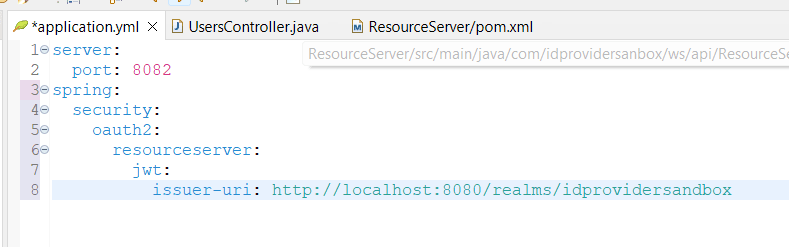
To let the Spring Boot app know where to find the auth server,
set the uri of issuer, in application properties of the boot app:
server:
port: 8082
spring:
security:
oauth2:
resourceserver:
jwt:
issuer-uri: http://localhost:8080/realms/idprovidersandbox
jwk-set-uri: http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/certs
The jwk-set-uri property contains the public key that the server can use for this purpose. The issuer-uri property points to the base Authorization Server URI, which can also be used to verify the iss claim as an added security measure.
The above link can be found from auth server:
http://localhost:8080/realms/idprovidersandbox/.well-known/openid-configuration
{
"issuer":"http://localhost:8080/realms/idprovidersandbox",
"authorization_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/auth",
"token_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/token",
"introspection_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/token/introspect",
"userinfo_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/userinfo",
"end_session_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/logout",
"frontchannel_logout_session_supported":true,
"frontchannel_logout_supported":true,
"jwks_uri":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/certs",
........
"pushed_authorization_request_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/ext/par/request",
"mtls_endpoint_aliases":{
"token_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/token",
"revocation_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/revoke",
"introspection_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/token/introspect",
"device_authorization_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/auth/device",
"registration_endpoint":"http://localhost:8080/realms/idprovidersandbox/clients-registrations/openid-connect",
"userinfo_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/userinfo",
"pushed_authorization_request_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/ext/par/request",
"backchannel_authentication_endpoint":"http://localhost:8080/realms/idprovidersandbox/protocol/openid-connect/ext/ciba/auth"
}
}
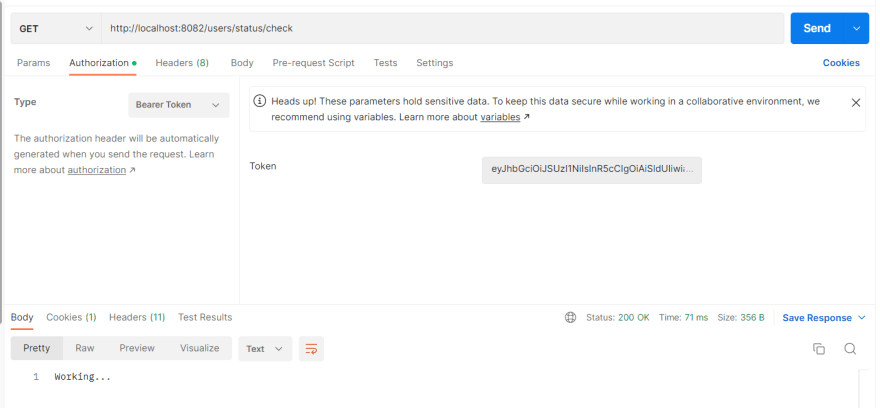
After pointing to, use the manual way to obtain an access token and embed it in the request (which was 401 unauthorised). Now the requested URL is responding without errors:
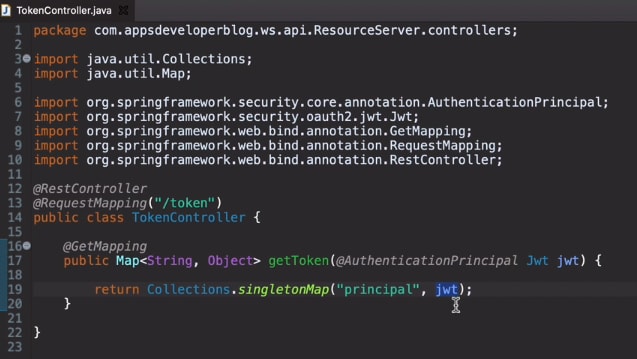
To further explorer what is in the token, you can also use an Annotation called AuthenticationPrincipal, which can provides a Jwt collection which contains the "principal" (currently authenticated user's claims). Using a Rest endpoint to experiment this:
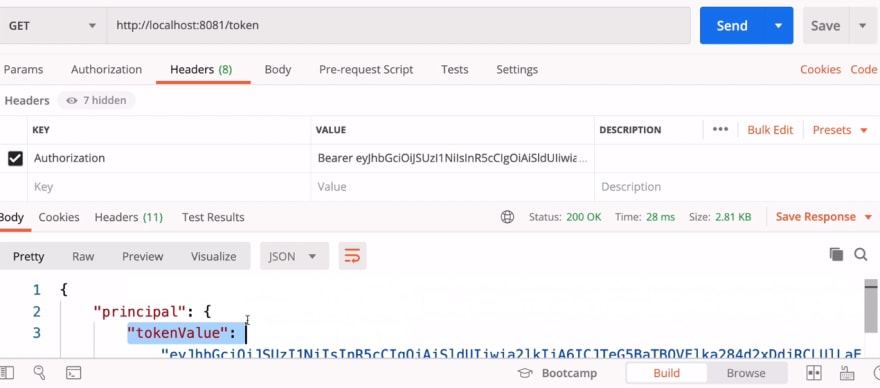
Now the principal details in token can be accessed by code:


Top comments (0)