
What is BeReal?
BeReal is a new social media app which is said to be more “in the moment” compared to conventional social media platform...
For further actions, you may consider blocking this person and/or reporting abuse


Learnt a lot, thank you :) I used mitmproxy to try this out for myself, however it seems like it complains about it already being finalised..?



This is the request:
Is it trying to cancel the upload?
Keep in mind that the "upload command" for the requests that succeeded was to upload and finalize.
Do you have any ideas? :D
Awesome! That looks to me like you are trying to resend a request which has already been sent. You need to make sure you intercept it before it has a chance to reach the server. You can do this by adding the domain to the "intercept" input.
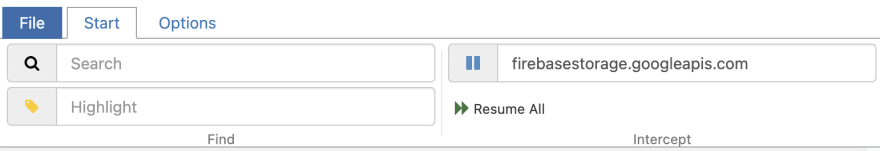
Once it is paused you can edit the payload and press the green play button to execute the request. Let me know how you get on!
That would be the app trying to retry. You can see in the image below that the first PUT request succeeds but then it tries again and fails with HTTP 400 "Upload has already been finalized" as seen in my first comment.
But if you add the domain into the intercept filter then both of those requests should have been paused. I noticed that the app seems to try every request twice. You only need to let one of them through after editing.
That way doesn't work for me. It keeps re-requesting a new upload (POST)
But either way those requests should also be paused, no?
Yes they are paused but the photo does not go through on the client and it is probably expecting different upload IDs
Here you can see the modified PUT request returns a success but the client requests to start another 3 uploads, 2 of them being the one just returned as a success.
That
PUTrequest looks ok to me actually. Looks like a decent amount of data was sent and it was a200status. If you close and open the app now, is your custom RealMoji there?Nope. I’m trying to send a BeReal photo though, but you said it acts relatively the same. If I close and open the app, it just tries to upload again.
Ah but if you post a normal BeReal then you upload two pictures (front and back) so the app is making two consecutive requests followed by a bereal API request to say where the photos are stored. Have a play around with sending a RealMoji and see if you can get that to work!
Ah yeah, a RealMoji worked with the script. However both manually and automatically I can't upload a fake normal BeReal. What am I getting wrong?
Okay, so:
"This software allows me to see all unencrypted HTTPS requests made between my phone and the internet"
So this means that BeReal is NOT consistently using HTTPS/SSL for everything it does, and if so, why not? As it's one of the most basic 'rules' out there ...
And if they did, wouldn't that make MITM right away impossible?
Or am I completely missing something here?
P.S. but I suppose that that's exactly what the MITM proxy (which obviously needs to be installed in the phone itself) does, somehow: insert itself into the "network stack" BEFORE the beginning of the HTTPS/SSL endpoint? Obviously the BeReal devs do use HTTPS for their stuff ... cool article!
That is correct, the proxying of the connection via mitmproxy results in the HTTPS connection only being established from the intercepting computer!
I think your question is irrelevant, since it's the ability to "fake" their API invocations. As long as you can create something that mimics the client, you can pretend to be a client, while you're really not. Since the BL is implemented mostly on the client for simplicity reasons, this implies you can bypass their business logic, right ...?
For instance, if we imagine something similar for Facebook ...
With stuff that allows you to dynamically build CRUD queries on the client, such as Firebase, GraphQL, and PostgREST, the above becomes a legitimate concern, and although I realise it is possible to fix and secure, by using "schemas" or "resolvers", and in addition adding "trigger functions" (or whatever) - At this point you've lost most of the simplicity these things gives you, or ...?
Am I wrong here or ...?
@oscar ...?
Yes my question was based on a misunderstanding ... and we agree that if an app has its business logic on the client, it's vulnerable to these kinds of attacks and to abuse - the reason why BeReal gets away with it is because nobody's going to jump through hoops and put in that much effort to fake their actions in the app, it's just too trivial, so the incentive isn't really there :)
Thx mate. Just checking. I'm not always correct, so it helps to confirm my assumptions every now and then 😊
Awesome post! Very interesting. I did not know it was possible to intercept and modify http requests, great to know :D
So am I right that a BeReal user could (if they wanted) install this proxy on their phone themselves and then go on and manipulate how the app works for them? Just goes to show how fragile and unsafe it is to put "business" logic in the frontend ... but well, I'm sure that the makers of BeReal don't really care, they're probably laughing all the way to the bank :)
I enjoyed reading your article and wanted to try it out, but unfortunately, I encountered an error message: "Client TLS handshake failed. The client does not trust the proxy's certificate for cdn.bereal.network. OpenSSL Error: ('SSL routines', '', 'sslv3 alert certificate unknown')."