Originally published at ssojet
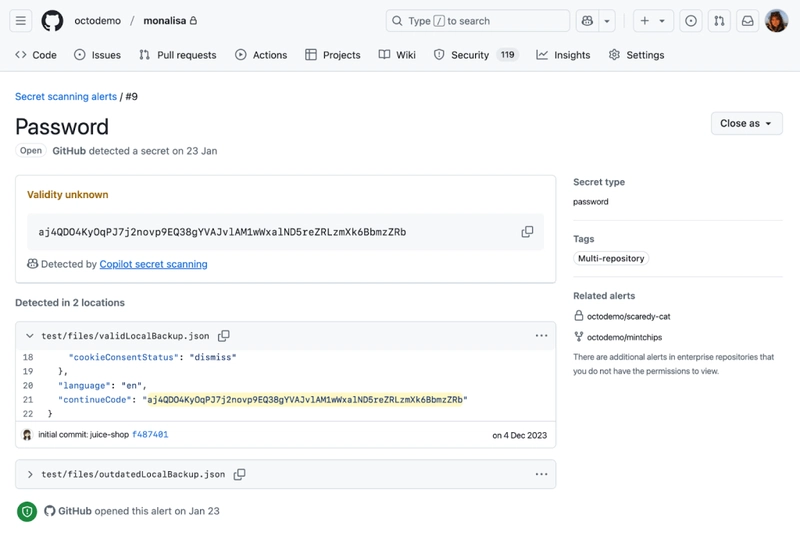
GitHub has launched an AI-powered secret scanning feature within Copilot that significantly enhances password detection in code while reducing false positives. This innovative feature leverages context analysis to improve the detection of leaked passwords and is part of GitHub Secret Protection. Traditional regex methods often miss varied password structures and generate numerous false alarms, which can overwhelm development teams.
According to a GitHub blog post, the new system analyzes the usage and location of potential secrets to minimize irrelevant alerts. Sorin Moga, a senior software engineer, noted that this marks a new era in platform security, where AI not only assists in development but also safeguards code integrity.
A key challenge identified during the private preview was the model's difficulty with unconventional file types and structures. GitHub initially employed "few-shot prompting" with GPT-3.5-Turbo to guide detection. To overcome early challenges, GitHub enhanced its evaluation framework by incorporating feedback from participants and diversifying test cases. They used GPT-4 to generate new test cases based on learnings from existing open-source repository alerts, improving precision and recall metrics.
Image courtesy of GitHub
New Vulnerability in GitHub Copilot and Cursor
A significant vulnerability affecting GitHub Copilot and Cursor has been identified, exposing severe supply chain risks for developers using these AI-assisted coding tools. This vulnerability, termed the "Rule Files Backdoor," allows attackers to manipulate AI platforms into generating malicious code that appears legitimate.
Ziv Karliner, CTO & Co-Founder of Pillar Security, highlighted that this attack vector weaponizes the AI itself, making it crucial for developers to scrutinize AI-generated suggestions. The attack does not require special privileges and can infiltrate repositories through compromised configuration files. This issue poses a serious risk, as malicious code can blend seamlessly with legitimate code, bypassing security checks.
To mitigate this risk, developers are advised to audit existing rules, implement validation processes for AI configuration files, and utilize detection tools to identify suspicious patterns in rule files. Moreover, GitHub has emphasized the importance of reviewing AI-generated code, particularly for unexpected additions.
Renaming Secret Scanning Alerts
As of March 11, 2025, alerts for non-provider patterns and Copilot-detected passwords have been categorized as "generic" instead of "experimental." This change applies to alert filters and the secondary inbox in alert views. GitHub aims to streamline the detection process, ensuring users can manage alerts in accordance with their organization's policies.
Detection for these secret types is available for repositories with a GitHub Advanced Security license, and users can enable it through repository settings or enterprise code security configurations.
For more information on securing repositories, refer to the documentation on secret scanning.
AI-Driven SOC Automation
Security Operations Centres (SOCs) face an overwhelming volume of alerts, often leading to analyst burnout and inefficiency. GitHub’s AI-powered secret scanning integrates AI-driven secret detection to streamline SOC operations. By analyzing how and where credentials are used, the system prioritizes real risks while minimizing noise.
The integration of context-aware AI and deterministic rules allows GitHub to enhance SOC workflows, auto-triaging alerts and integrating with SIEM and SOAR tools. This improved process reduces false positives by 94%, allowing analysts to focus on genuine threats.
Additionally, GitHub's Copilot Secret Scanning aims for rapid response to credential leaks, an essential aspect of maintaining security integrity within development workflows.
Finding Leaked Passwords with AI
GitHub's Copilot secret scanning feature utilizes AI to detect generic passwords in codebases, addressing the limitations of traditional approaches. The system analyzes context, such as the usage and location of potential secrets, which enhances its ability to deliver relevant alerts critical for maintaining repository security.
The development process revealed challenges with unconventional file types. Initial prompts struggled, leading to a reevaluation of the approach, which ultimately included a robust offline evaluation framework. This framework allows for a more diverse set of test cases, leading to improved detection accuracy.
By refining their testing methodologies and leveraging technologies like GPT-4, GitHub has significantly boosted its precision and recall metrics, thereby enhancing the detection capabilities of Copilot secret scanning.
GitHub continues to focus on collaboration, resource management, and user feedback to refine its secret scanning capabilities, ensuring it remains a critical component of application security.
For enterprises seeking to enhance their security protocols, implementing secure SSO and user management is crucial. SSOJet offers an API-first platform featuring directory sync, SAML, OIDC, and magic link authentication, tailored for your needs. Explore our services at SSOJet or contact us for more information.


Top comments (0)