AWS Threat Detection Service:
Amazon GuardDuty is threat detection service that continuously monitors for malicious activity and it keeps track of unauthorized API activity or behavior to protect AWS accounts.
How GuardDuty works:
Once we enable the GuradDuty within our AWS account, it automatically start collecting VPC flow logs,Cloudtrail logs event(Management and Data event) and DNS query logs. It continuously monitor and analyze these logs and provide us the findings If there is any abnormal activity within AWS account.
It also uses threat intelligence feeds, such as lists of malicious IP addresses and domains, and machine learning to identify unauthorized and malicious activity within our AWS environment.
Along with AWS threat intelligence feeds we can use our own Blacklist and Whitelist IP address for malicious IP detection.
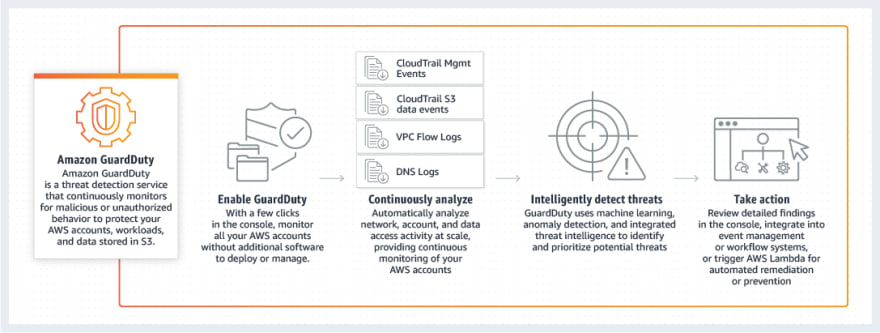
(Image taken from AWS)
How to enable GuardDuty in AWS Account:
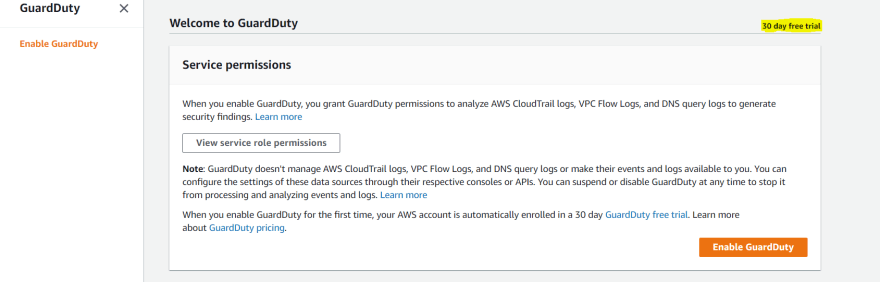
When we enable GuardDuty for the first time, AWS account is automatically enrolled in a 30-day GuardDuty free trial. We can view the details of GuardDuty free trial in the usage page of the GuardDuty console.
Steps:
- Login to the console, choose the region and find GuardDuty under Services.
- After clicking on GuardDuty, below page will be display. Click on Get started.
- Click on Enable GuardDuty. When GuardDuty is enabled a GuardDuty detector is created in that region.
When we enable GuardDuty, it create service-linked role called
AWSServiceRoleForAmazonGuardDuty. This service-linked role
allows GuardDuty to retrieve details of EC2 instances and S3
buckets in our AWS environment that are involved in potentially
suspicious activity.
- After enabling GuardDuty, it takes some time to display the findings.
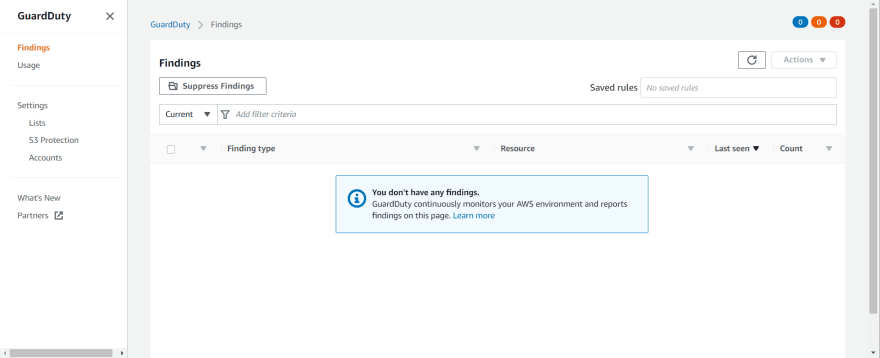
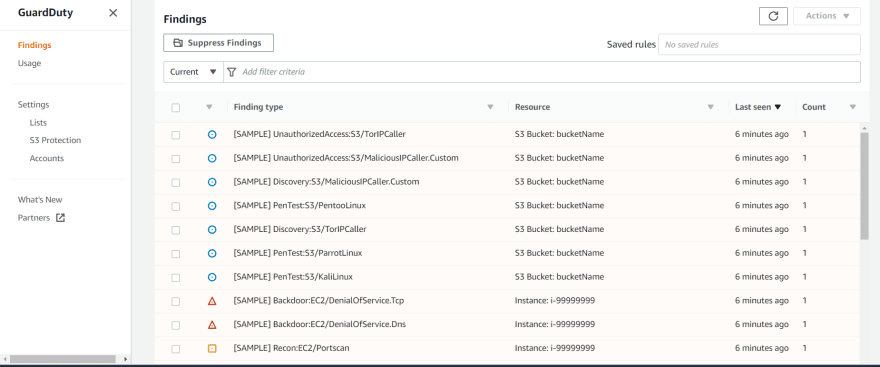
How to check GuardDuty Findings:
- Go to GuardDuty> Findings. Below is screenshot of sample findings.
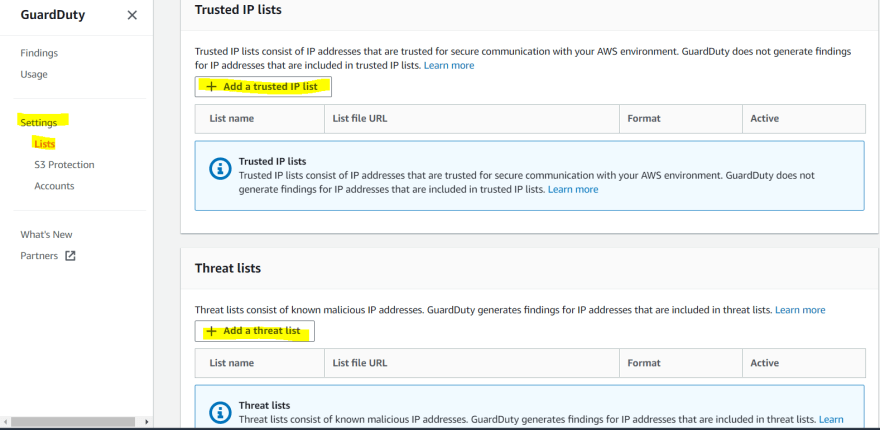
How to create Custom Whitelist and Blacklist IP lists.
- Go to GuardDuty> Settings> lists
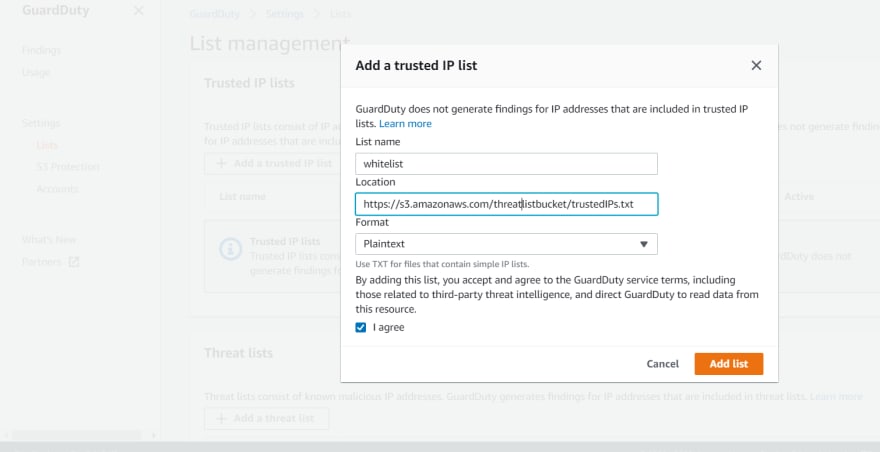
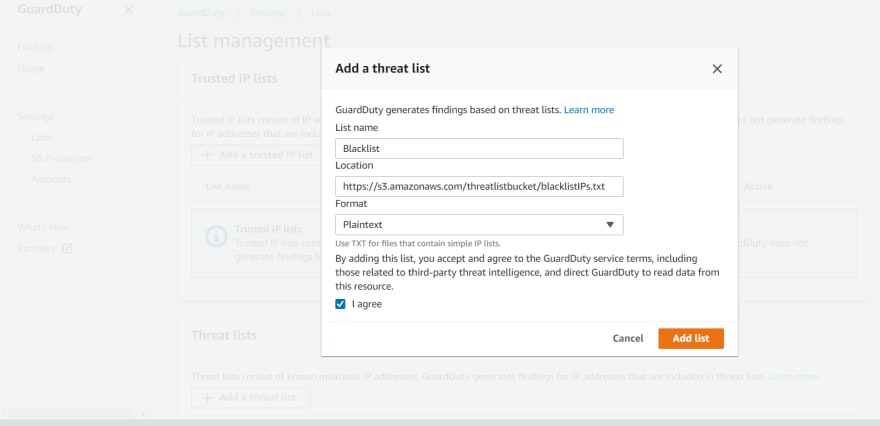
- To add trusted IPs(Whitelist), click on add trusted IP list. If you would like to add custom Blacklist IPs, click on add a threat list. After clicking on "add a trusted IP list/add a threat list" It will prompt and ask us to specify the bucket URL where we are storing blacklist and whitelist IP address. Please refer below screenshot.
Severity levels for GuardDuty findings:
Each GuardDuty finding has severity level and value range. Severity value range start from 0 to 10.
- High (7.0 - 8.9)
- Medium (4 - 6.9)
- Low (1 -3.9 )
Where is severity value 0-0.9 and 9.0-10.0?
Values 0 and 9.0 to 10.0 are currently reserved for future use by AWS.
By default findings are automatically sent to CloudWatch Events
every 6 hours and it can be change to 1 hour and 15 minutes.
GuardDuty can also send findings to S3 bucket and that can be further use for analysis and take action by third party tools.
Thank You.




Top comments (0)