Hi Folks, AWS announced that a new capability in AWS Key Management Service (AWS KMS) called multi-Region keys, where it lets you replicate keys from one Amazon Web Services (AWS) Region into another.
So today I am going to show how multi-Region keys can be used and its usefulness with few examples.
What is special about Multi-Region keys?
Multi-Region keys are a set of interoperable KMS keys that have the same key ID and key material, and that you can replicate to different Regions within the same partition. With symmetric multi-Region keys, you can encrypt data in one Region and decrypt it in a different Region.
AWS services also let you configure multi-Region keys for server-side encryption in case you want the same key to protect data in multiple regions. Also multi-region key will be useful for Client-side encryption where it reduces the latency and extra burden when your application is deployed in multiple regions.
Create a multi-region KMS key
First create the multi region KMS key in a desired region. I choose us-east-1(N.Virginia) region.
Go to KMS service, click create key and choose the option multi-region key.(I will create a Symmetric Key in this tutorial but you can create asymmetric key as well)

Choose Key Administrator users or roles.

Once you followed the steps shown as below, you will able to create a Multi-region KMS key.
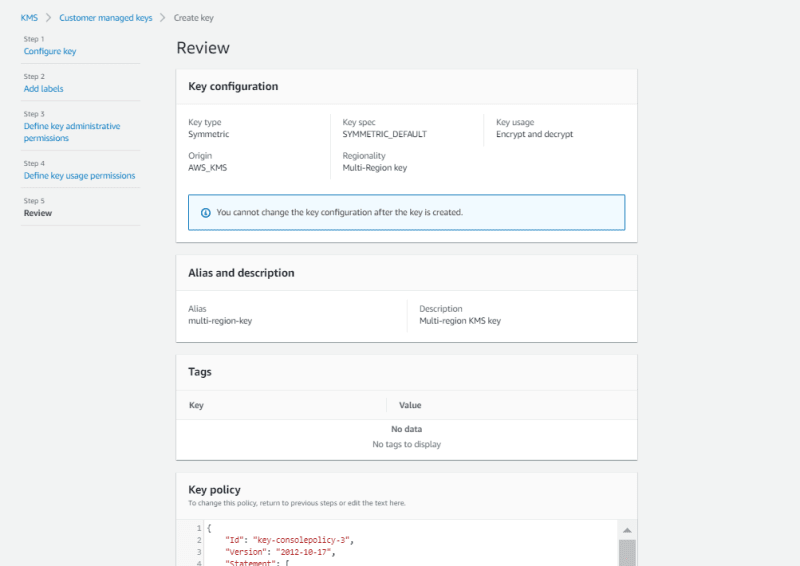
This can be used in one region only until you create replicas.

Note: Multi-Region Key is consist of two types of keys.
Primary Key - This is the place where key is created originated initially. In our case we created the multi-region KMS key in N.Virginia(us-east-1). So primary key will be placed here.
Replica Keys - You can create replica keys of primary key in each region.
It has different ARNs. But all of these keys have Key ID and share same key materials.
Primary Key --> arn:aws:kms:us-east-1:528196604817:key/mrk-095774ce295d40a8a249e0257825598c
Replica Key -->arn:aws:kms:us-west-2:528196604817:key/mrk-095774ce295d40a8a249e0257825598c
Create new replica keys under regionality configuration section. For this tutorial, I will create a replica key in Oregon region. This will be used later.
Note: Key policy needs to be defined for each replica key as well.
Why?
every multi-Region key, whether primary or replica, is a fully functional, independent KMS key resource with its own key policy, aliases, grants, key description, lifecycle, and other attributes
Applications:
1) S3 Cross-region Replication:
Previously when you want to enable S3 cross region replication between two regions with server side encryption using custom KMS keys, You need to create two KMS keys in each region but KMS key materials is different for each key. Therefore AWS has to
transparently decrypt and re-encrypting data on your behalf using the KMS keys you designate in the destination Region.
But when you use multi-region key for both S3 buckets, then this burden is reduced as the key material is same. So it is recommended to use multi-region key unless there is any special compliancy requirement exists where keys materials cannot be replicate between regions.
Lets create source and destination buckets with server-side encryption(using previously created multi-region key)
Creation of source bucket
Creation of destination bucket
Create replication rules in source bucket
choose the destination bucket in replication rule

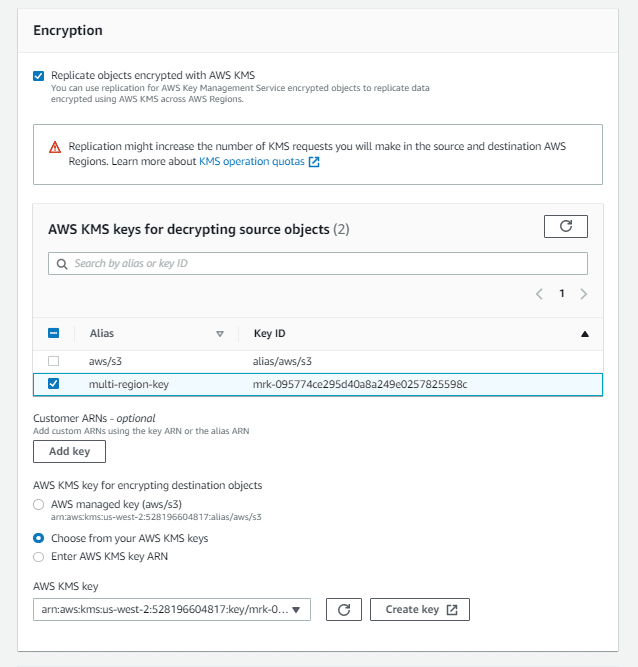
To replicate objects encrypted with CMKs stored in AWS KMS, you must explicitly enable the option. Use the same multi-region KMS key.
Require a IAM role for replication. Since I didn't create role earlier, I will go for create new role option.

Lets have a look at the policy of the IAM role.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:ListBucket",
"s3:GetReplicationConfiguration",
"s3:GetObjectVersionForReplication",
"s3:GetObjectVersionAcl",
"s3:GetObjectVersionTagging",
"s3:GetObjectRetention",
"s3:GetObjectLegalHold"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::chathra-s3-cross-region-replication-source-bucket",
"arn:aws:s3:::chathra-s3-cross-region-replication-source-bucket/*"
]
},
{
"Action": [
"s3:ReplicateObject",
"s3:ReplicateDelete",
"s3:ReplicateTags",
"s3:GetObjectVersionTagging",
"s3:ObjectOwnerOverrideToBucketOwner"
],
"Effect": "Allow",
"Condition": {
"StringLikeIfExists": {
"s3:x-amz-server-side-encryption": [
"aws:kms",
"AES256"
],
"s3:x-amz-server-side-encryption-aws-kms-key-id": [
"arn:aws:kms:us-west-2:528196604817:key/mrk-095774ce295d40a8a249e0257825598c"
]
}
},
"Resource": [
"arn:aws:s3:::chathra-s3-cross-region-replication-dest-bucket/*"
]
},
{
"Action": [
"kms:Decrypt"
],
"Effect": "Allow",
"Condition": {
"StringLike": {
"kms:ViaService": "s3.us-east-1.amazonaws.com",
"kms:EncryptionContext:aws:s3:arn": [
"arn:aws:s3:::chathra-s3-cross-region-replication-source-bucket/*"
]
}
},
"Resource": [
"arn:aws:kms:us-east-1:528196604817:key/mrk-095774ce295d40a8a249e0257825598c"
]
},
{
"Action": [
"kms:Encrypt"
],
"Effect": "Allow",
"Condition": {
"StringLike": {
"kms:ViaService": [
"s3.us-west-2.amazonaws.com"
],
"kms:EncryptionContext:aws:s3:arn": [
"arn:aws:s3:::chathra-s3-cross-region-replication-dest-bucket/*"
]
}
},
"Resource": [
"arn:aws:kms:us-west-2:528196604817:key/mrk-095774ce295d40a8a249e0257825598c"
]
}
]
}
Test Cross region replication
Lets upload a file to source bucket.
Once uploaded check the replication status. If its successful, the status should be "COMPLETED".

File is successfully copied to destination bucket and its encrypted using same multi-region KMS Key
Clean Up
When you schedule to delete multi region KMS key, make sure to delete both primary and replica, If you try to delete it only from the primary region, your primary key will stuck in following state without deleting.





















Oldest comments (1)
As per the S3 doc:
You can use multi-Region AWS KMS keys in Amazon S3. However, Amazon S3 currently treats multi-Region keys as though they were single-Region keys, and does not use the multi-Region features of the key.
Please re-verify above article about S3 Cross Region Replication with Multi region keys