Intro
In this tutorial we will try provisioning a vm on azure using their terraform provider and reproduce the same deployment I have completed on AWS and Oracle Cloud. As usual we won’t just deploy an instance but also configure an nginx website linked to its public IP. I’ll end this post with some notes on Azure/AWS differences.
I used azurerm_linux_virtual_machine resource instead of the classic vm resource because azure decided it was better to split both windows/Linux for vm deployments(provider 2.0) which is unlike anything seen elsewhere.
Note: I have done the same task with my AZ-CLI based bash scripts (avaialble in Github) which was very helpful to understand the logic behind components needed during the vm creation (More details: deploy-webserver-vm-using-azure-cli).
Content :
I. Terraform setup
IV. Partial deployment
V. Full deployment
Tips & Conclusion
Overview and Concepts
Topology
The following illustration shows the layers involved between your workstation an Oracle cloud infrastructure while running the terraform actions along with the instance attributes we will be provisioning.
Besides describing my GitHub repo before starting this tutorial, I’ll just briefly discuss some principles.
- Infrastructure As Code Manages and provisions cloud resources using a declarative code (i.e Terraform) and definition files avoiding interactive configuration. Terraform is an immutable Orchestrator that creates and deletes all resources in the proper sequence. Each Cloud vendor has what we call a provider that terraform uses in order to convert declarative texts into API calls reaching the Cloud infrastructure layer.
Terraform Files
- Can be a single file or split into multiple tf or tf.json files, any other file extension is ignored.
- Files are merged in alphabetical order but resource definition order doesn’t matter (subfolders are not read).
- Common configurations have 3 type of tf files and a statefile.
Terraform resource declaration syntax looks like this:
Component "Provider_Resource_type" "MyResource_Name" { Attribute1 = value ..
Attribute2 = value ..}
Where do I find a good Azure deployment sample?
The easiest way is to create/locate an instance from the console and then use the import function from terraform to generate each of the related components in HCL format (vnet, instance,subnet,etc..) based on their id.
Example for a Vnet >>
1- Create a shell resource declaration for the vnet in a file called vnet.tf
2- Get the id of the vnet resource from your Azure portal
3- Run the Terraform import then run Terraform show to extract the vnet full declaration from azure to the same file ( vnet.tf)
4- Now you can remove the id attribute with all non required attributes to create a vnet resource (Do that for each resource)
1- # vi vnet.tf
provider "azurerm" {
features {}
}
resource "azurerm_virtual_network" "terra_vnet" {
}
2- # terraform import azurerm_virtual_network.terra_vnet /subscriptions/00*/resourceGroups/providers/Microsoft.Network/virtualNetworks/terra_vnet
3- # terraform show -no-color > vnet.tf
If you want to import all the existing resources in your account in bulk mode (not one by one) there are tools likepy-az2tf or terraformer , which can import both code and state from your azure account automatically.
Terraform lab content: I have deliberately split this lab in 2:
- Vnet Deployment: To grasp the basics of a single resource deployment.
- Instance Deployment: Includes the instance provisioning configured as web sever(includes above vnet) .
I.Terraform setup
Although I’m on windows I tried the lab using WSL (Ubuntu) terminal (but same applies to Mac).
- Windows: Download and run the installer from their website (32-bit ,64-bit)
- Linux: Download, unzip and move the binary to the local bin directory
$ wget https://releases.hashicorp.com/terraform/1.0.3/terraform_1.0.3_linux_amd64.zip
$ unzip terraform_1.0.3_linux_amd64.zip
$ mv terraform /usr/local/bin/
- Once installed run the version command to validate your installation
$ terraform --version
Terraform v1.0.3
Azure authentication
- To authenticate with your azure account, Terraform will only need you to login using az cli . This can be done by running az cli commands described here >> az-cli installation
Assumptions
- I will assume that below authentication option is present in your workstation:
- AZCLI default profile configured with your azure credentials. Refer to my Blog post for more details
$ az account show
EnvironmentName HomeTenantId IsDefault Name State
----------------- ---------------- ----------- ------------- -------
AzureCloud 00000000-00000000... True BrokeDba Lab Enabled
- I’ll also assume the presence of an ssh key pair to attach to your vm instance. If not here is a command to generate a PEM based key pair.
$ ssh-keygen -P "" -t rsa -b 2048 -m pem -f ~/id_rsa_az
Generating public/private rsa key pair.
Your identification has been saved in /home/brokedba/id_rsa_az.
Your public key has been saved in /home/brokedba/id_rsa_az.pub.
II. Clone the repository
- Pick an area that is close to your azure-terraform directory on your file system and issue the following command
$ git clone https://github.com/brokedba/terraform-examples.git
Note: As explained earlier you will find 2 directories inside the repository which will make things easier:
- terraform-provider-azure/create-vnet/ To grasp how we deploy a single Vnet.
- terraform-provider-azure/launch-instance/ For the final instance deploy.
III. Provider setup
- INSTALL AND SETUP THE AZURE PROVIDER
- Cd Into “ terraform-provider-azure/create-vnet” where our configuration resides (i.e vnet)
$ cd /mnt/c/Users/brokedba/azure/terraform-examples/terraform-provider-azure/create-vnet
- Azure provider plugin will be automatically installed by running "terraform init".
$ terraform init
Initializing the backend...
Initializing provider plugins...
- Finding latest version of hashicorp/azurerm...
- Installing hashicorp/azurerm v2.80.0...
* Installed hashicorp/azurerm v2.80.0 (signed by HashiCorp)
provider "azurerm" {
Terraform has been successfully initialized!
$ terraform --version
Terraform v1.0.3 on linux_amd64
+ provider registry.terraform.io/hashicorp/azurerm v2.80.0
- Let’s see what’s in the directory. Here, only files matter (click to see content)
$ tree
.
|-- outputs.tf ---> displays resources detail after the deploy
|-- variables.tf ---> Resource variables needed for the deploy
|-- vnet.tf ---> Our vnet terraform declaration
IV. Partial Deployment
DEPLOY A SIMPLE VNET
- Once the authentication is setup and provider installed , we can run terraform plan command to create an execution plan (quick dry run to check the desired state/actions). Specify the prefix for your resource names
$ terraform plan
var.prefix The prefix used for all resources in this example
Enter a value: Demo
Terraform used selected providers to generate the following execution plan.
Resource actions are indicated with the following symbols: + create
------------------------------------------------------------------------
Terraform will perform the following actions:
# azurerm_network_security_group.terra_nsg will be created
+ resource "azurerm_network_security_group" "terra_nsg"
{..
+ security_rule = [
+ destination_port_ranges = [+ "22", + "3389",+ "443",+ "80",]
+ direction = "Inbound"
+ name = "Inbound HTTP access"
# azurerm_resource_group.rg will be created
+ resource "azurerm_resource_group" "rg"
{..}
# azurerm_subnet.terra_sub will be created
+ resource "azurerm_subnet" "terra_sub"
{..
+ address_prefixes = ["192.168.0.0/16”]
…}
# azurerm_subnet_network_security_group_association.nsg_sub will be created
+ + resource "azurerm_subnet_network_security_group_association" "nsg_sub"{
# azurerm_virtual_network.terra_vnet will be created
+ resource "azurerm_virtual_network" "terra_vnet" {
...
+ address_space = [ "192.168.0.0/16”
...}
Plan: 5 to add, 0 to change, 0 to destroy.
- The output being too verbose I deliberately kept only relevant attributes for the Vnet resource plan
- Next, we can run ”terraform deploy” to provision the resources to create our Vnet (listed in the plan)
$ terraform apply -auto-approve
azurerm_resource_group.rg: Creating...
azurerm_virtual_network.terra_vnet: Creating...
azurerm_network_security_group.terra_nsg: Creating...
azurerm_subnet.terra_sub: Creating...
...
Apply complete! Resources: 5 added, 0 changed, 0 destroyed.
Outputs:
Subnet_CIDR = 192.168.10.0/24
Subnet_Name = internal
vnet_CIDR = 192.168.0.0/16
vnet_Name = Terravnet
vnet_dedicated_security_group_Name = "Demo-nsg"
vnet_CIDR = 192.168.0.0/16
vnet_dedicated_security_ingress_rules = toset([
{…
"access" = "Allow"
"description" = "RDP-HTTP-HTTPS ingress trafic"
"destination_port_ranges" = toset([
"22",
"3389",
"443",
"80",])
…
Observations:
- The deploy started by loading the resources variables in variables.tf which allowed the execution of vnet.tf
- Finally terraform fetched the attributes of the created resources listed in outputs.tf
Note : We’ll now destroy the Vnet as the next instance deploy contains the same Vnet specs.
$ terraform destroy -auto-approve
Destroy complete! Resources: 6 destroyed.
V. Full deployment (Instance)
- After our small intro to Vnet creation, let’s launch a vm and configure nginx in it in one command.
- First we need to switch to the second directory terraform-provider-azure/launch-instance/ Here's the content:
$ tree ./terraform-provider-azure/launch-instance
.
|-- cloud-init --> SubFolder
| `--> centos_userdata.txt --> script to config a webserver+ modify the index
| `--> sles_userdata.txt --> for SUSE
| `--> ubto_userdata.txt --> for Ubunto
| `--> el_userdata.txt --> for Enteprise linux distros
| `--> Win_userdata.ps1 --> for windows
|-- compute.tf ---> Instance related terraform configuration
|-- outputs.tf ---> displays the resources detail at the end of the deploy
|-- variables.tf ---> Resource variables needed for the deploy
|-- vnet.tf ---> same vnet we deployed earlier
Note: As you can see we have 2 additional files and one Subfolder. is where the compute instance and all its attributes are declared. All the other “. tf” files come from my vnet example with some additions for variables.tf and output.tf
- Cloud-init : is a cloud instance initialization method that executes tasks upon instance Startup by providing the user_data entry of the azure vm resource definition (See below). I have created enough for 6 OS’ (Centos,Ubuntu,Windows,RHEL,OL,SUSE)
...variable "user_data" { default = "./cloud-init/centos_userdata.txt"}
$ vi compute.tf
resource "azurerm_linux_virtual_machine" "terravm" {
...
custom_data = base64encode ("${file(var.user_data)}")
...
- In my lab, I used cloud-init to install nginx and write an html page that will replace the HomePage at Startup.
- Make sure you your public ssh key is in your home directory or just modify the path below (see variables.tf)
$ vi compute.tf
resource "azurerm_linux_virtual_machine" "terravm" {
..
admin_ssh_key {
username = var.os_publisher[var.OS].admin
public_key = file("~/id_rsa_az.pub") } ## Change m
LAUNCH THE INSTANCE
- Once in “ launch-instance” directory, you can run the plan command to validate the 9 resources required to launch our vm instance. The output has been truncated to reduce verbosity
$ terraform plan
Terraform used selected providers to generate following execution plan.
Resource actions are indicated with the following symbols:
------------------------------------------------------------------------
Terraform will perform the following actions:
... # Vnet declaration (see previous vnet deploy)
...
# azurerm_linux_virtual_machine.terravm will be created
+ resource "azurerm_linux_virtual_machine" "terravm" {
+ ...
+ admin_username = "centos"
+ location = "eastus"
+ size = "Standard_B1s"
+ name = "TerraDemo-vm"
+ private_ip = "192.168.10.51"
+ admin_ssh_key { = {
+ public_key = <<-EOT ssh-rsa AAAABxxx…*
EOT
username =”centos” }
+ custom_data = (sensitive value)
+ os_disk {…}
+ source_image_reference {
+ offer = "CentOS"
+ publisher = "OpenLogic"
+ version = "latest"
}
}
# azurerm_network_interface.Terranic will be created
# azurerm_network_interface_security_group_association.terra_assoc_pubip_nsg will be created
# azurerm_network_security_group.terra_nsg will be created
# azurerm_public_ip.terrapubip will be created
...}
...
}
Plan: 9 to add, 0 to change, 0 to destroy.
- Now let’s launch our CENTOS7 vm using terraform apply (I left a map of different OS ids in the variables.tf you can choose from)
$ terraform apply -auto-approve
...
azurerm_resource_group.rg: Creating...
azurerm_virtual_network.terra_vnet: Creating...
azurerm_network_security_group.terra_nsg: Creating...
azurerm_subnet.terra_sub: Creating...
azurerm_subnet_network_security_group_association.nsg_sub: Creating...
azurerm_network_interface.Terranic: Creating...
azurerm_linux_virtual_machine.terravm: Creating......
Apply complete! Resources: 9 added, 0 changed, 0 destroyed.
Outputs:
...
Subnet_Name = "internal"
vnet_CIDR = 192.168.0.0/16
Subnet_CIDR = 192.168.10.0/24
vnet_dedicated_security_ingress_rules = toset([
{…
"access" = "Allow"
"description" = "RDP-HTTP-HTTPS ingress trafic"
"destination_port_ranges" = toset([
"22",
"3389",
"443",
"80",])
]
SSH_Connection = ssh connection to instance TerraCompute ==> sudo ssh -i ~/id_rsa_az centos@’’ <---- IP not displayed due to bug with az provider
private_ip = "192.168.10.4"
public_ip = ""
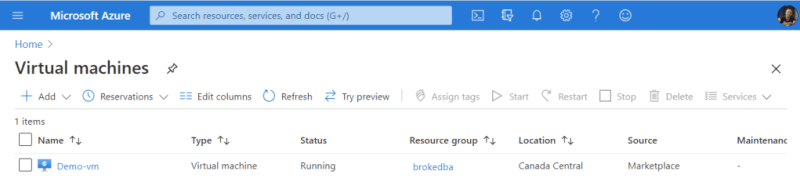
- Once the instance is provisioned, juts copy the public IP address(i.e 52.191.26.102 ) in chrome and Voila!
- Although a bug of azurerm_linux_virtual_machine doesn’t show the public IP , just go to the console and copy past the IP into your browser
- You can also tear down this configuration by simply running terraform destroy from the same directory
Tips
- You can fetch any of the specified attributes in outputs.tf using terraform output command i.e:
$ terraform output SSH_Connection
ssh connection to instance TerraCompute ==> sudo ssh -i ~/id_rsa_az centos@ ’’
- Terraform Console: Although terraform is a declarative language, there are still myriads of functions you can use to process strings/number/lists/mappings etc. There is an excellent all in one script with examples of most terraform functions >> here
- I added cloud-init files for different distros you can play with by adapting var.user_data & var.OS
Differences between Azure/AWS & things I wish azure kept simple
- Network In Azure every subnet is a public subnet because as soon as you associate a public IP to a Vm’s VNIC, you’ll magically have internet access. Internet gateway is not needed here because system routes are taking care of that.
- CIDR range in azure is slightly larger than aws ( from /8 to /29 ).
- ID Azure doesn’t provide regular alpha numeric IDs for its resources but a sort of path based identification (see below)
$ SUBNET ID
/subscriptions/xx/resourceGroups/my_group/providers/Microsoft.Network/virtualNetworks/MY-VNET/subnets/My_SUBNET
- Naming Case insensitive but unique, a resource group can’t have 2 resources of the same type with the same name
- Bummer: I wish azure kept one terraform resource to create vms instead of having one for Linux and one for Windows since v2.0. This implies that we will have extra blocks/modules if we want to do both in one stack instead of leveraging loops. The classic one is not handy for Linux either.
CONCLUSION
- We have demonstrated in this tutorial how to quickly deploy a web server instance using terraform in Azure and leverage Cloud-init to configure the vm during the bootstrap .
- Remember that all used attributes in this exercise can be modified in the file.
- Route table and internet gateway setting in our code were replaced by the Public IP and VNICs
- I found azure vm spinning time so slow comparing to AWS or OCI, not sure if it’s it’s regional thing
- Improvement: I will look to improve the compute.tf code to allow both windows & Linux type of resource to provision. Validate that userdata works for windows too, unlike on az cli. Another improvement can be reached in terms of display of the security rules using formatlist . stay tuned
Thank you for reading!
Originally published at http://www.brokedba.com.





Top comments (0)