Originally published at ssojet
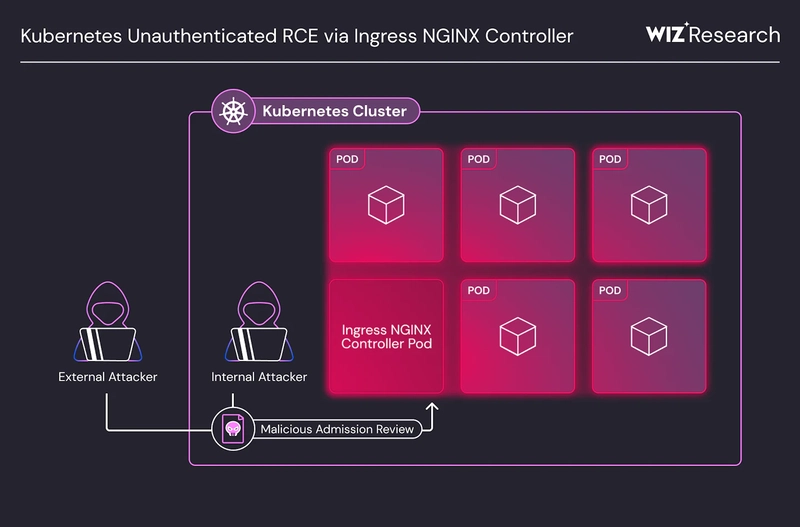
Recent vulnerabilities discovered in Ingress NGINX Controller for Kubernetes have raised significant security concerns. Dubbed "IngressNightmare," these vulnerabilities could allow attackers to gain unauthorized access to Kubernetes clusters, which has been a critical risk for over 6,500 clusters, including those of Fortune 500 companies.
Image courtesy of Help Net Security
Vulnerabilities Identified
- CVE-2025-1974: This vulnerability has a CVSS score of 9.8 and allows attackers on the Pod network to exploit configuration injection vulnerabilities via the Validating Admission Controller feature of ingress-nginx. This situation can lead to complete cluster takeover without requiring administrative access. The risk is exacerbated by the fact that many workloads in cloud environments have access to the Pod network.
For further details, refer to the Kubernetes blog.
- CVE-2025-1097: This vulnerability allows for configuration injection via the "auth-tls-match-cn" Ingress annotation, which can potentially lead to arbitrary code execution in the context of the ingress-nginx controller.
- CVE-2025-1098: Similar to the previous one, this vulnerability enables configuration injection through the "mirror-target" and "mirror-host" Ingress annotations, which can also facilitate arbitrary code execution.
- CVE-2025-24514: This issue arises from the "auth-url" Ingress annotation and can enable attackers to inject configuration into NGINX, leading to arbitrary code execution.
- CVE-2025-24513: An improper input validation vulnerability that could lead to directory traversal within the container, which may result in denial-of-service (DoS) or limited disclosure of sensitive information.
For a detailed breakdown of these vulnerabilities, you can view the advisory from Wiz.
Mitigation Strategies
To protect Kubernetes clusters from these vulnerabilities, it is crucial to implement immediate remedial actions. The following strategies are recommended:
- Upgrade Ingress NGINX: Ensure that the ingress-nginx is updated to versions 1.12.1, 1.11.5, or 1.10.7. These versions include patches for all identified vulnerabilities.
- Limit Access to Admission Controller: Restrict access to the admission controller to only the Kubernetes API Server. This will reduce the risk of unauthorized access through exposed endpoints.
- Disable Validating Admission Controller Temporarily: If upgrading is not feasible immediately, consider disabling the Validating Admission Controller feature. Be sure to reinstate it post-upgrade to maintain the security benefits it provides.
For guidance on implementing these mitigations, refer to the AWS security bulletin and the Google Cloud advisory.
Importance of Robust Security Solutions
In light of these vulnerabilities, it is imperative for organizations to have robust identity and access management solutions in place. Implementing secure Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Passkey solutions can significantly enhance security in Kubernetes environments.
SSOJet offers an API-first platform that ensures effective user management and secure authentication. Our services include directory synchronization, SAML, OIDC, and magic link authentication to provide a comprehensive security framework for enterprises.
Explore our services or contact us at SSOJet to learn how we can enhance your organization's security posture.


Top comments (0)