Let me take you through a scenario I imagine a lot of you have experienced time and time again.
I'm signing up for an account on a website, and finally, I get to the dreaded inputs: password and password confirmation.
I open up my password manager, generate a new pass, copy it to the clipboard, and paste it into the input (if it allows, but we'll get to that...).
"Please enter a valid password."
Rage ensues.
Without a doubt, there is a disallowed special character... or it's too long... or there isn't the minimum number of required capital letters... or <insert other archaic requirements here>. Sometimes they are nice enough to tell me what is barring me from proceeding, but that's rare and more often than not I'm left to copy the password into a text-editor and remove characters, one-by-one, until finally the password satisfies the, often unstated or vague (must contain a special character, but ope, not that one, I don't like that one...), requirements. Or worse, I go with 'ol faithful: "Foobar1234!". Security win. Should I forget to return to my password manager to update the entry, I'm granted the pleasure of going through this entire song and dance again the next time I attempt to log in as I now need to do a password reset.
This is far from a theoretical scenario; it happens all the time. It makes me irate, every time.
Please, for the love of UX, stop doing this. Banking websites seem to be the worst about it.
And the thing is, the way I see it, if the stated goal is to increase security, it seems counterproductive at best. I'm no security researcher, but I do understand how brute forcing works (which is the only attack vector attempting to be mitigated here as far as I can tell. If the app/company is irresponsible/incompetent with the data, none of it matters anyway).
The number of possible passwords, given no restrictions, is a simple 95^lengthOfPassword. (95 is the number of ASCII printable characters: 26 uppercase, 26 lowercase, 10 numbers, 33 special characters).
For each blacklisted character, the base is reduced by one. While nothing will ever be as crucial to password strength as length, this still results in a massive decrease in the worst-case runtime.
But it gets worse.
Lets say, as many, many websites do, at least one capital letter is required. What this means is that we can go ahead and omit every password containing only lowercase, numbers, and/or special characters (still assuming every special character is permitted).
95^lengthOfPassword - (95 - 26)^lengthOfPassword
With an 8 character password this eliminates ~513.8 trillion possibilities right off the bat.
In reality the maths are much more complex including summations and whatnot (unless an explicit length is specified, which is very bad) and I'll concede that the set of possible passwords is still immensely large, but the point I'm trying to convey is hopefully clear; each added complexity requirement only further shrinks the possible solution set, decreasing security rather than increasing it. It is purely antithetical to the stated goal. More-so it impedes the usability of the tool that does more to protect me online than anything, my password manager, and makes me more likely to fall back on that "Foobar1234!" out of sheer frustration.
So please, stop. Don't do it. If you really want to protect your users, enforce a minimum password length, disallow commonly used passwords, and/or require actual complexity.
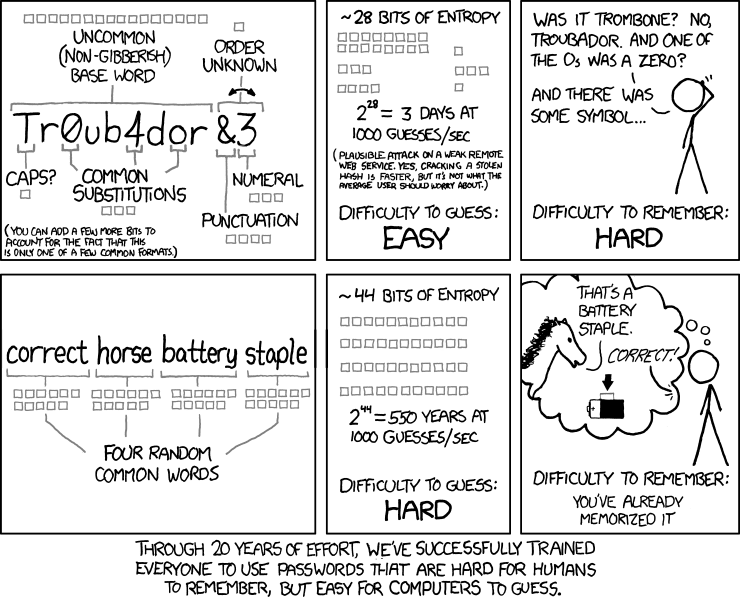
As is often the case, XKCD put it clearer and more succinctly than I ever could. We have trained people to use passwords that are hard to remember, and easy to crack.
And, because I said I'd get to it, stop doing one other thing: disallowing paste. I'm really not sure exactly what people believe this accomplishes. Not only does it make the likelihood of mistyping a password increase infinitely (as there is precisely zero chance of mistyping a pasted password), it's wholly ineffective: F12 -> document.querySelectorAll('input[type=password]').forEach((el) => el.value = 'mypassword'). Just call me hackerman.
Sorry for the rant. Bridgecrest's website just really, really sucks.


Top comments (7)
I'm with you on this. Can't stand the password requirements like add special char etc. I wrote a password manager that remembers the password reqirements for you.
It's called C'YaPass and you can try it in your browser without installing anything: cyapass.com/js/cya.htm
It's entirely implemented in client-side JavaScript and the code is Open Source and available at : github.com/raddevus/CYaPass-Web
My password manager doesn't store your password anywhere and allows you to draw one pattern that can be used to generate unlimited unique passwords based upon SHA-256 hashes. Also when you add your site key (the way to remember which site your password will be used at) you can set the password requirements (length, special char, uppercase) so you never have to remember that stuff again.
Check it out and let me know what you think. I've attached a quick snapshot of how you add a new site key and requirements.

You'll have to pry pass + dmenu from my cold, dead hands, but I'll definitely take a look at this if out of nothing more than curiosity. Have you considered making it a PWA and hosting on GH pages? Would also be super cool with the "add special characters" feature to be able to whitelist/blacklist characters.
edit: scratch gh pages and whitelisted special chars, skipped over the fact you've already got it hosted. You're already steps ahead of me 😅
I've written the app as a Android, iOS, and WinForms app also so you can run it from anywhere. All source code to every version is available at my GitHub repos (github.com/raddevus?utf8=%E2%9C%93...) so everyone can examine the code and build it for themselves.
You can easily take the SPA web app that I built and copy it to your own web site and start using it there. It saves your sitekeys in your localstorage that can only be retrieved at that URL / DOMAIN.
I tried to make it completely open so people might start using it. I've written this up a bit at CodeProject.com also.
And one more thing. You'll never have to type your passwords again because I copy the the password to your clipboard. That way you can
Easy as that. I don't even know my passwords any more. I just draw my pattern and paste them in. And they're super strong random chars of SHA-256.
My password manager for years has been an encrypted gpg file I use with a vim plugin. When it comes to making specific passwords, there's a linux cli command called "apg" (auto password generator). You can designate length and complexity options and it will generate six passwords. With the default options is generates pronounceable passwords.
I like a 13-15 character password, sometimes I may have to change a few characters, a number here, symbol there, or capital letter and they end up being pretty good. It would be trivial to import them into any password manager utility.
A top tip for banking websites, by the way, where they ask for "letter 9 from your super-secret word", is to add a note to your password manager for that site like this:
A great read. Thanks for writing this.