Introduction: Understanding Cross-Site Scripting (XSS) in Symfony
Cross-Site Scripting (XSS) is a widespread vulnerability in web applications that can be exploited by attackers to inject malicious scripts into web pages. In a Symfony application, if user inputs are not sanitized properly, they could lead to XSS attacks, compromising the security of your website.
This blog will guide you through the prevention of XSS in Symfony, highlighting practical coding examples and best practices. We will also demonstrate how our Website Vulnerability Scanner can help identify such vulnerabilities in your Symfony application.
What is Cross-Site Scripting (XSS)?
XSS attacks occur when an attacker injects malicious scripts into web pages viewed by other users. These scripts can steal cookies, session tokens, or redirect users to malicious websites. The three main types of XSS are:
- Stored XSS: Malicious scripts are stored on the server and then served to users.
- Reflected XSS: Malicious scripts are reflected off a web server, typically via query parameters.
- DOM-based XSS: Malicious scripts are executed due to the way a client-side script modifies the DOM.
In Symfony, like any other PHP framework, XSS vulnerabilities can arise if input is not validated or escaped properly before being rendered on a page.
Identifying XSS Vulnerabilities in Symfony
To identify XSS vulnerabilities in your Symfony application, you can use our Free Website Security Checker. This tool scans your website for XSS and other security risks, offering a detailed vulnerability report.
Example: Using Symfony’s Built-in Escaping Mechanism
In Symfony, it’s crucial to escape user inputs before rendering them in the template. Symfony provides the |escape Twig filter to help with this.
Here’s an example of unsafe user input handling in Symfony:
// Controller code
public function index(Request $request)
{
$name = $request->query->get('name');
return $this->render('home/index.html.twig', ['name' => $name]);
}
If the user provides malicious input, such as <script>alert('XSS')</script>, it will be executed when the page is loaded.
To prevent this, use Symfony's |escape filter in the Twig template:
<!-- Safe handling of user input -->
<h1>Hello {{ name|escape }}</h1>
This ensures that the input is escaped before being displayed, preventing malicious scripts from running.
Best Practices to Prevent XSS in Symfony
1. Use Symfony’s Twig Escaping by Default
Ensure that all dynamic content rendered in Twig templates is escaped. Symfony's default behavior escapes output, but it’s important to explicitly apply escaping where necessary.
2. Validate User Input
Always validate and sanitize user input. Symfony’s Validator component can be used to ensure that inputs conform to expected formats.
use Symfony\Component\Validator\Validation;
use Symfony\Component\Validator\Constraints as Assert;
$validator = Validation::createValidator();
$violations = $validator->validate($input, [
new Assert\NotBlank(),
new Assert\Length(['min' => 5])
]);
if (count($violations) > 0) {
// Handle validation errors
}
3. Use Content Security Policy (CSP)
Implement a Content Security Policy to add an extra layer of protection. CSP helps prevent the execution of malicious scripts from untrusted sources.
Example of a CSP header in Symfony:
# In config/packages/security.yaml
security:
firewalls:
main:
http_headers:
content_security_policy:
default-src: 'self'
script-src: 'self' 'https://trusted.cdn.com'
Testing for XSS with Our Free Security Tool
To ensure your Symfony application is secure from XSS and other vulnerabilities, regularly scan your website using our free tool to test Website Security. This tool automatically identifies common security issues, including XSS, and provides a detailed vulnerability report.
Example Screenshot of our Security Scan tool:
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
Conclusion: Safeguard Your Symfony Application
XSS is a dangerous vulnerability, but with proper input validation, escaping, and security measures, you can safeguard your Symfony application. Using Symfony's built-in features like Twig escaping and integrating a strong CSP header can significantly reduce the risk of XSS attacks.
If you want to make sure your website is free of XSS vulnerabilities, use our Free Website Security Scanner to scan your application and receive an instant vulnerability assessment.
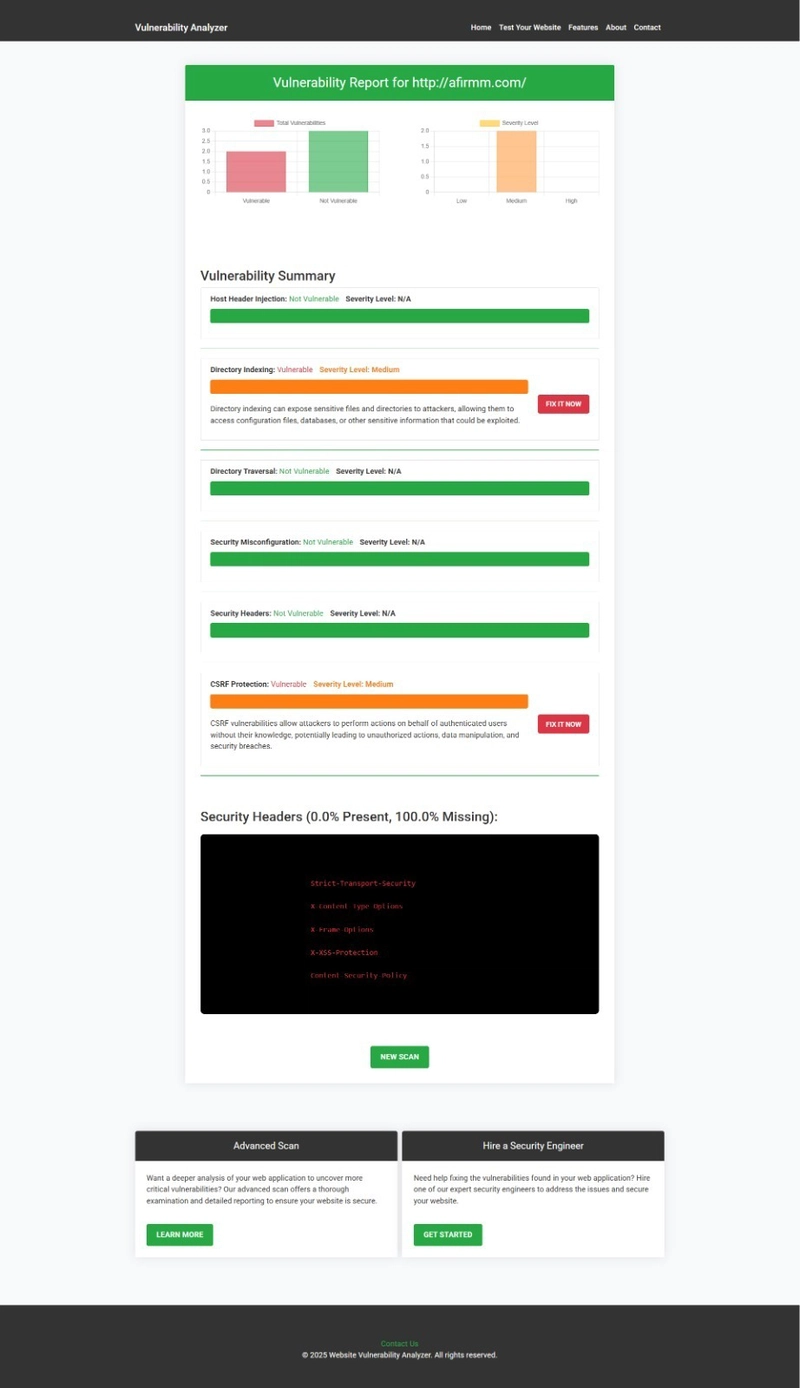 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
For more tips on securing your web applications, visit our blog at Pentest Testing Corp..




Top comments (2)
Great guide on preventing XSS in Symfony! Escaping user input and implementing CSP are indeed crucial steps.
On my macOS setup, I use ServBay to manage PHP environments, which simplifies testing various security configurations in Symfony projects.
Thank you for the kind words and for sharing your setup! 🙌
ServBay on macOS sounds like a solid choice for managing PHP environments—glad to hear it's helping streamline your Symfony security testing. If you ever test out additional security headers or use custom bundles for XSS protection, we'd love to hear about it! Stay secure and keep sharing your insights. 😊