When we start learning AWS, the first thing we have to learn is networking concepts. Once you open an AWS account, you have to create your network space or you can use the default VPC.
If you want hands-on practice on these services, you can open a free tier account with AWS and explore many products without spending a single penny. Some services are chargeable and their rates vary a lot depending on a particular region.
NOTE: In this article NAT gateway is chargeable. Still, I would suggest you use AWS ESTIMATE for other services as well.
In this article, you will understand the main networking concepts: VPC, Subnets (private, public), CIDR, Elastic IP, Route Table, NAT Gateway, Internet Gateway, Security Group, NaCl
This will be our final outcome
What is VPC?
VPC is way to logically separated resources when you’re working in AWS. You will be creating resources inside VPC so it won't be accessible from outside unless we give permission. These resources can communicate with only this VPC resources.
We will be using VPC wizard templates to create VPC. We are using a template which will be creating VPC with private and public subnet (will explain in some time) for us.
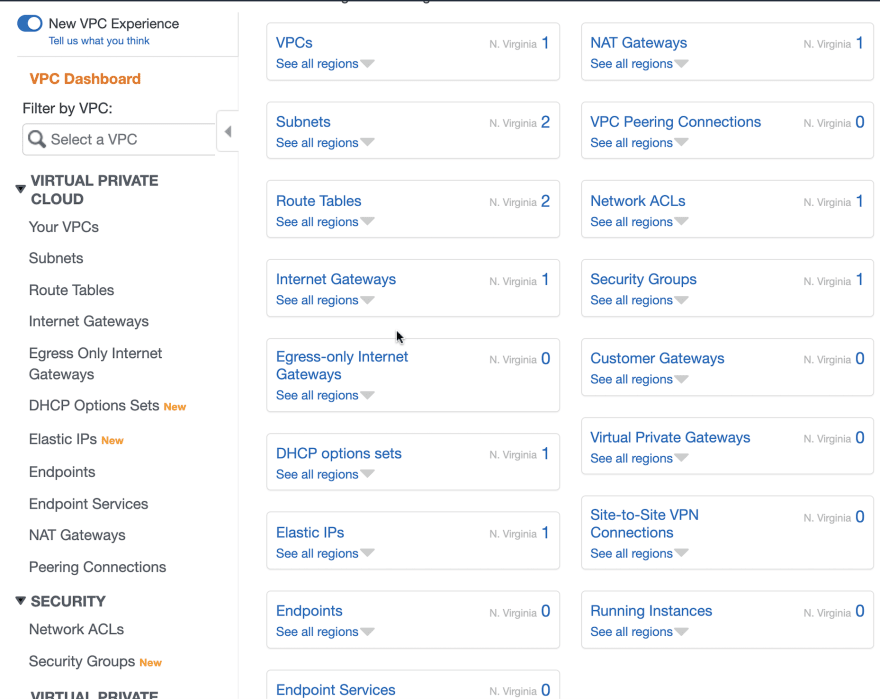
Go to Launch VPC Wizard:
VPC Creation:
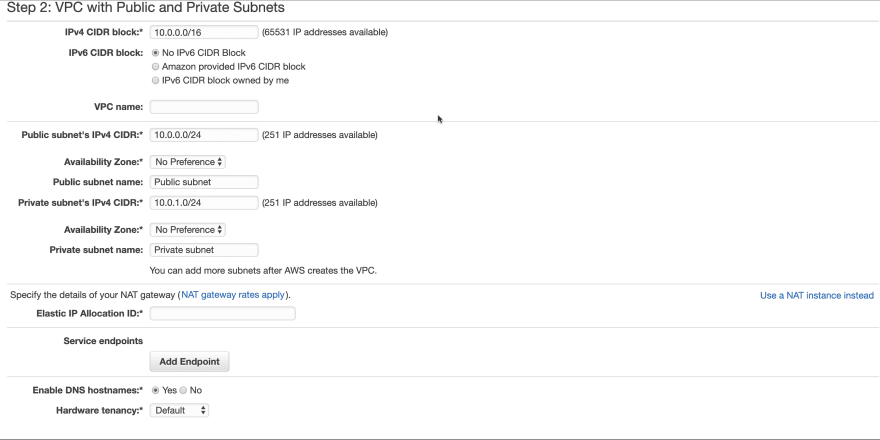
If you will see the above image, VPC requires a range of IP address. This range is configured using CIDR. In the example, we will be using 10.0.0.0/16 (means 65531 unique address) which can be used for a lot of AWS resources.
You can use this CIDR calculator for calculating the IP address range
What is Subnet?
A subnet is a smaller piece of network. We create different subnets based on our networking rules and our availability zones needs.
In our example, we will be creating 2 subnets: private and public
Public subnet traffic is routed to an internet gateway so resources of this subnet can be accessible from the internet. It will always have public IP for communication
Internet Users → dev.to → Public IP
Private subnet doesn’t have a route to the internet gateway.
Example: Our website server which needs to be accessible via the internet so it will be in Public Subnet. Our database servers will be in private subnet which should not be accessible via the internet.
In an example, we are giving 251 IP address to both subnets and us-east-1 availability zone. You can choose based on your resources need and their availability demand.
You can choose different availability zones for different subnets
What is Internet Gateway?
An AWS resource that gives subnet access to the public internet. We have chosen public subnet template so AWS will create this for us and attach it to the public subnet.
You can attach internet gateway to any subnet and it will become Public Subnet. Don't try to attach to your database servers 😜. It can cause security issues for your database servers.
I will show you internet gateway usage later in the article.
What is NAT Gateway or NAT instance?
We have seen that private subnets can't be accessible from the internet. Sometimes resources inside private subnet need internet access.
Example: Database servers need patching and need to download some packages from the internet. In this case, we will have to use a NAT gateway. It will always have public IP to communicate with the internet.
We can use NAT instances as well. We just need to attach this to our private subnet. Then private subnet resources will communicate to the internet through NAT gateway.
We have to select the public subnet at time of creating NAT Gateway. Each NAT gateway is created in a specific Availability Zone and implemented with redundancy in that zone.
Multiple availability zones private subnets can share this NAT gateway.
If the NAT availability zone is down, other availability zones resources will lose internet access. Ideally, we should create NAT for each availability zone and resources use the NAT gateway in the same Availability Zone.
Check this for more details: NAT USAGE
Check out the difference between NAT Gateway and NAT Instance
What is Route Table?
A routeing table is what decides how traffic flows between subnets. Route table would need to set up in order to define where services can access.
Internet gateway attachment, NAT gateway attachment, transient gateway everything goes into route table for defining the route rules.
Whenever we create VPC, AWS create default main route table for us. If we have to create a private subnet and attach a NAT gateway, we have to create a custom route table and attach it to a specific subnet.
We are using Public/private subnet template in our example, AWS will create 2 route table
for us. One is the main route table and another is a custom route table.
You can go to any subnet and check which route table is attached to that subnet.
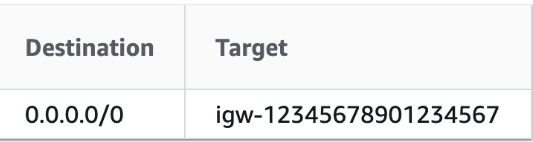
In our example, go to public subnet and check the routeing table:
Select the public subnet → Scroll to end → Find route table column
You will find that it is using the main route table and using internet gateway route for accessing the internet. This internet gateway Id can be different.
You can check the private subnet route table as well. Go to private subnet, it will use a custom route table and be using NAT for accessing the internet. Whenever private subnet needs internet access,
we will have to add NAT in the subnet route table.
Whenever you need custom routing for your subnets, you will have to create a custom route table and attach it to a specific subnet.
What is an Elastic IP?
Elastic IP addresses are used by AWS to manage its dynamic cloud computing services. Whenever we create instances in a public subnet, it will get different public IP. If we need public IP's which needs to fixed for some purpose, we have to allocate Elastic IP.
Example:
We use Elastic IP's for creating a NAT gateway.
We need to communicate with any third party API and they can allow only fix number of public IP from the client. In this case, we will have to allocate an Elastic IP and assign it to the resource.
Now we come to the security part of VPC:
What is a Security group?
A security group is a set of networking rules that are applied to a resource. A security group is responsible for defining what traffic (based on port and protocol) can enter or leave certain resources.
Suppose you want to give permission to specific IP's to access the resource on a specific port. You need to create a security group with that permission and attach it to the resource. Multiple resources can use the same security group.
Inbound Rules → Incoming traffic rules of resource
Outbound Rules → Outgoing traffic rules of resource
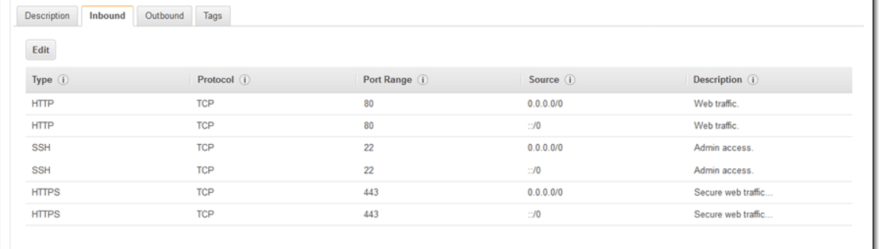
Go to any security group → Inbound rules (Incoming traffic rules)
In this above image, we have chosen only 3 ports for incoming traffic. For database instances, you will open a specific port to only limited IP's. All those rules go into a security group.
What is NACL?
Network ACLs control inbound and outbound traffic for your subnets.
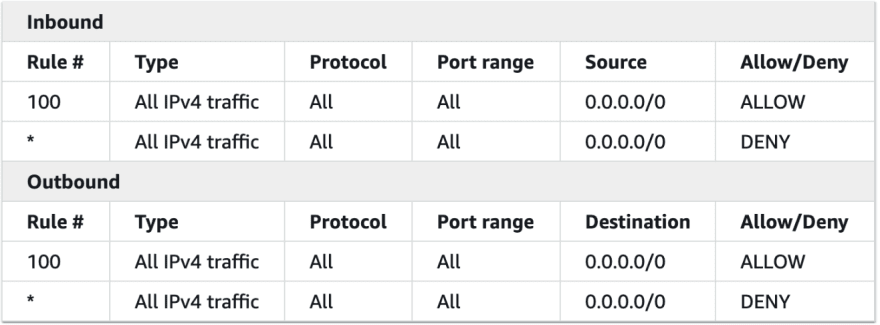
These are default rules which come with default NACL:
If we have to allow permission for specific IP's or specific port on the subnet level, we have to use NACL.
As per AWS documentation:
We recommend that you use network ACLs sparingly for the following reasons: they can be complex to manage, they are stateless, every IP address must be explicitly opened in each (inbound/outbound) direction, and they affect a complete subnet.
More details on NACL vs Security group differences
In VPC dashboard, you will see other services as well like VPN, endpoints, endpoints service, transient gateway, VPC peering which we have not covered in this article. If you want to know more about these services, let me know. I will try to write those about as well.
Conclusion:
That was a lot. Hope you were able to understand these networking concepts. Now you can easily create infrastructure in AWS with this knowledge.
Thanks a lot for reading. Let me know if you find this useful. It will motivate me to write more articles.




Top comments (2)
Great article Pankaj! Pretty useful and comprehensive overall on most of the popular AWS people are always talking about :) thanks for sharing
Thanks for kind words, Lucas :)