Insecure Direct Object References (IDOR) vulnerabilities are a serious yet common security risk in web applications, including those built on Symfony. If not properly mitigated, IDOR can allow attackers to access sensitive data by manipulating object references like IDs in the URL or request.
In this article, we’ll explore how IDOR vulnerabilities occur in Symfony, walk through real-world coding examples, and show how you can easily detect such issues using our free website security scanner tool.
🔍 What is an IDOR Vulnerability?
IDOR is a type of access control flaw that occurs when an application exposes a reference to an internal implementation object—like a file, database record, or key—without proper authorization checks. An attacker can manipulate these references to access unauthorized data.
Example of an IDOR attack:
GET /user/12345/profile
If changing the ID to /user/12346/profile exposes another user's data, that’s a classic IDOR vulnerability.
🚨 Common Causes of IDOR in Symfony
Symfony applications can become vulnerable to IDOR when:
- Authorization checks are missing or incorrectly implemented.
- URL or POST parameters are directly used to access resources.
- The system trusts user input without verification.
Let’s break this down with coding examples.
🧪 Coding Example: Vulnerable Symfony Controller
Here’s a vulnerable implementation of a controller in Symfony:
// src/Controller/ProfileController.php
use Symfony\Bundle\FrameworkBundle\Controller\AbstractController;
use Symfony\Component\HttpFoundation\Response;
use Symfony\Component\Routing\Annotation\Route;
class ProfileController extends AbstractController
{
#[Route('/profile/{userId}', name: 'user_profile')]
public function show(int $userId): Response
{
$user = $this->getDoctrine()->getRepository(User::class)->find($userId);
return $this->render('profile/show.html.twig', [
'user' => $user,
]);
}
}
This controller renders the profile of any user based on the ID in the URL. There are no access control checks—any authenticated or even unauthenticated user could guess another user's ID.
✅ Secure Version: Fixing the IDOR
You should always verify that the currently logged-in user is allowed to access the requested resource.
Here’s a safer approach:
// src/Controller/ProfileController.php
use Symfony\Component\Security\Core\Security;
class ProfileController extends AbstractController
{
#[Route('/profile', name: 'user_profile')]
public function show(Security $security): Response
{
$user = $security->getUser(); // Get the currently logged-in user
return $this->render('profile/show.html.twig', [
'user' => $user,
]);
}
}
In this version, the profile route doesn’t accept a user ID in the URL. It fetches the authenticated user directly, mitigating any chance of IDOR.
🛡️ Detecting IDOR Using Our Free Security Tool
Want to quickly test your website for IDOR and other vulnerabilities? Try our free website vulnerability scanner online:
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
Just enter your URL and let the scanner check for common issues like IDOR, XSS, CSRF, and more. It provides detailed results and remediation steps.
📄 Sample Vulnerability Report
Here's a screenshot of a vulnerability assessment report generated by our tool after detecting an IDOR issue in a test Symfony app to check Website Vulnerability:
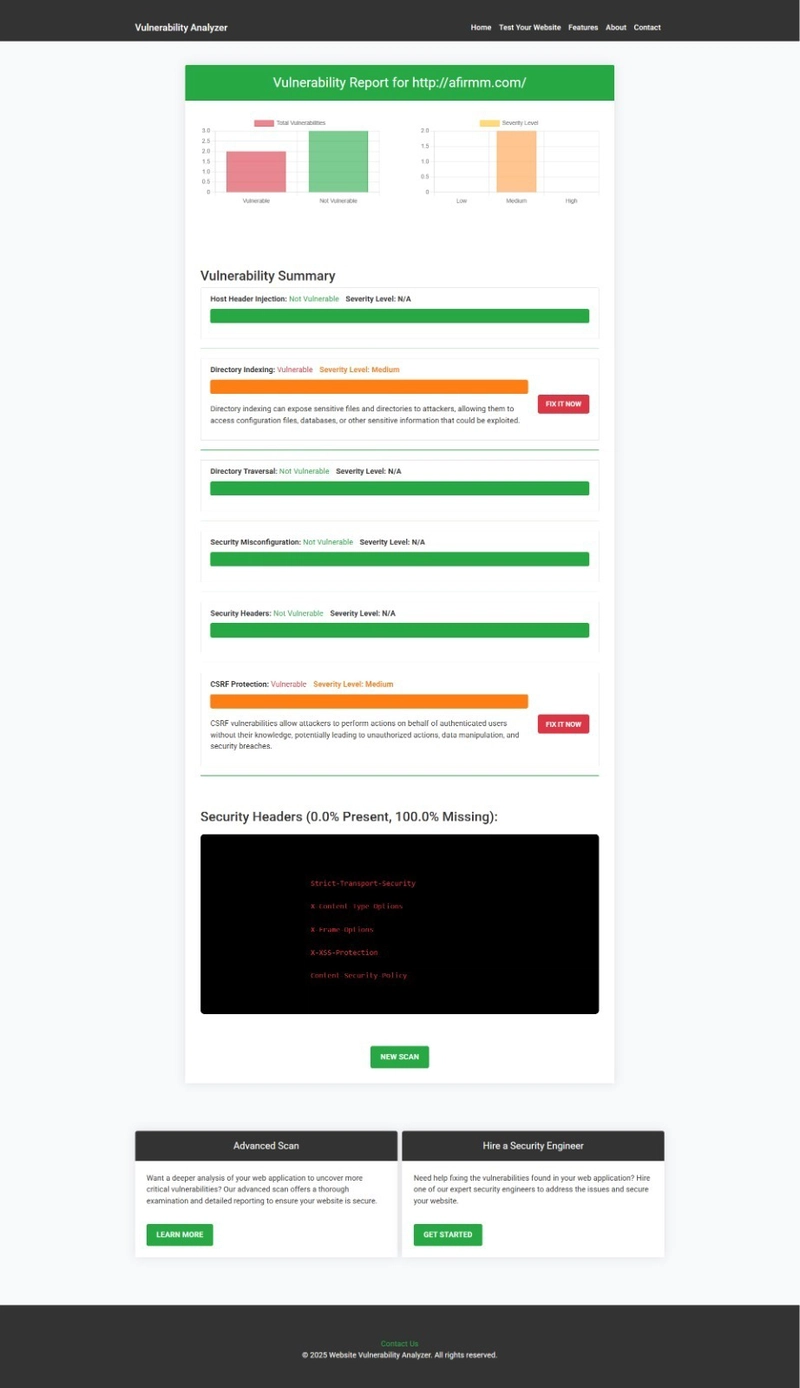 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
The report includes the affected URLs, severity levels, and recommended fixes—making it easy for developers to Website security check and address the problem quickly.
🧰 More Secure Coding Practices in Symfony
Here are a few more coding tips to prevent IDOR in Symfony:
1. Always Use Security Voters or Access Control
$this->denyAccessUnlessGranted('view', $user);
Symfony provides a built-in method for granular permission checking using voters. Implement voters to validate if a user has access to the object.
2. Avoid Passing User IDs in URLs
Instead of:
GET /orders/9876
Use:
#[Route('/my-orders', name: 'my_orders')]
Then fetch orders associated with the logged-in user in the controller.
3. Enforce Strict API Validation
If you're building APIs with Symfony, validate object ownership in the controller:
if ($order->getUser() !== $this->getUser()) {
throw $this->createAccessDeniedException();
}
Never trust incoming IDs without verifying ownership or access rights.
📢 Final Thoughts
IDOR vulnerabilities are deceptively simple but can lead to major security breaches. If you're using Symfony, ensure that your code follows strong access control rules and doesn't expose internal references carelessly.
Use automated tools like our website vulnerability scanner to catch these flaws early and protect your web applications effectively.
🔗 Want More Security Tips?
Check out our latest posts on secure coding and vulnerability analysis on our official blog at Pentest Testing Corp.
Stay secure. Stay smart. 🚀




Top comments (0)