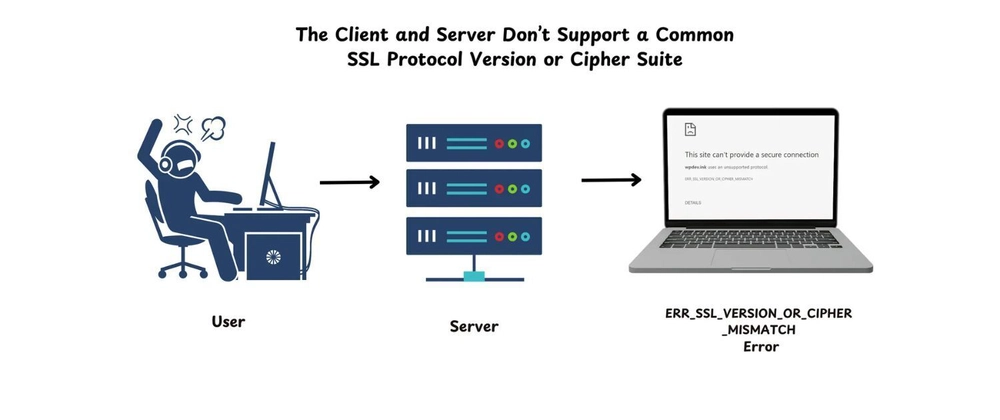
One of the most frustrating SSL/TLS-related issues users and developers encounter is the error: “The client and server don’t support a common SSL protocol version or cipher suite.” This message typically appears when the browser (or any client) and the server fail to establish a secure communication channel due to incompatible encryption protocols or cipher suites.
What Does This Error Mean?
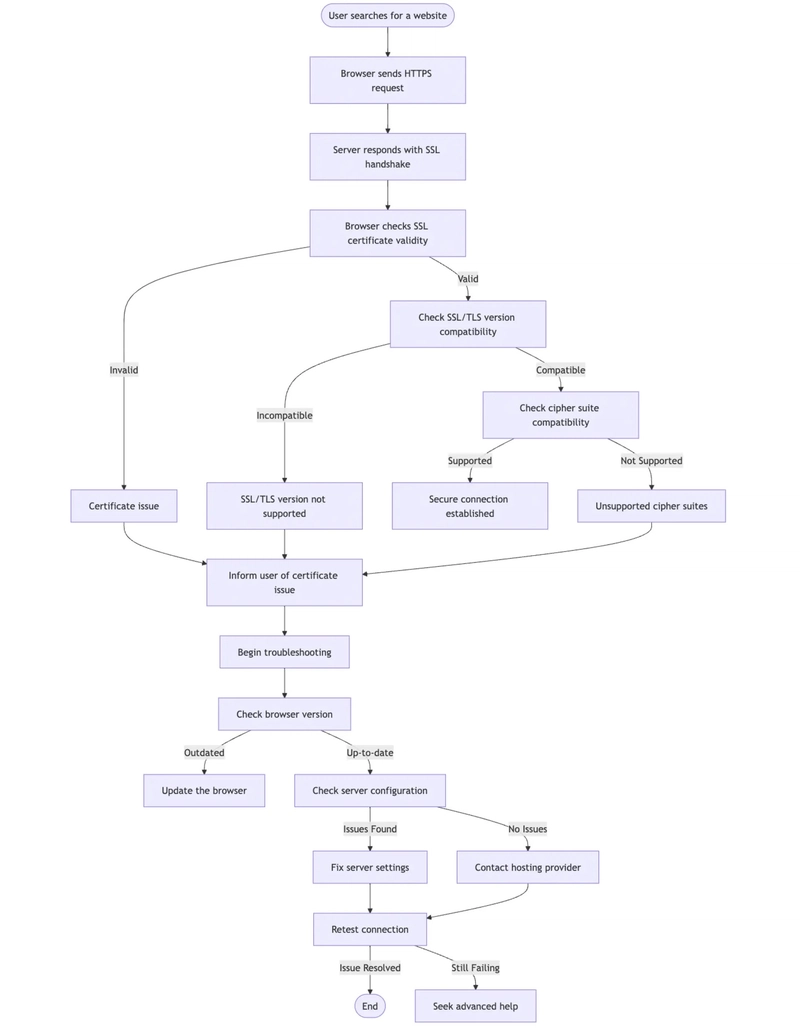
The Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), are cryptographic protocols that ensure privacy and data integrity between two communicating applications, typically a browser and a web server. The SSL/TLS handshake is the initial step during which both the client and server agree on a protocol version and cipher suite for encryption. When there's no mutual agreement on these, the connection fails, triggering this error.
The core of this issue lies in protocol mismatch (e.g., client supports TLS 1.2, the server only supports TLS 1.0) or unsupported/disabled cipher suites.
For Website Visitors: Understanding the Problem
Visitors typically encounter this error due to one or more of the following reasons:
1. Outdated Browser
Older browsers lack support for modern encryption protocols like TLS 1.2 or 1.3. Browsers such as Internet Explorer 8 or early versions of Safari/Firefox often trigger these issues.
2. Unsupported Protocols
Modern servers may restrict access to legacy protocols like SSL 3.0 or TLS 1.0 for security reasons. If the client attempts to use these, the handshake fails.
3. Incorrect System Date/Time
SSL certificates are time-bound. If a device has an incorrect date or time, even a valid certificate may appear invalid.
4. VPN or Proxy Interference
Certain VPNs or proxies modify connection parameters, potentially stripping secure protocols or interfering with the handshake process.
5. Cached SSL Data
Stale cache or stored cookies might include outdated or incompatible security settings.
How Website Visitors Can Fix It
- Update the browser to the latest version supporting TLS 1.2 and 1.3.
- Sync device time/date with an internet time server.
- Clear cache and cookies to eliminate outdated certificate/session data.
- Temporarily disable VPN or proxy, then retry the connection.
- Switch browsers or devices to test if the issue is isolated.
For Website Owners: Digging Into the Cause
This error is an indication that the server is either:
- Using deprecated protocols.
- Offering weak or outdated cipher suites.
- Missing proper certificate chaining.
- Running outdated server software (e.g., OpenSSL).
Common Technical Causes
Deprecated Protocols Enabled
Support for SSL 3.0, TLS 1.0, and TLS 1.1 has been dropped by modern browsers.Weak Cipher Suites
Algorithms like RC4, MD5, and DES are no longer considered secure. These must be removed.Certificate Chain Errors
Missing intermediate certificates or using self-signed certificates can block trust establishment.Server Software Misconfiguration
Running outdated versions of Apache, NGINX, or OpenSSL can limit supported encryption features.
How Website Owners Can Fix It
-
Enable only TLS 1.2 and 1.3
- Apache:
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1- NGINX:
ssl_protocols TLSv1.2 TLSv1.3; -
Use strong ciphers:
- NGINX example:
ssl_ciphers HIGH:!aNULL:!MD5; Install and verify SSL certificates, including intermediate CAs.
Test your setup with SSL Labs to uncover weaknesses.
Update server software to versions supporting TLS 1.3 and secure cipher sets.
Preventive Measures
- Conduct regular SSL/TLS audits using tools like SSL Labs.
- Automate certificate renewals using Certbot or similar tools.
- Keep server software updated to the latest stable versions.
- Implement HSTS headers to enforce HTTPS-only communication:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
Pinggy's Role in Testing and Troubleshooting This Error
While Pinggy is primarily known for exposing local services to the internet, it also offers an effective way to test SSL/TLS configurations during development or debugging. Developers can run a secure service locally, configure it with various SSL/TLS protocols and cipher settings, and expose it via Pinggy. This setup allows them to test how clients (e.g., browsers or tools like curl) negotiate protocols and ciphers in a realistic yet controlled environment. Such use cases are valuable for reproducing SSL handshake failures, experimenting with security configurations, and validating fixes before deploying to production.
Conclusion
The error “The client and server don’t support a common SSL protocol version or cipher suite” serves as a reminder that internet security is a moving target. As attackers evolve, so too must our defensive protocols. Website visitors and administrators alike should remain vigilant in ensuring their systems are up-to-date, compliant with modern standards, and tested regularly. Tools like Pinggy can assist during testing phases by simulating realistic network conditions, making SSL/TLS debugging more efficient and accessible.


Top comments (0)