Imagine this: a server in your production environment has been breached, and the security team suspects malware or rogue files have been installed. Speed is crucial. As an engineer, your ability to run detailed and precise Linux searches can make a world of difference in identifying, isolating, and removing the threat.
Incident response involves a lot of steps, but in this article, I’ll focus on the critical role Linux searches play. I’ll walk you through some essential search commands that can help uncover suspicious files like newly created executables, recently modified files, and those with unusual extensions. Plus, I’ll share a bonus tip for generating a CSV report of your search results.
Index
- Finding Recently Modified Files
- Locating Newly Created Executables
- Identifying Files with Unusual Extensions
- Bonus Tip: Generate a CSV Report
- Summary
Why Mastering Linux Searches Matters
In a large-scale production environment, hundreds, if not thousands, of files are created or modified daily. Running imprecise searches can return overwhelming results, wasting valuable time. By mastering advanced Linux search commands, you can pinpoint the exact information you need during an incident response, saving time and mitigating risks effectively.
Key Searches to Run During a Breach
1. Finding Recently Modified Files
When dealing with a breach, one of the first steps is identifying files modified recently. This can help you detect suspicious activity.
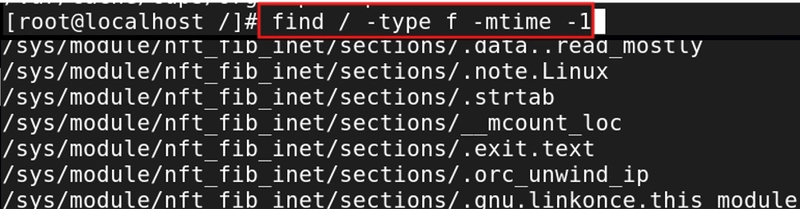
Command: - find / -type f -mtime -1
What It Does:
find /: Starts searching from the root directory.
-type f: Limits the search to files only.
-mtime -1: Finds files modified in the last 24 hours.
This search will return a lot of results because a lot if legitimate files can be generated in 24 hours, and it may be too broad of a search, but it's a place to start.
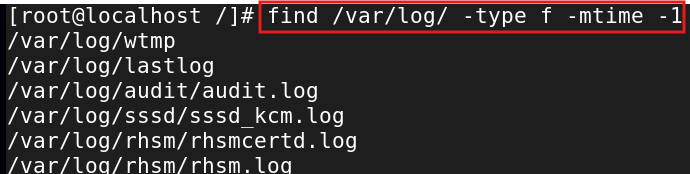
If you wanted to search the log files modified in the last 24 hours, run the command find /var/log/ -type f -mtime -1. This will return files in the log directory.
Use Case: If rogue files were added during the breach, this command helps identify them quickly. Be precise with your searches to avoid sifting through unrelated results.
2. Locating Newly Created Executables
Newly created executables can be a major red flag. These might be scripts or binaries added by attackers.
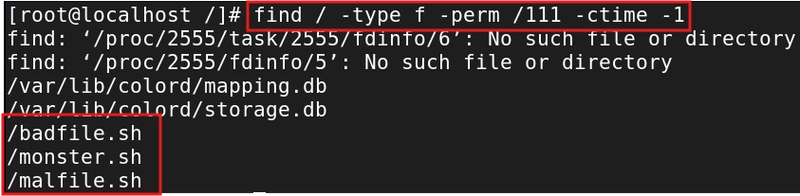
Command: - find / -type f -perm /111 -ctime -1
What It Does:
-perm /111: Finds files with execute permissions (for user, group, or others).
-ctime -1: Filters files created in the last 24 hours.
Use Case: Helps you focus on executable files that could potentially be malicious programs.
3. Identifying Files with Unusual Extensions
Attackers often hide malicious files using uncommon or suspicious extensions.
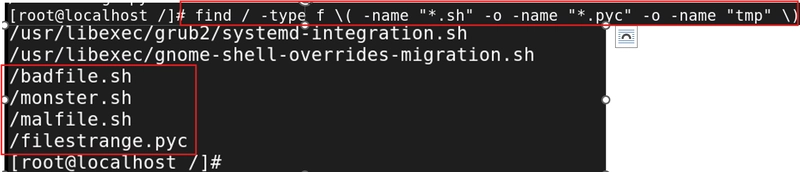
Command: - find / -type f \( -name "*.sh" -o -name "*.pyc" -o -name ".tmp" \)
What It Does:
-type f: Limits the search to files.
\( ... \): Groups multiple conditions.
-o: Acts as “OR” to search for multiple extensions like .sh, .pyc, and .tmp.
Use Case: Quickly locate files with extensions that don’t usually appear in your system but may indicate malicious intent.
4. Bonus Tip: Generate a CSV Report
If you need to document your findings, you can export search results into a CSV file for easier analysis.
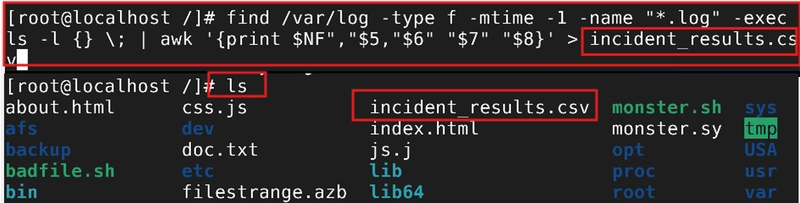
Command: - `find /var/log -type f -mtime -1 -name "*.log" -exec ls -l {} \; | awk '{print $NF","$5","$6", "$7" "$8}' > incident_results.csv
This command finds log files accessed in the last 24 hours and puts the output in a CSV file.
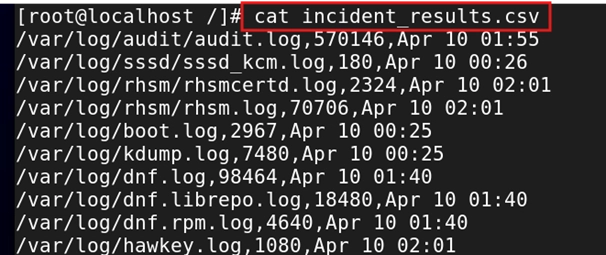
Run the command cat incident_results.csv to view the contents of the CSV file.
What It Does:
-exec ls -l {}: Lists details about each file found.
awk: Extracts the file name, size, and timestamp.
> incident_results.csv: Redirects the output into a CSV file.
Use Case: Perfect for creating a structured report to share with your security team or to document the incident.
5. Summary
When responding to a server breach, time is critical. The ability to perform precise, detailed searches on Linux servers is an invaluable skill for any engineer. By identifying suspicious files, you can help your team resolve incidents faster and more effectively. Having strong Linux search skills isn’t just about being technically proficient; it’s about being prepared when it matters most.
Connect with me on LinkedIn to comment or share your experiences with Linux.
#30DaysLinuxChallenge #RedHatEnterpriseLinux
#CloudWhistler #CloudEngineer #Linux
#DevOps #RedHat #OpenSource
#CloudComputing #WomenInTech


Top comments (2)
I enjoyed reading this!
nice!