The use case
This post comes from the fact that the token used by Codepipeline to connect to Github to download the source code of the website has expired. Hence, the automation “push and update the website” is not working. Here’s the error:
Let’s view how the secret is stored into cloudformation, and how codepipeline can connect.
The secret stack
The cloudformation stack is quite easy. It does not have any hard dependency on other stacks, and it’s used both to download code for dev and prod website.
{
"AWSTemplateFormatVersion": "2010-09-09",
"Parameters": {
"GithubOAuthTokenParameter": {
"Description": "Github OAuth Token",
"NoEcho": "true",
"Type": "String"
}
},
"Resources": {
"GithubOAuthToken": {
"Properties": {
"Name": "GithubOAuthToken",
"SecretString": {
"Ref": "GithubOAuthTokenParameter"
}
},
"Type": "AWS::SecretsManager::Secret"
}
}
}
The next part of the post is dedicated on how to create and use this cloudformation template
Create stack
aws cloudformation create-stack --stack-name secrets-stack `
--template-body file://secrets-stack.json `
--parameters file://secret-token-sample.json
The secret-stacks.json refers to the code just shown before, and the secret-token-sample.json file is written with the parameter syntax. Here’s a sample:
[
{
"ParameterKey": "GithubOAuthTokenParameter",
"ParameterValue": "sample value",
"UsePreviousValue": false
}
]
Check stack resources
aws cloudformation list-stack-resources `
--stack-name secrets-stack `
--query 'StackResourceSummaries[\*].[LogicalResourceId,ResourceType,ResourceStatus]'
The output is quite straightforward (the stack was already created when I re-ran the command)
[
[
"GithubOAuthToken",
"AWS::SecretsManager::Secret",
"UPDATE\_COMPLETE"
]
]
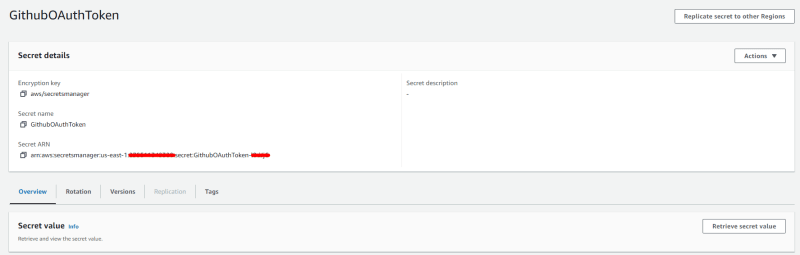
This is how the resource appears in AWS ui, once created (the output of the CLI is just the ARN of the stack).
The actual value (the one that’s expired) of the token can be viewed by clicking on the retrieve secret value button. Time to move to Github and generate the new token
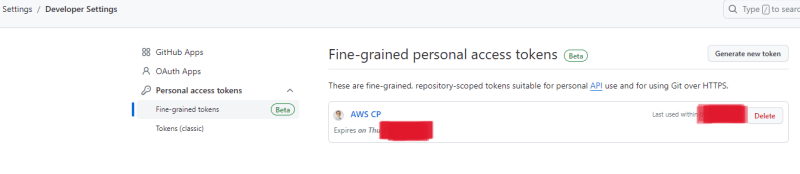
Github account setting
While logged in into the Github profile where the repository with the code is kept, go to settings page, and then move to developer settings. Click on “fine grained tokens”:
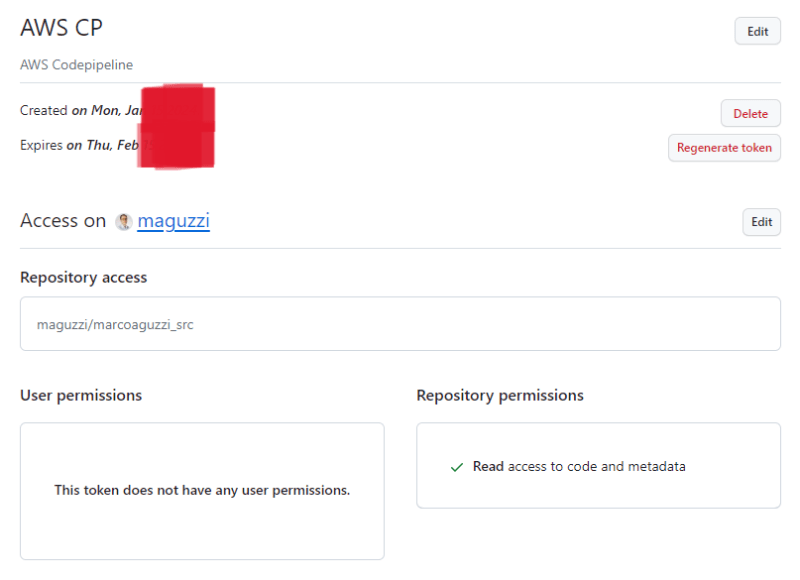
Clicking on AWS CP shows the token settings. It can be seen that it grants read-only access to one repository and no user permission. Of course the actual key cannot be seen anymore, it’s only possible to regenerate it.
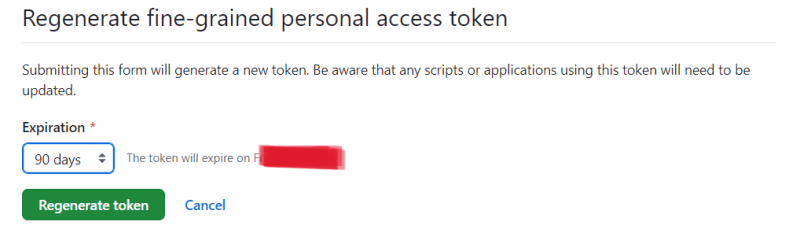
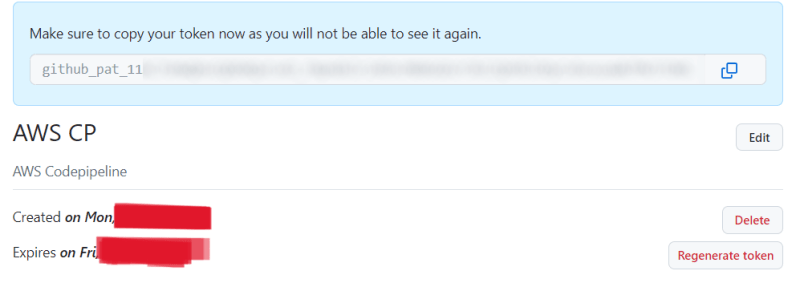
Click on regenerate token
Confirm the token regeneration. The token will be visile only for it to be copied
Cloudformation update
Now that the token is in our hands, we can update the cloudformation stack by putting the token in the place of “sample value” shown before and then issuing
aws cloudformation update-stack --stack-name secrets-stack `
--template-body file://secrets-stack.json `
--parameters file://secret-token-sample.json
Let’s check the stack after the update
Check stack
aws cloudformation describe-stacks --stack-name secrets-stack `
--query '[Stacks[0].[StackName,StackStatus,Parameters],Stacks[0].Outputs]'
Output
The null value is because there are no outputs to be used by other stacks. Please note that in the template file GithubOAuthTokenParameter is reported as “NoEcho”: “true”. In this way the real token won’t be shown neither in output logs nor in the Cloudformation ui.
[
[
"secrets-stack",
"UPDATE\_COMPLETE",
[
{
"ParameterKey": "GithubOAuthTokenParameter",
"ParameterValue": "\*\*\*\*"
}
]
],
null
]
The token is then actually used in code pipeline
And the cloudformation code hosting the reference to the token is:
"Configuration": {
"Branch": { "Ref": "RepoBranchParameter" },
"OAuthToken": "{{resolve:secretsmanager:GithubOAuthToken}}",
"Owner": {"Ref":"RepoOwnerParameter" },
...
},
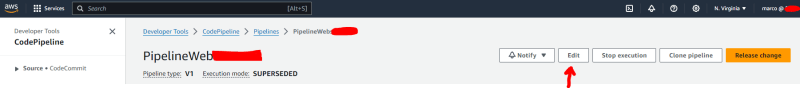
Refresh and restart the pipeline
Navigate the AWS UI in Codepipelines, select the pipeline, click edit pipeline:
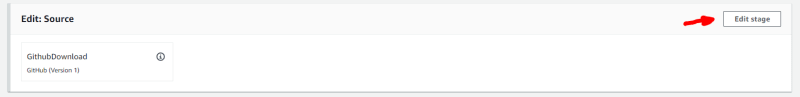
Search for the button “Edit stage” on the source stage:
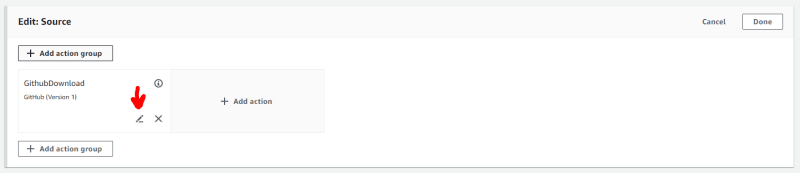
Click it, and then search for the pencil in the “Github download” box:
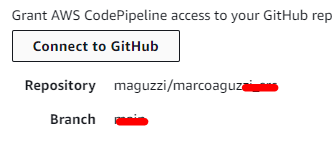
Even if repository and branch are selected, click on “Connect to Github”
A pop-up will appear asking the oauth confirmation, click it
Insert repository and branch in their respective fields (a popup should appear, letting you select)
Scroll to the bottom of the page and click done to save (actually refresh) the changes. Now you can trigger a new pipeline and it should connect with the repo and dowload the code.
Next time I’ll check how to automate the pipeline refresh via clouformation CLI.
Thanks for reading it all!






Top comments (0)