Data is the new gold according to many scholars. It becomes much important to secure data on internet from the unauthorized users.
Reactjs is one the popular library of Javascript used to make SPA's and Mpa's. As is provides ease for developer to work over front-end development , its side effects are also huge.
It’s also true that React web apps may face certain security pitfalls. But it’s nothing discouraging, every framework has its own pitfalls. What matters is how you deal with React security vulnerabilities and protect your application against possible attacks.
[Link]https://www.simform.com/blog/react-security-vulnerabilities-solutions/
React Security Vulnerabilities and How to Prevent Them
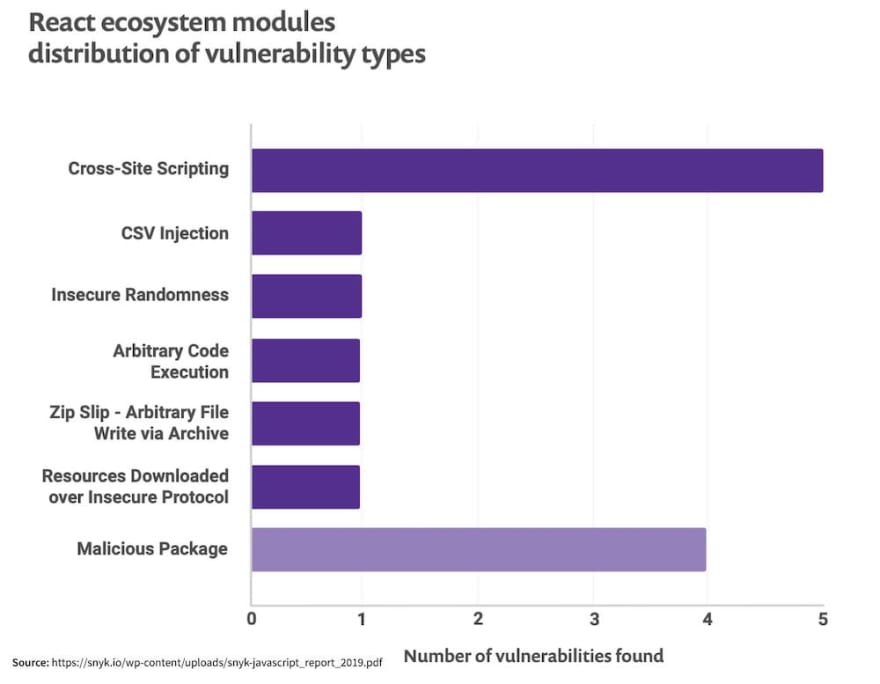
- Cross-Site Scripting (XSS) XSS is an injection of a malicious script into the code of a web application. The browser picks up this script and interprets it as legitimate. After that, the malicious code is executed as a part of an app.
Prevention:
APIs like createElement() help in automatic detection of injection attacks
The power of JSX can be leveraged in order to secure the application via its auto-escaping functionality
Third-party libraries like dangerouslySetInnerHTML can be used to set HTML directly from React instead of using innetHTML that is vulnerable to XSS
2.SQL Injection
Another common React security vulnerability is SQL injection (SQLi). It’s a trick hackers use to inject your database with random SQL code. By doing this, they are able to receive, edit, or delete data irrespective of user permissions.
Hackers are able to pull off SQLi by faking or creating new credentials. They manage to access data on the server by getting the admin credentials. Such a security attack can be very dangerous as hackers can modify this data or even destroy it.
Error based SQLi, time-based SQLi, and logical-error-based SQLi are three common types of SQL injections.
Broadly, a React application is vulnerable to this security pitfall because of improper coding of the app. Some developers may accidentally make it possible for SQL statements to enter through entry fields and move to the database directly.
Prevention
In no case should you allow your React app to connect to any database that may have admin privileges.
- Broken Authentication Invalid authentication processes, improper implementation, and failure of authentication functions lead to compromise or exploitation of credential data in your web app. In some cases, authentication failure leads to credential stuffing and even automated brute force attacks.
Here’s a quick and dirty checklist you can follow to improve your authentication :
Implement multi-factor authentication
Initiate credential recovery
Incorporate API pathways
Use cloud native authentication for secure access (Example: amazon cognito)
Prevention
Employ multi-factor authentication wherever possible. It prevents attacks from credential stuffing and stolen credential re-use.
- XML External Entities (XXE) In certain cases, XXE attacks are also considered a type of injection attack. XML parsers that are outdated in your React web application become the most vulnerable to get abused with injection attacks leading to DoS attacks. In such attacks, the perpetrator attempts to collect confidential data from the server.
In certain cases, XXE attacks fall under the category of injection attacks. Outdated XML parsers in your React web app are the most vulnerable to injection attacks that lead to DoS attacks.
- Security Misconfiguration Needless to say, web applications developed using Reactjs do not follow security measures by default. It has to be incorporated during the development cycle to avoid any damage from occurring in the application framework. Often React security misconfigurations occur because of improperly built HTTP headers or incomplete configurations.


Oldest comments (0)