A developer from the compañy I work asked me about the posibility of adding a new database for a new requirement. After asking some question about what he needs to do, we decided to moved to elastic cache.
First.
we need to crete a security group to permit port 6379
resource "aws_security_group" "allow_cache" {
name = "allow_cache-${local.app_name}-${terraform.workspace}"
description = "Allow cache inbound traffic"
vpc_id = var.vpc-id
ingress {
description = "cache from VPC"
from_port = 6379
to_port = 6379
protocol = "tcp"
cidr_blocks = [var.allowed_cidr_block-1]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "allow_cache"
}
}
Lambda role
resource "aws_iam_role" "lambda_vpc_role" {
name = "lambda-vpc-role-${local.app_name}-${terraform.workspace}"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Principal = {
Service = "lambda.amazonaws.com"
}
}
]
})
}
attachmet
resource "aws_iam_role_policy_attachment" "lambda_vpc_role_policy" {
policy_arn = "arn:aws:iam::aws:policy/service-role/AWSLambdaVPCAccessExecutionRole"
role = aws_iam_role.lambda_vpc_role.name
}
Cluster elastic cache with output
resource "aws_elasticache_cluster" "hr_cache" {
cluster_id = "clusterforlambdatest-${local.app_name}-${terraform.workspace}"
engine = "redis"
node_type = "cache.t4g.micro"
num_cache_nodes = 1
port = 6379
#engine_version = "3.2.10"
subnet_group_name = aws_elasticache_subnet_group.subnet-sg.id
security_group_ids = [aws_security_group.allow_cache.id]
tags = {
nombre = "hr_cache"
deploy = "terraform"
}
}
output "elasticache_endpoint" {
value = aws_elasticache_cluster.hr_cache.cache_nodes.0.address
}
all code here:
resource "aws_security_group" "allow_cache" {
name = "allow_cache-${local.app_name}-${terraform.workspace}"
description = "Allow cache inbound traffic"
vpc_id = var.vpc-id
ingress {
description = "cache from VPC"
from_port = 6379
to_port = 6379
protocol = "tcp"
cidr_blocks = [var.allowed_cidr_block-1]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "allow_cache"
}
}
resource "aws_iam_role" "lambda_vpc_role" {
name = "lambda-vpc-role-${local.app_name}-${terraform.workspace}"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Principal = {
Service = "lambda.amazonaws.com"
}
}
]
})
}
resource "aws_iam_role_policy_attachment" "lambda_vpc_role_policy" {
policy_arn = "arn:aws:iam::aws:policy/service-role/AWSLambdaVPCAccessExecutionRole"
role = aws_iam_role.lambda_vpc_role.name
}
#resource "aws_subnet" "example" {
# vpc_id = aws_vpc.example.id
# cidr_block = "10.0.0.0/8"
#
# tags = {
# Name = "my-subnet"
# }
#}
resource "aws_elasticache_subnet_group" "subnet-sg" {
name = "my-cache-subnet"
subnet_ids = [var.subnet-t-app-net]
}
resource "aws_elasticache_cluster" "hr_cache" {
cluster_id = "clusterforlambdatest-${local.app_name}-${terraform.workspace}"
engine = "redis"
node_type = "cache.t4g.micro"
num_cache_nodes = 1
port = 6379
#engine_version = "3.2.10"
subnet_group_name = aws_elasticache_subnet_group.subnet-sg.id
security_group_ids = [aws_security_group.allow_cache.id]
tags = {
nombre = "hr_cache"
deploy = "terraform"
}
}
output "elasticache_endpoint" {
value = aws_elasticache_cluster.hr_cache.cache_nodes.0.address
}
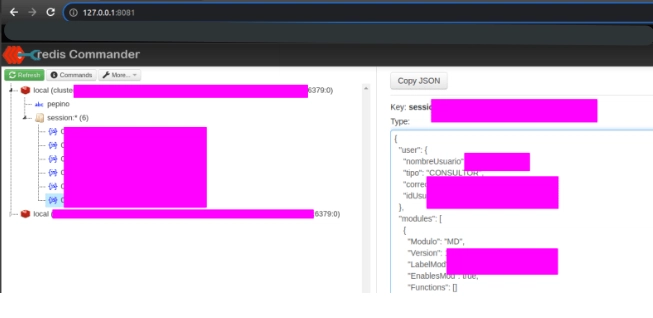
in order to test this, we can install a tool called redis comander
redis-commander --redis-host clusterforlambdatest-xxxx-prd.xxxxxxxxxx.cache.amazonaws.com
If we are saving data correctly into the Elastic Cache, we can see it here.



Top comments (0)