title: [Kubernetes] About Kubernetes
published: false
date: 2023-11-30 00:00:00 UTC
tags:
canonical_url: http://www.evanlin.com/til-k8s-environment-secret/
---

## Preface:
Recently, during a chat, we discussed that when managing accounts and passwords within Kubernetes, we all know to use [Kubernetes Secret](https://kubernetes.io/docs/concepts/configuration/secret/) instead of [Environment Variables](https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/). But what are the differences in terms of security? I decided to look up some information and summarize it from books:
## Reference Book Content
### \*\*[Kubernetes Security\*\*](https://learning.oreilly.com/library/view/kubernetes-security/9781492039075/) [Liz Rice](https://learning.oreilly.com/search/?query=author%3A"Liz%20Rice"&sort=relevance&highlight=true), [Michael Hausenblas](https://learning.oreilly.com/search/?query=author%3A"Michael%20Hausenblas"&sort=relevance&highlight=true)

You can pass environment variables into containers at runtime. This means you can take the container image (code) and configure it according to the scenario it is running in. In Kubernetes, “ordinary” environment variables can be specified directly in the pod YAML or via a [ConfigMap](http://bit.ly/2Q8Hlkb). But be careful: including secret values in YAML files that you check into code control means those secrets are accessible to the same people who can see the source code.
To mitigate this, Kubernetes also supports the [secret](http://bit.ly/2xCI7Pz) resource, which can be [passed into a pod as an environment variable](http://bit.ly/2xO0Syz). Your pod spec or ConfigMap YAML refers to the secret resource by name rather than directly to the secret value, so that it’s safe to put that YAML under code control.
From Kubernetes 1.7 onwards, you can add [node authorization](http://bit.ly/2IfD2k1) to ensure that unauthorized kubelets cannot access confidential information.
### [Kubernetes Secrets Management](https://learning.oreilly.com/library/view/kubernetes-secrets-management/9781617298912/) By [Andrew Block](https://learning.oreilly.com/search/?query=author%3A"Andrew%20Block"&sort=relevance&highlight=true), [Alex Soto](https://learning.oreilly.com/search/?query=author%3A"Alex%20Soto"&sort=relevance&highlight=true)

### [2 An introduction to Kubernetes and Secrets](https://learning.oreilly.com/library/view/kubernetes-secrets-management/9781617298912/OEBPS/Text/02.htm#heading_id_10)
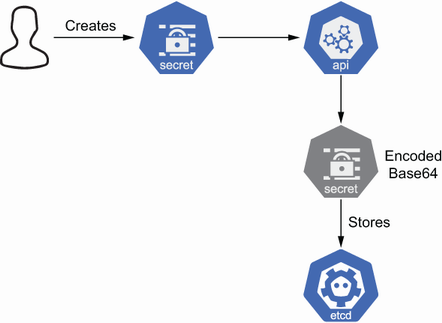
As discussed in chapter 1, one of the big differences between Secrets and ConfigMaps is how data is stored inside `etcd`. Secrets store data in Base64 format; ConfigMaps store data in plain text.
### 2.4.2 Secrets are mounted in a temporary file system
A Secret is only sent to a Node if there is a Pod that requires it. But what’s important is that a Secret, even though it is mounted as a volume, is never written to disk but in-memory using the `tmpfs` file system. `tmpfs` stands for temporal filesystem, and as its name suggests, it is a file system, where data is stored in volatile memory instead of persistent storage. When the Pod containing the Secret is deleted, the kubelet is responsible for deleting it from memory as well.
### Level of Danger / Hacking Methods
#### Environment Variables /
export
declare -x GREETING_MESSAGE="Hello Anna" ①
declare -x HOME="/"
declare -x HOSTid="greeting-demo-deployment-5664ffb8c6-2pstn"
...
#### Secret placed in a temporary file
mount | grep tmpfs
tmpfs on /dev type tmpfs (rw,nosuid,size=65536k,mode=755)
tmpfs on /sys/fs/cgroup type tmpfs (ro,nosuid,nodev,noexec,relatime,mode=755)
tmpfs on /etc/sec type tmpfs (ro,relatime) / ①
...
ls /etc/sec ②
greeting.message
cat /etc/sec/greeting.message ③
Hello Anna
### Utilizing external structures
### Summary
- Kubernetes clusters consist of a master node and optional worker nodes.
- The current state of any Kubernetes resource and the cluster is stored in the `etcd` instance.
- We discussed deploying applications to Kubernetes.
- We introduced using ConfigMaps to configure applications externally, either as environment variables or as files.
- Secrets are not very different from ConfigMaps in terms of construction and usage.
### To strengthen ConfigMap, you can refer to this article
#### [Proper Secret Management with Kubernetes ConfigMaps](https://www.trendmicro.com/en_us/devops/23/f/kubernetes-configmaps-secret-management.html)


Top comments (0)