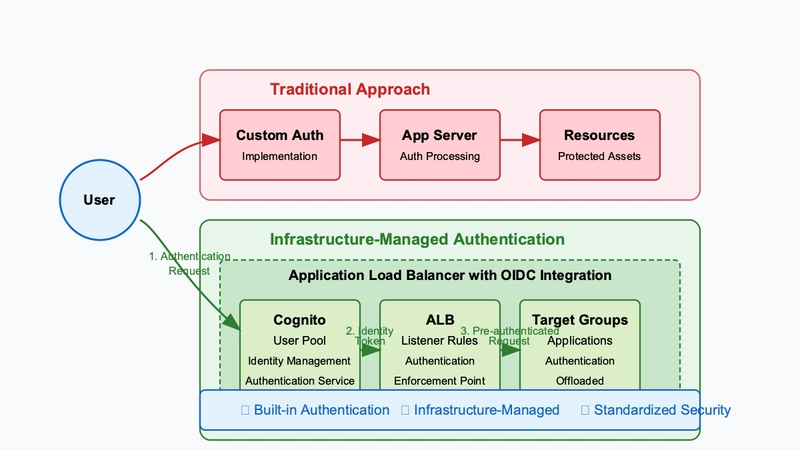
While many developers overlook a game-changing security feature, AWS Application Load Balancers (ALBs) harbor a secret weapon: native OpenID Connect (OIDC) authentication. This lesser-known capability transforms authentication from a complex, resource-draining challenge into a streamlined, efficient solution that operates directly at the infrastructure level.
By enabling OIDC authentication at the load balancer, you can offload critical authentication work from your application servers, reducing complexity, minimizing potential security vulnerabilities, and delivering a more robust authentication strategy with minimal additional configuration.
Benefits
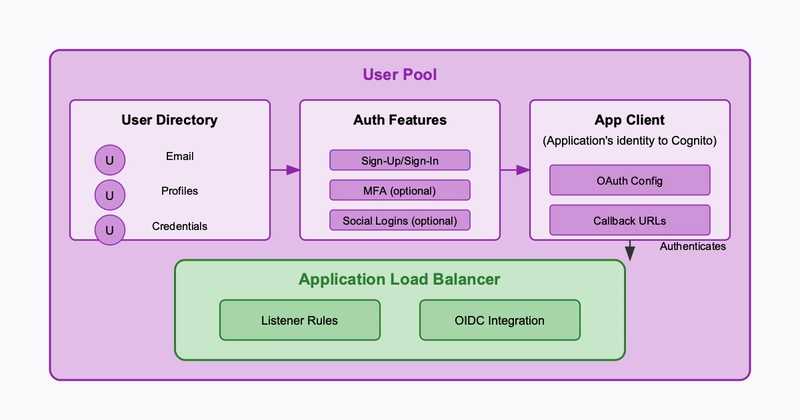
✅ Application Load Balancer acts as an OIDC Relying Party (RP) that provides authentication backend with seamless integration with AWS Cognito, public IdP (such as Facebook, Google) and corporate identities using SAML, LDAP, Microsoft AD, or OIDC
✅ Offloading the responsibility of authentication to the Application Load Balancer, while benefiting from its scale, availability, and reliability.
✅ Cost-Effectiveness: Managed authentication reduces the need for custom solutions, saving time and resources on development and maintenance.
How it works
📌 OIDC client is implemented in ALB via configured listener rules that simplifies authorization in the backends
📌 Cognito User Pool Domain serves as the OIDC Provider (OP), hosting the authorization server endpoints
Limitations
⚠️ Cookie Size Restrictions:
The session cookies used by ALB have size limitations (maximum 4KB). if token payloads exceed this limit (e.g., larger than 11KB), the load balancer may return errors like HTTP 500.
⚠️ Dependency on Publicly Resolvable DNS:
For OIDC-compliant IdPs, the OIDC Provider's endpoints must be publicly resolvable even if they resolve to private IPs, which may not be feasible in certain private network setups.
⚠️ No Custom Login Pages:
Applications relying on ALB for authentication must use the login page hosted by the IdP (e.g., Amazon Cognito). Customization of the login UI may be limited.
⚠️ Complex Configuration for Multiple Applications:
When supporting multiple applications via a single ALB, developers must configure unique session cookies and listener rules to avoid conflicts between client authentications
Design Overview
Configuration Components
1. DNS and SSL Configuration
- Create CNAME record in your domain registrar:
- Record: app.[your-domain].com
- Target: [your-load-balancer-dns-name].region.elb.amazonaws.com
- Request SSL certificate in AWS Certificate Manager (ACM):
- Domain name: app.[your-domain].com
- Validation: DNS validation recommended
2. Amazon Cognito Configuration
User Pool Setup
- User Pool Name: [Your Application Name]-user-pool
- Domain: [your-domain].auth.[region].amazoncognito.com
- App client:
- Name: of your choice
- Generate client secret:
Yes - Allowed OAuth Flows:
Authorization code grant - Allowed OAuth Scopes:
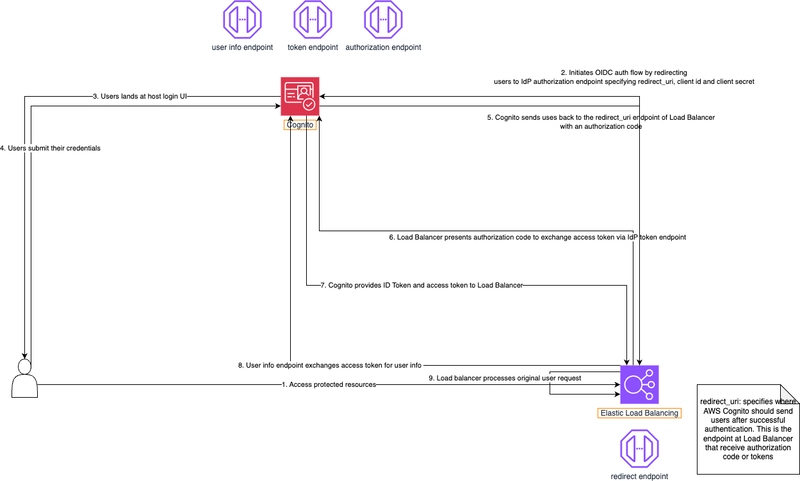
openid, email, profile - Callback URLs: https://[your-load-balancer-domain]/oauth2/idpresponse and https://[your-domain]/oauth2/idpresponse (this is an ALB-specific endpoint required for the OIDC authentication flow)
3. Application Load Balancer Configuration
Our Application Load Balancer is configured with two listeners:
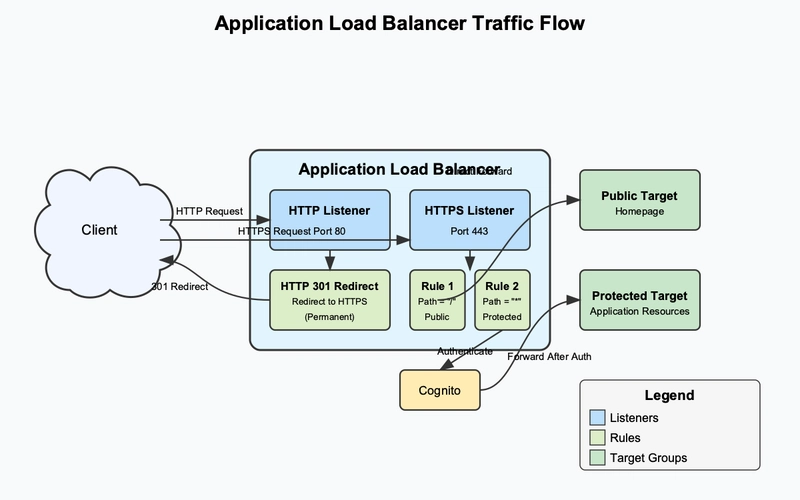
HTTP Listener (Port 80)
- Rule Configuration: Redirects all HTTP traffic to HTTPS (port 443)
- Status Code: HTTP 301 (Permanent Redirect)
- Security Purpose: Ensures all authentication traffic is encrypted
HTTPS Listener (Port 443)
Configuration: Serve HTTPS traffic as path routing, handles authentication through AWS Cognito before routing to downstream applications depending on different listener rules
This listener has two distinct rules that handle different access patterns:
-
Public Resource Rule (Priority: 1)
- Path Pattern: Exact match for root path "/"
- Actions: Direct forward to target group without authentication
- Purpose: Allows public access to the homepage without requiring authentication
-
Protected Resources Rule (Default Rule)
- Path Pattern: All other paths not explicitly matched by other rules
-
Actions: Configured in the following order:
- authenticate-cognito (Order: 1): Authenticates users via Cognito before allowing access. We need to specify Cognito User Pool, User Pool Domain, App Client and include TLS/SSL Certificate here.
- forward (Order: 2): Forwards authenticated requests to the target group
- Purpose: Protects all application resources by requiring authentication


Top comments (3)
It is so usefull, thank you so much.
Yes with built-in capabilities in Authentication of Application Load Balancer, we don't have to worry about authenticating users at Application level
Your article is very helpful, thank you