In this article, we'll take a friendly stroll through the fundamental concepts of AWS IAM, breaking down the jargon and providing clear, step-by-step insights for beginners. From understanding what IAM is and why it's crucial to AWS security, to creating your first IAM user and group, we'll guide you through the IAM dashboard and policies like a trusted friend. Get ready to demystify IAM for beginners, making your first steps into the world of secure AWS access both enjoyable and empowering.
Introduction
AWS Identity and Access Management (IAM) is a cloud-based identity and access management service that helps you securely control access to AWS services and resources. You can use IAM to create and manage users and groups, and to assign permissions to them. You can also use IAM to control who can access your AWS resources and what actions they can perform.
IAM is an important part of any AWS security strategy. By using IAM, you can help to protect your AWS resources from unauthorized access and use.
Here are some of the key benefits of using IAM:
Granular Access Control:
IAM provides fine-grained control over who can access AWS resources and what actions they can perform.
Enables the principle of least privilege, reducing the risk of unauthorized access or accidental misuse.Securely Managing Identities:
IAM allows the creation and management of AWS users, groups, and roles, providing a structured approach to identity management.
Centralized control over user access helps organizations maintain a robust security posture.Supports Multi-Tiered Environments:
Ideal for organizations with complex, multi-tiered environments by allowing the creation of roles with specific permissions for different components and services.Integration with AWS Services:
IAM seamlessly integrates with various AWS services, facilitating secure access to resources like S3, EC2, RDS, and more.
IAM Components: Users, Groups, Roles, Policies
IAM Users:
Definition: IAM users represent individual entities—typically people or applications—that interact with AWS services.
Key Points:
- Each user has unique credentials (username and password or access keys).
- Users are the entities to which permissions are assigned to perform actions on AWS resources.
- IAM users are the foundation for managing access within an AWS environment.
IAM Groups:
Definition: IAM groups are collections of IAM users. Instead of attaching policies to individual users, policies are attached to groups.
Key Points:
- Simplifies permission management by allowing you to apply policies to a group of users with similar access needs.
- Users can belong to multiple groups, streamlining access control for different roles or projects.
- Changes to group memberships automatically reflect in the permissions of associated users.
Note:
Users and Groups:
- Users are people within your organization, and can be grouped.
- Groups only contain users, not other groups.
- Users don't have to belong to a group, and can belong to one or more groups, inheriting the group's permissions.
IAM Users & Groups Hands On
Let's walk through a practical example illustrating how IAM Users and Groups work together in a typical AWS scenario:
Scenario: Creating and Managing Users on AWS IAM
Step 1: Creating IAM Users:
Task: Set up individual access for five developers – Jamie, Allen, Mark, Ross, Chris
Action:
- In the AWS Management Console, navigate to IAM.
- Create IAM users for Jamie, Allen, Mark, Ross and Chris, each with unique credentials.
Step 2: Organizing Users into Groups
Task: Simplify access management by creating groups for different development roles.
Action:
- Create three IAM groups: "Developers", "Operations" and "QA".
- Add Allen to the "Developers" group, Chris to the "Operation" group.
- Since Mark and Ross belong to multiple groups, Add Mark to the "Developers" and "QA" groups, Ross to the "Operations" and "QA" groups.
- Jamie don't have a group.
- Assign additional permissions to the "Developers" group for elevated access.
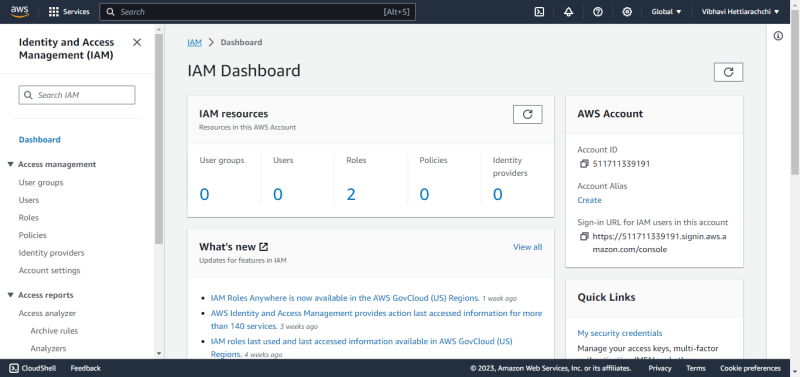
IAM Dashboard
This dashboard allows users to manage their identity and access to their AWS account. It provides a clear and concise overview of the IAM resources in the account, and it provides easy access to tools and resources for managing access to AWS resources.
AWS IAM dashboard is divided into two main sections:
- IAM resources: This section shows a summary of the IAM resources in the account, including users, groups, roles, and policies.
- Access management: This section provides links to tools and resources for managing access to AWS resources, such as the Access Analyzer and the IAM Identity Center.
Users Dashboard
Below dashboard provide summary of all the IAM users in this AWS account, including their user names, paths, groups, last activity MFA status, password, age and user groups.

This dashboard is currently showing that there are no IAM users in this account. To create a new IAM user, you can click the "Create User" button.
Step 01- Specify User Details
The journey begins by specifying the details of the user you're creating. Think of this step as introducing your user to the AWS environment. You'll need to provide a unique username for the individual, ensuring it's something easy to remember and identify. Additionally, you can include other information like the user's email address to enhance account management.

To complete the process of creating the new IAM user, the user would need to click the Next: Permissions button to proceed to the next step of the workflow.
Step 02- Set Permissions
Next, it's time to decide what your user can and cannot do within the AWS ecosystem. This is like assigning roles and responsibilities. You might want a user to have full administrative access, or perhaps only limited permissions for specific tasks. It's a bit like handing out keys – you decide which doors your user can open and which ones stay locked.
To set permissions for an IAM user or group:
- Select the IAM user or group that you want to set permissions for.
- Click the Attach policies button.
- Select the managed policies or inline policies that you want to attach.
- Click the Attach policies button.
You can also use the Permissions section to review and edit the permissions that are granted to the IAM user or group that is selected.
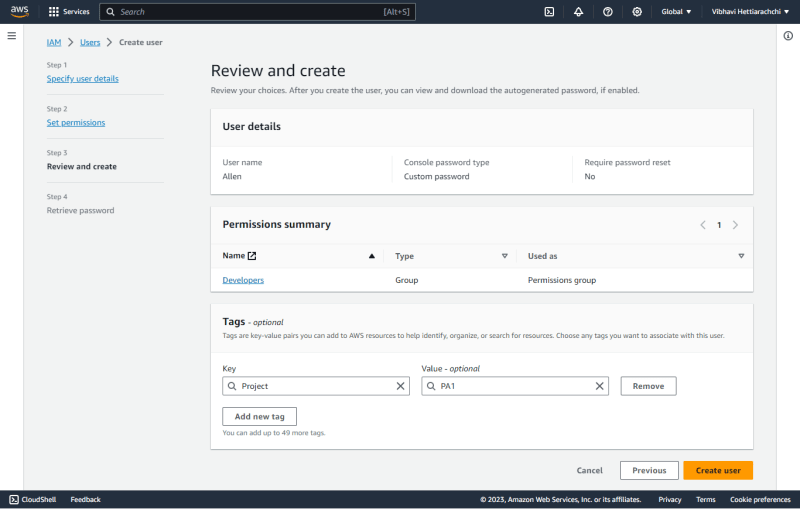
Step 03- Review and Create
Once you've set the ground rules, take a moment to review your choices. This is your chance to double-check that you've given the user the right level of access and that their details are accurate. Think of it as a final run-through before you officially welcome your user into the AWS world.
Step 04- Retrieve Password
Just like getting the keys to a new house, you need to give your user a way to access their AWS account. AWS will generate a temporary password that you can share with the user. They'll need to change this password the first time they log in, ensuring that only they have access to their account.
Step 05- User Created Successfully
Congratulations, you've successfully created an AWS IAM user! Think of this as the moment your user officially moves in. They now have their own corner of the AWS cloud, with access levels and permissions tailored to your specifications. This step is a pat on the back for completing the process and ensuring that your user is ready to start using AWS.
IAM Policies
IAM policies are the set of rules that govern what users are permitted to do within the AWS environment. Think of them as the guidelines and boundaries you establish for your team members in the workplace. These policies are incredibly flexible, allowing you to grant or restrict access at a granular level.
Policy Components
Effect: This is like the decision-making part of the rule. It can be either "Allow" or "Deny." If it's "Allow," the specified actions are permitted. If it's "Deny," those actions are forbidden.
Action: These are the specific tasks or operations users are allowed or denied. Imagine it as the job description for each team member. For example, you might allow someone to launch new EC2 instances but deny them the ability to delete resources.
Resource: This defines the AWS resources to which the policy applies. It's like specifying which projects or areas of the office the rules apply to. For instance, you might grant permissions to manage S3 buckets but only for a specific bucket.
Condition: Conditions are like situational requirements. They allow you to set conditions under which the policy takes effect. It's akin to saying a task can only be done during certain hours or under specific circumstances.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:Get*",
"iam:List*",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy"
],
"Resource": "*"
}
]
}
This policy is quite permissive, allowing the specified IAM actions on any AWS resource. The actions include generating credential reports, accessing service last accessed details, getting information (using "Get*"), listing information (using "List*"), and simulating custom and principal policies. It's important to note that such broad permissions should be carefully considered and assigned only to trusted entities or administrators who require extensive access for managing IAM resources.
Policy Attachments
Policies are attached to IAM users, groups, or roles, specifying the permissions for those entities. It's similar to assigning roles or responsibilities within a team. Each team member has their own set of permissions outlined by the policies attached to their account.
IAM MFA
IAM MFA, which stands for Multi-Factor Authentication, is a security feature that adds an extra layer of protection to AWS accounts. It requires users to present two or more separate forms of identification before they can access their AWS resources. In the case of IAM, MFA helps to mitigate the risk of unauthorized access, even if a user's password is compromised.
Key Components of IAM MFA
Factors of Authentication:
- Password: The traditional password or PIN.
- MFA Device: A physical or virtual device that generates time-based one-time passwords (TOTPs) or other authentication codes.
Enabling IAM MFA:
- IAM MFA can be enabled for individual IAM users. Users must then associate an MFA device, such as a hardware token or a virtual device (e.g., a mobile app) with their IAM account.
- The MFA device generates temporary authentication codes that are required in addition to the user's password for authentication.
Types of MFA Devices:
- Hardware MFA Token: A physical device that generates authentication codes. It's often a key fob-like device.
- Virtual MFA Device: An app on a mobile device (e.g., Google Authenticator or AWS Virtual MFA app) that generates authentication codes.
IAM Roles
IAM roles are like backstage passes in the AWS world. Instead of assigning permissions directly to users, roles are designed to be assumed by trusted entities, whether they are AWS services, users, or applications. These roles come with a set of permissions, defining what the entity can and cannot do during their performance.
IAM Security Tools
IAM Security Tools in AWS play a crucial role in ensuring the security and compliance of your AWS environment. Two such tools are IAM Credential Report and IAM Access Advisor.
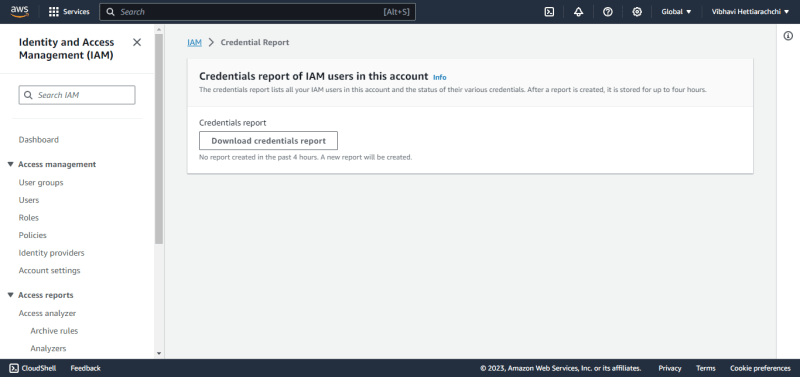
IAM Credential Report
The IAM Credential Report is a tool that provides a detailed snapshot of the status and attributes of IAM users and their respective access keys within an AWS account. It includes information about when access keys were last rotated, the creation date of access keys, and whether they are active.
The IAM credential report can be generated from the AWS Management Console, the AWS CLI, or the AWS API. The report is generated in a CSV file that you can download and view.
You can use the IAM credential report to identify IAM users with expired passwords, inactive access keys, or disabled MFA devices. You can then take steps to remediate these issues, such as requiring users to change their passwords, enabling access keys, or enabling MFA devices.
The IAM credential report can also be used to audit your IAM users and to identify any potential security risks. For example, you can use the report to identify IAM users with access keys that are older than 90 days or IAM users who do not have MFA enabled. You can then take steps to remediate these risks, such as requiring users to rotate their access keys or enable MFA devices.
Key Features
- Access Key Details: The report includes information about each IAM user's access keys, such as their status (active or inactive), creation date, and last rotation date.
- Password Status: It also provides information about the password last used status for IAM users, helping in identifying inactive or unused accounts.
- Security Audit: IAM Credential Report is valuable for security audits and compliance checks, assisting in identifying and addressing potential security risks.
IAM Access Advisor
IAM Access Advisor is a tool that provides insights into the last-accessed information for IAM roles and helps in determining which permissions are actually being used. It assists in making informed decisions about adjusting access permissions based on usage patterns.
Key Features
- Last Accessed Information: Access Advisor provides details about when an IAM role or policy was last accessed, offering visibility into which permissions are actively utilized.
- Unused Permissions: It helps identify IAM roles or policies with unused or rarely used permissions, allowing for the refinement of access policies.
- Policy Optimization: Enables organizations to optimize policies by aligning them with actual usage patterns, reducing the risk of over-permission.
Shared Responsible Model for IAM
The AWS Shared Responsibility Model outlines the division of security responsibilities between AWS (the cloud service provider) and the customer. This model helps users understand which security aspects are managed by AWS and which aspects are the responsibility of the customer.
IAM Summary
In the dynamic landscape of AWS, think of Identity and Access Management (IAM) as the superhero cape that ensures only the right folks get backstage passes to your cloud world. IAM isn't just a gatekeeper; it's your security maestro, orchestrating a symphony of access controls and permissions. Picture it as your backstage manager, assigning roles and responsibilities, ensuring that everyone has the right access tunes to play. IAM doesn't just stop at controlling who can access your AWS resources; it's your trusted companion for securely organizing and managing the entire crew, from rockstar developers to backstage operations.
And guess what? IAM doesn't shy away from complexity. In the world of multi-tiered environments, it's your secret sauce, allowing you to create roles tailored for each component and service, ensuring everyone gets their moment in the spotlight. Integrating seamlessly with AWS services, IAM becomes your backstage pass to S3, EC2, RDS, and more, making sure your team can rock the stage securely.
The IAM dashboard is your command center, offering a DJ booth for managing user identities and access to AWS. Users, Groups, Roles, and Policies—think of them as the VIP passes, creating an ensemble for precise control over who can access what. Through hands-on scenarios, IAM comes to life, with users and groups taking center stage in a practical dance of access management.
But IAM isn't just about the techy stuff; it's your trusted security sidekick. Policies become your workplace guidelines, ensuring everyone knows the moves and follows the script, reducing the risk of unauthorized access. IAM MFA? It's like having a bouncer at the entrance, making sure only those with the secret handshake get in—even if someone spills the password beans.
IAM Security Tools, including IAM Credential Report and IAM Access Advisor, step in as your backstage crew, providing behind-the-scenes insights into user credentials and access patterns. It's your security team whispering in your ear, "Hey, there's a potential security risk backstage, let's fix it before the show."
And let's not forget the Shared Responsibility Model—it's like IAM's tour manager, clearly defining who handles what in the security concert. IAM emerges not just as a tool but as a dynamic, indispensable member of your AWS band, ensuring that your cloud performance is not just secure but a chart-topper in the world of cloud security symphonies.
Thanks for embarking on this IAM adventure with me!🚀✨ Feel free to revisit this guide anytime you need a refresher, and stay tuned for more tech journeys ahead! Happy exploring! 🌐🔐











Top comments (0)