Welcome back, tech explorers! 🚀
I’m glad to have you here as we continue our exciting journey through the world of computer networking. If you haven’t checked out the previous blogs in this series—where we explored the Physical, Data Link, and Network layers—I highly recommend giving them a read. They’ll help you build a solid foundation before diving into today’s topic.
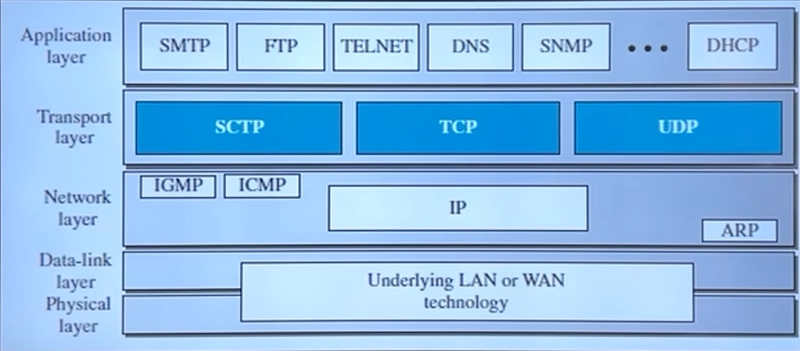
Now, let’s move one step higher in the networking hierarchy and uncover the magic of the Transport Layer—the unsung hero ensuring smooth and reliable communication between devices. Let’s get started! 🎯
Introduction
Imagine you’re sending a package to a friend in another city. You carefully pack it, choose between a reliable courier service (which guarantees delivery with tracking) or a faster, no-tracking option, and label it with the correct address. The transport layer in networking works in a similar way—it ensures that data sent from one device reaches the right application on another device, either reliably or quickly, depending on the need.
Key Functions of the Transport Layer
Segmentation & Reassembly (Breaking down data into smaller packets and reassembling them).
Flow Control (Preventing data overload using mechanisms like sliding window).
Error Control (Ensuring data integrity through acknowledgments and retransmissions).
Multiplexing & Demultiplexing (Managing multiple communication sessions).
How Does It Work?
When an application sends data, the transport layer divides it into smaller units called segments (in TCP) or datagrams (in UDP). Each segment is labeled with a source port number and a destination port number, so the receiver knows which application should process the data.
Protocols of the Transport Layer
The two main protocols in this layer are:
- TCP (Transmission Control Protocol) – A reliable, connection-oriented protocol that guarantees data delivery with error checking, acknowledgments, and retransmissions if needed. Think of it like a courier service with tracking.
- UDP (User Datagram Protocol) – A fast, connectionless protocol that sends data without guarantees. It’s useful for time-sensitive applications like gaming and streaming. Think of it like sending a postcard—quick but no guarantee it’ll arrive safely.
Ports & Port Numbers
Every computer has multiple applications running at the same time—so how does the transport layer know where to send the data? That’s where port numbers come in. A port is like a specific door in a building that directs incoming data to the right application. For example:
- Port 80 – Used for HTTP (web browsing)
- Port 443 – Used for HTTPS (secure web browsing)
- Port 25 – Used for email (SMTP)
We are done with introduction part, I think i described everything in concise format now let's discuss everything in detail.
Transport layer protocol
Transmission Control Protocol (TCP) – Reliable & Connection-Oriented
TCP is like a well-organized courier service that guarantees your package (data) will reach its destination correctly and in order. It establishes a connection between sender and receiver before transmitting data, making sure that the communication is reliable and accurate.
Key Features of TCP:
- Connection-Oriented – A connection is established before sending data (via a process called the three-way handshake).
- Reliable Delivery – Ensures that all data reaches the destination correctly. If a packet is lost, TCP retransmits it.
- Error Checking – Uses checksums to detect errors in transmission.
- Ordered Data Transfer – TCP numbers each packet so they arrive in the correct order.
- Flow Control – Prevents overwhelming the receiver by adjusting the speed of data transmission.
- Congestion Control – Regulates data flow to avoid network congestion.
How TCP Works?
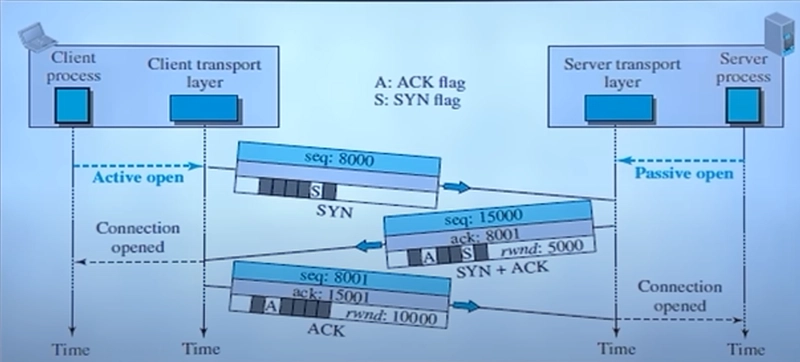
1 Connection Establishment (Three-Way Handshake)
The sender sends a SYN request to initiate communication.
The receiver responds with SYN-ACK to acknowledge the request.
The sender replies with ACK, and the connection is established.
2 Data Transmission
TCP segments are sent in sequence, and each segment is acknowledged by the receiver.
If a segment is lost, TCP retransmits it.
3 Connection Termination
When communication is done, the sender and receiver exchange FIN (Finish) and ACK packets to close the connection.
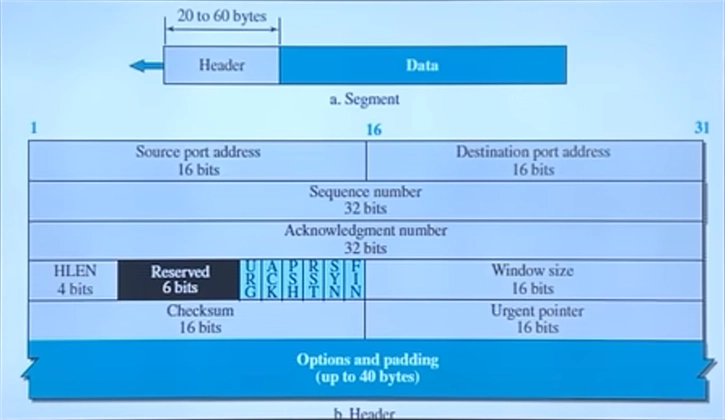
TCP Header
When data is transmitted using TCP, it is broken into segments, and each segment contains a TCP header. This header provides important control information that ensures reliable and ordered delivery of data.
The TCP header is typically 20 to 60 bytes long and contains the following fields:
Source Port & Destination Port – These ensure the data is sent to the correct application. For example, a web server may use port 80 (HTTP), while an email server may use port 25 (SMTP).
Sequence Number – TCP assigns each byte of data a sequence number, ensuring that data is reassembled correctly at the receiver’s end.
Acknowledgment Number – This field confirms receipt of data. If a sender sends data with sequence number 1000, the receiver will reply with acknowledgment 1001, meaning it expects the next byte to start from 1001.
Flags (Control Bits) – Used to manage the connection:
SYN – Used in connection establishment (Three-Way Handshake).
ACK – Acknowledges received data.
FIN – Used to terminate a connection.
RST – Resets the connection.
URG – Indicates urgent data.
PSH – Instructs to send data immediately.
Window Size – Controls flow control by specifying how much data can be sent before requiring an acknowledgment.
Checksum – Used for error detection to ensure data integrity.
Urgent Pointer – If the URG flag is set, this field tells the receiver which part of the data is urgent.
Use Cases of TCP:
- Web Browsing (HTTP/HTTPS) – Ensures webpages load completely and correctly.
- Email (SMTP, IMAP, POP3) – Guarantees reliable delivery of emails.
- File Transfer (FTP) – Ensures error-free transmission of files.
User Datagram Protocol (UDP) – Fast & Connectionless
UDP is like sending a regular letter without tracking—it delivers data quickly but does not guarantee that all packets will arrive. It does not establish a connection before sending data, making it much faster than TCP.
Key Features of UDP:
- Connectionless Communication – No need to establish a connection before sending data.
- Fast & Lightweight – Less overhead compared to TCP.
- No Error Checking or Retransmission – Lost packets are not resent.
- Unordered Data Transfer – Packets may arrive out of order.
How UDP Works?
- The sender transmits data packets (datagrams) to the receiver.
- The receiver gets them, but there are no guarantees of order or reliability.
- If a packet is lost, UDP does not request retransmission.
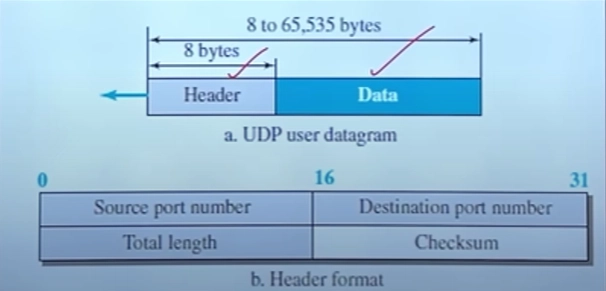
UDP Header
Unlike TCP, UDP (User Datagram Protocol) does not establish a connection before sending data, making it faster but less reliable. The UDP header is fixed at 8 bytes, making it much smaller than the TCP header.
Source Port & Destination Port – Like TCP, these identify the sender and receiver’s applications. For example, a video streaming service might use port 1935 (RTMP), and DNS uses port 53.
Length – Specifies the total length of the UDP packet (header + data). The minimum size is 8 bytes (header only), but it can be larger if data is included.
Checksum – Provides error detection. Unlike TCP, UDP does not request retransmission if errors are found, meaning the data is simply discarded.
Use Cases of UDP:
🔹 Online Gaming – Fast response time is more important than 100% accuracy.
🔹 Live Streaming (YouTube, Netflix, Zoom) – Minor packet loss doesn’t ruin the experience.
🔹 DNS (Domain Name System) – Quick lookups of website addresses need speed, not reliability.
Ports & Sockets
What is a Port?
A port is a logical communication endpoint used by networking protocols to identify specific services running on a device. Just like a house has multiple rooms, a computer has multiple ports to handle different types of network traffic.
Each port is assigned a port number, which is a 16-bit integer (ranging from 0 to 65535). The combination of an IP address and a port number allows a computer to distinguish between different network connections.
Types of Port Numbers
| Port Range | Name | Description |
|---|---|---|
| 0 – 1023 | Well-Known Ports | Reserved for common services like HTTP (80), HTTPS (443), FTP (21), and SMTP (25). |
| 1024 – 49151 | Registered Ports | Used by specific applications like MySQL (3306) and Docker (2375). |
| 49152 – 65535 | Dynamic / Private Ports | Assigned dynamically to temporary connections (e.g., video calls, online gaming). |
Examples of Common Port Numbers:
| Service | Port Number | Protocol |
|---|---|---|
| HTTP (Web Browsing) | 80 | TCP |
| HTTPS (Secure Web Browsing) | 443 | TCP |
| FTP (File Transfer Protocol) | 21 | TCP |
| SSH (Secure Shell) | 22 | TCP |
| DNS (Domain Name System) | 53 | UDP |
| SMTP (Email Sending) | 25 | TCP |
What is a Socket?
A socket is a combination of an IP address and a port number that uniquely identifies a network connection. It acts as an endpoint for sending and receiving data between two devices.
Understanding Socket Address
A socket address is written in the format:
IP Address:Port Number
For example:
-
192.168.1.10:8080Here,
192.168.1.10 → Represents the device’s IP address
8080 → Represents the port number where a service (e.g., a web server) is running
Cryptography: Securing Data in the Transport Layer
In computer networks, cryptography plays a crucial role in ensuring secure communication over the internet. It protects sensitive data from unauthorized access, alteration, or interception.
** What is Cryptography?**
Cryptography is the practice of securing information through encryption and decryption techniques. It ensures confidentiality, integrity, and authenticity in communication.
** Key Goals of Cryptography**
- Confidentiality – Ensures that only the intended recipient can read the data.
- Integrity – Ensures that the data is not altered during transmission.
- Authentication – Verifies the identity of the sender and receiver.
- Non-repudiation – Prevents denial of sending or receiving data.
** Cryptography in the Transport Layer**
At the transport layer, cryptography is implemented using SSL (Secure Sockets Layer) and TLS (Transport Layer Security) to encrypt and secure data during transmission. These protocols prevent eavesdropping and ensure a secure end-to-end connection between devices.
Conclusion
In this blog, we explored the Transport Layer, understanding its core concepts:
✅ Transport Layer Protocols – TCP (reliable) vs. UDP (fast).
✅ TCP & UDP Headers – Structure and role of each field.
✅ Ports & Sockets – How applications communicate using port numbers.
✅ Cryptography – How encryption secures data transmission.
The Transport Layer is the backbone of reliable data communication, ensuring that messages are delivered correctly and securely.
🙏 Thank You for Reading!
Thank you for reading this blog! I hope it helped you understand the Transport Layer in depth. My final blog on the Application Layer is still pending, so stay tuned! 🚀
📢 Follow me on LinkedIn and X (Twitter) for more updates! 😊



Top comments (0)