I'm excited to announce that HTTP View (the first release of HTTP Toolkit) is now available!
HTTP View is a free & open-source HTTP inspector. HTTP View lets you intercept HTTP or HTTPS traffic with one click, explore & examine that traffic up close, and discover exactly what your code (or anybody else's) is sending.
Want to dive right in? Download it now.
HTTP Toolkit is a project that I've been working on for a while, to build an open-source suite of tools for HTTP development. The goal is to intercept & examine HTTP, edit it live, analyse flows of HTTP requests to audit performance and security, and rapidly prototype HTTP clients or servers.
You might be familiar with Fiddler or Charles - this is a similar concept, but taken further, and updated to integrate closely with newer tools and technology.
This first release includes the core technology for this and the full set of working features for the read-only parts, with lots more to come soon. Some of the features included so far:
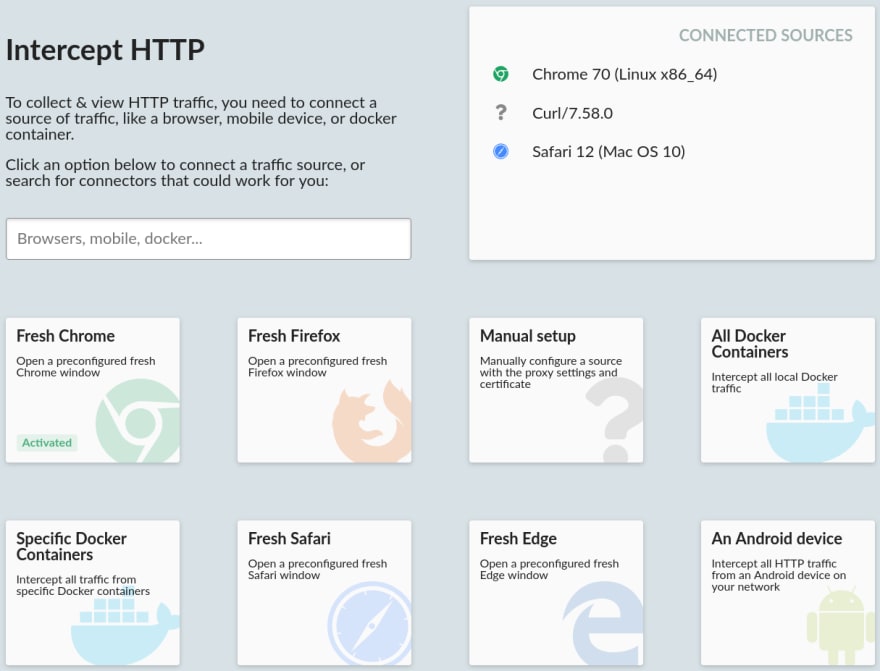
Capture HTTP & HTTPS with zero setup
HTTP View can do automatic hands-free interception for HTTP and HTTPS on a huge range of platforms, with more to come soon, from Chrome to iOS to Docker.
For any platforms without automatic integrations, it simply acts as an HTTP(S) proxy, so it's compatible with almost all HTTP clients out of the box.
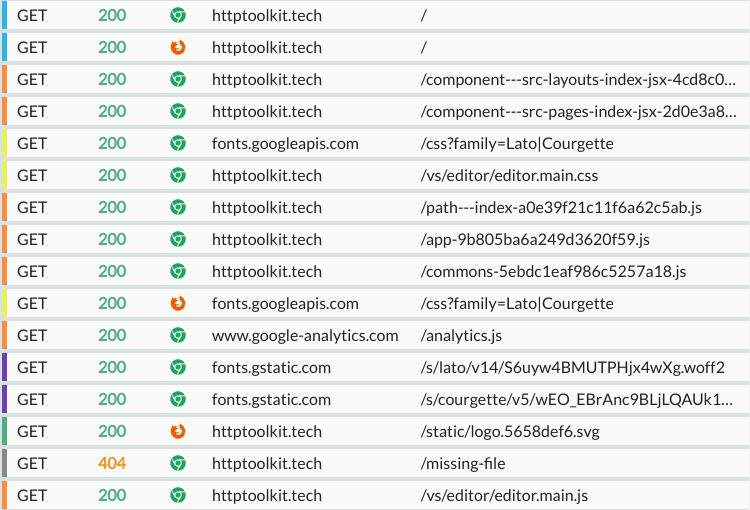
Quickly skim & search HTTP traffic
HTTP exchanges are automatically highlighted by content type, status and source, so you can skim through streams of requests, and easily spot issues. You can search over the full request & response URLs, statuses and headers too, to quickly find whichever message you're hunting.
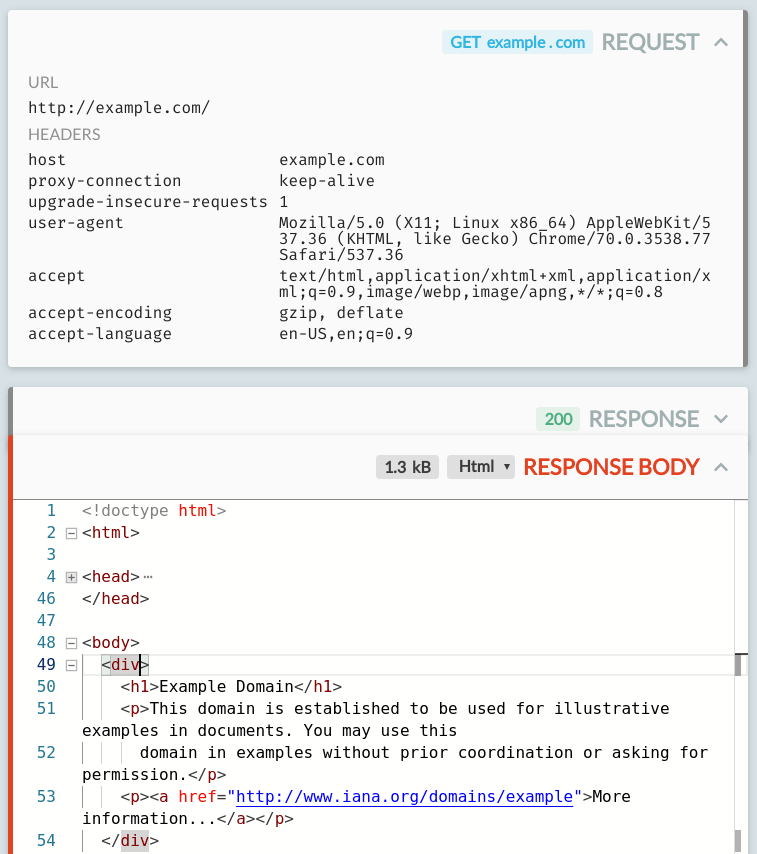
Deep dive into HTTP exchanges
If you pick a specific request, you can examine the full URL, status, headers and body up close to understand exactly what's being sent.
You can also explore the details of request and response bodies, with built-in editor highlighting and autoformatting for JavaScript, JSON, all popular image formats, HTML, hex, etc etc.
All the body inspection is built using Monaco, the editor from Visual Studio Code, so it comes with all the power of VS Code built-in.
Sound interesting? Great! You can download it now from httptoolkit.tech/view.
Have feedback? Let me know below!



Latest comments (4)
Hey bro, this is such a great work. Unfortunately, I couldn't download it. Because limit of time for download. I couldn't resume my download after my session expire. Please fix it thank you
You should be able to redownload, no problem. There's no sessions involved, it's just a download page.
Or do you mean that the download always fails? How fast is your internet? It is about 80MB, which might be a bit difficult on very slow connections (<5MB) but it should still work eventually.
I do have plans to try and make the installer and app work a little better on slow connections, there's definitely more to do there. If you don't mind me asking, where in the world are you?
So, you've built some sort of convenient toolkit for man-in-the-middle attacks against HTTPS?
For local development, yes. It's designed as a development & debugging tool rather than a security tool for mitm generally, though it can help there too.
Note that it does fully automatic mitm attacks only against software running on your own machine though, where it can automatically set up the certificates to make that work. For remote devices (e.g. phones) it will be able to fully automatically intercept plain HTTP traffic, but it can't automatically intercept HTTPS - there has to be a manual step that somehow trusts the certificate on the device.