As microservices continue to revolutionize application development, they also introduce new challenges related to service discovery, observability, traffic management, and security. This is where Service Mesh comes into play. In this blog, we’ll explore what a service mesh is, how it works, and why it's essential in a cloud-native environment.
🔧 What is a Service Mesh?
A service mesh is a dedicated infrastructure layer that facilitates service-to-service communication within a microservices architecture. It decouples these capabilities from the application code by handling concerns such as:
- Secure communication (mTLS)
- Load balancing
- Traffic routing
- Retry logic
- Observability (metrics, logs, traces)
All of these capabilities are abstracted away from your code and implemented at the infrastructure level, making service mesh a powerful paradigm for large-scale, distributed systems.
🏋️ Core Components of a Service Mesh
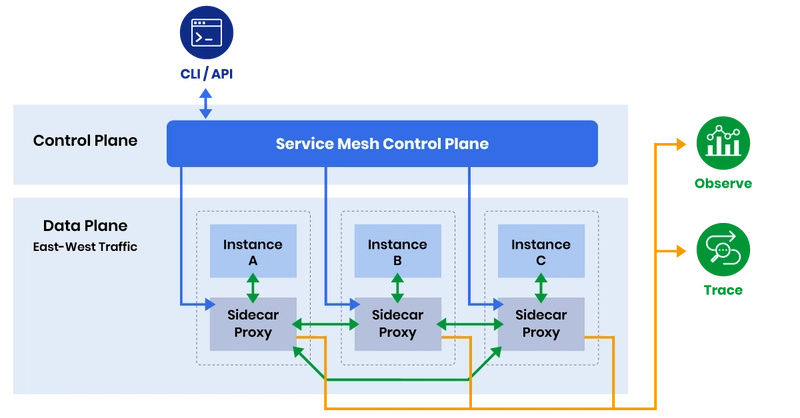
1. Data Plane
The data plane is composed of lightweight network proxies, often deployed as sidecars alongside each service instance. These proxies handle real-time communication between services.
Responsibilities:
- Service discovery
- Load balancing
- TLS encryption/decryption
- Health checks
- Traffic routing (e.g., A/B testing, canary releases)
Popular proxy: Envoy
2. Control Plane
The control plane manages the configuration and behavior of the data
plane.
Responsibilities:
- Policy management (routing, retries, timeouts)
- Security configurations
- Certificate distribution (for mTLS)
- Observability integrations
Popular control plane tools: Istiod (Istio), Kuma CP, Consul CP
📝 Architecture Overview
The typical service mesh architecture looks like this:
+-------------------+ +-------------------+ +-------------------+
| Service A | | Service B | | Service C |
| +---------------+ | | +---------------+ | | +---------------+ |
| | Sidecar Proxy|<-------->| | Sidecar Proxy|<-------->| | Sidecar Proxy| |
| +---------------+ | | +---------------+ | | +---------------+ |
+-------------------+ +-------------------+ +-------------------+
| | |
+--------------------------+--------------------------+
|
Control Plane
|
(e.g., Istiod)
All communication between services passes through their respective sidecar proxies, which are configured and controlled by the control plane.
🚀 Key Features and Capabilities
🛡️ Security
- Mutual TLS (mTLS) for secure, encrypted service-to-service communication
- Fine-grained access control between services
⚖️ Traffic Management
- Intelligent routing: blue-green, canary, A/B testing
- Fault injection for resilience testing
- Circuit breaking and retry policies
📊 Observability
- Metrics: request/response times, success/error rates
- Distributed tracing (Jaeger, Zipkin)
- Centralized logging
🚧 Resilience
- Timeout, retry, and failover mechanisms
- Rate limiting
- Health probes
🧪 Popular Service Mesh Tools
| Tool | Data Plane | Control Plane | Highlights |
|---|---|---|---|
| Istio | Envoy | Istiod | Most feature-rich and widely used |
| Linkerd | Linkerd2 | Linkerd CP | Lightweight and fast |
| Consul | Envoy | Consul CP | Integrated with HashiCorp tools |
| Kuma | Envoy | Kuma CP | Built by Kong, supports multi-mesh |
| Open Service Mesh (OSM) | Envoy | OSM CP | Microsoft-backed, simple setup |
📊 Use Case Scenarios
- Multi-team, multi-service environments needing secure, consistent communication
- Applications with high compliance requirements (zero trust architecture)
- Gradual deployment of new features with canary or A/B strategies
- Applications needing unified monitoring and logging across services
🔧 Example: Istio in Action
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: reviews
spec:
hosts:
- reviews
http:
- route:
- destination:
host: reviews
subset: v2
weight: 80
- destination:
host: reviews
subset: v1
weight: 20
This Istio config routes 80% of traffic to version 2 of the reviews service and 20% to version 1. Useful in canary deployments.
🚫 Service Mesh vs API Gateway
| Feature | Service Mesh | API Gateway |
|---|---|---|
| Scope | Internal service-to-service | Ingress traffic |
| Security | mTLS, RBAC | JWT, OAuth |
| Observability | Distributed tracing | Request/response metrics |
| Use Case | Microservice internal communication | External client requests |
Often used together: API Gateway at the edge, service mesh inside the cluster.
💚 Best Practices
- Start Small: Don’t mesh everything at once. Begin with critical services.
- Monitor Overhead: Keep an eye on latency and resource usage.
- Automate with GitOps: Manage mesh configurations via Git.
- Secure the Control Plane: Ensure it can't be a single point of failure.
- Use Observability Tools: Integrate Prometheus, Grafana, Jaeger, etc.
📅 Final Thoughts
Service meshes like Istio and Linkerd are powerful tools to tame the complexity of modern cloud-native architectures. They bring in built-in security, observability, and resilience with minimal effort from developers.
While they do introduce a learning curve and operational overhead, the long-term benefits in scale, governance, and control are undeniable.
Embrace the mesh, not the mess. ✨
Written by Nitesh Kumar Sah | DevOps & System Design Blogger



Top comments (0)