Welcome
Here's a quick introduction/presentation so you know what this is and why you're reading it. I'm Merk, a Software Engineering student that really likes reverse engineering (among other things).
What we're doing
In this series we will attempt to reverse engineer and complete challenges from the Reversing.kr website. In this particular case, we will be reversing the password of the challenge Easy Crack.
Reconnaissance
We're given a Windows executable and must crack it. Using DIE we can see it is a 32-bit executable and is not packed.
![]()
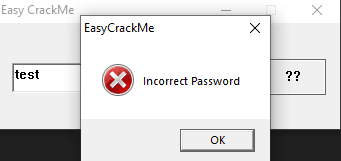
When we execute it, a window pops up. It asks for input and has a button.

If we input an arbitrary string such as "test", an error dialog appears telling us the password is incorrect.
Knowing what we know, there exist several ways to tackle this challenge:
-
We could straight up patch the program so that the flow of execution skips the error message and goes to the right place
- This would be the cracker's way; not the reverser's, and would also not give us points since we don't reverse engineer the password ;)
-
We could look for string references
- Given that the executable doesn't seem to have any protections, and knowing the string "Incorrect Password", this method can prove to be useful
-
We could set a breakpoint on the Win32 API GetDlgItemText/A/W
- Because of how the program window looks, it is very likely that the Dialog reads its content using this function
x64dbg
We'll test our luck looking for string references. Let's fire up x64dbg, attach the executable and look for strings in the main module.
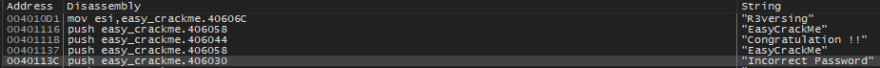
And there we have some meaningful strings:
- "Congratulation !!" - the good boy
- "Incorrect Password" - the bad boy
Addressing the references, we can take a look at the program logic in graph mode. The first thing we see is a comparison between the start of our input (ESP+4) and the character 'E'. So our string must commence with the letter 'E'.
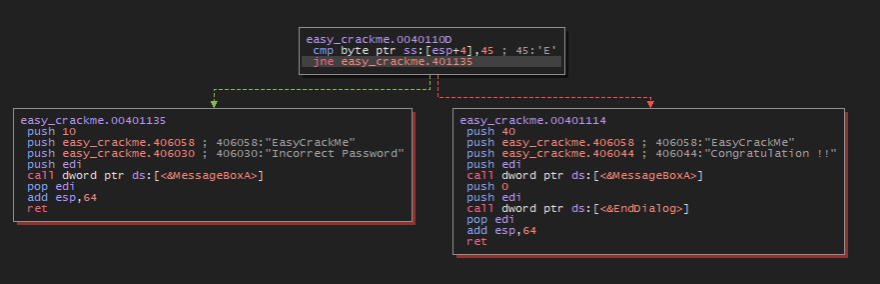
Also, further up in the code, right bellow the call to the API GetDlgItemTextA (which we inferred right) is a comparison between ESP+5 and 'a', which means our second character must be the letter 'a'.
![]()
(This is what ESP is currently pointing to, that's why ESP+4 is the first letter and ESP+5 is the second)
![]()
So we know that the first two letters of the password are "Ea".
There also exists a function within the program that constantly returns 1, and makes the flow end up executing the bad boy. Taking a look inside, we can see it compares [EBP+C] which contains "5y" with our string starting from the third letter, which is stored in ESI. This is done via "repe cmpsb", which essentially compares several characters.
![]()
(ESI is pointing at the third character of our input, in this case the first 'a' in 0x19F7F2)
![]()
(EBP+C points to the characters "5y")
![]()
This means that our third and fourth letters must be "5y".
Changing our input to "Ea5y" will now make the function return 0, and the flow of execution gets further into the program.
![]()
If we keep looking further down in the code, x64dbg hints us that at some point in the code, the string "R3versing" is stored in ESI before some comparisons.
![]()
Without thinking much, we could infer that the correct input will be "Ea5y R3versing". However, we still missed something.
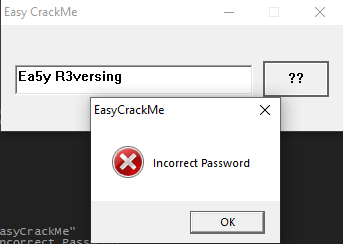
Stepping through the comparisons, we can quickly see that there shouldn't be a space between "Ea5y" and "R3versing".
'R' is compared with our input ' ', which means we probably need to remove the space.
![]()
![]()
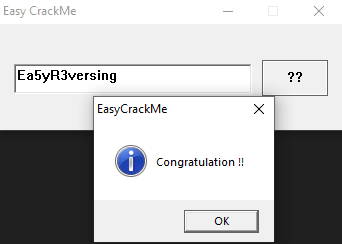
Therefore, we input 'Ea5yR3versing' and hit the button one last time.



Oldest comments (1)
If you want download the easy crack software like photoshop crack mac or any other software then visit the kabli store. It is perfect for you.