Purpose of this post
The purpose of this post is to show you what kind of encryption Microsoft uses for encrypting storage accounts by default and how you can use CMK (Customer Managed Keys) to encrypt your storage accounts.
Encryption using Microsoft managed keys
By default, if you don't specify the type of encryption for your storage accounts while creation, Microsoft uses server-side encryption (SSE) to automatically encrypt your data. This is applied to any storage account regardless of its tier. Microsoft uses Microsoft managed keys for this type of encryption. This is the default option from Microsoft.
Encryption using Customer managed keys (CMK)
While you can continue to let Microsoft handle the encryption of your data, customers can use their own keys to handle data encryption. This type of encryption is called CMK enabled encryption. Here are some of the benefits of using CMK over default Microsoft managed keys.
- Customers have control over the keys used to encrypt their data.
- Microsoft rotates their keys as per their own compliance requirements. Customers using CMK can meet security compliance requirements.
- CMK keys are stored in customer's key vault, giving control over where these can be used.
- Same CMK keys can be used to encrypt multiple storage accounts.
Implementing CMK for storage accounts
In this section, we'll see how to implement CMK for storage accounts.
Examining default encryption for a storage account
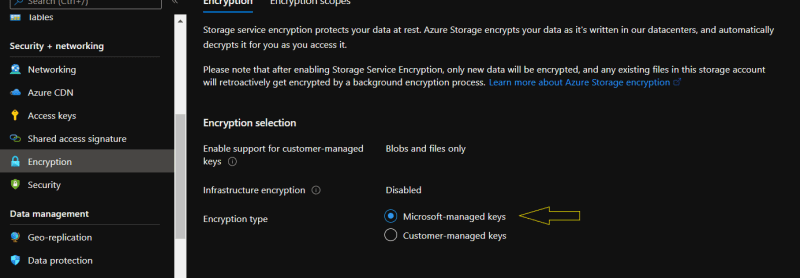
Before implementing CMK, lets see how Microsoft encrypts storage account with Microsoft managed keys. While creating a storage account in the 'encryption' section, you can specify whether you would like go with default encryption or a customized encryption using CMK.
Once its created, you can see the type of encryption used by storage account as shown below:
If you would like to use CMK, you can do so, however the a new key has to be created and stored in Azure Key Vault and used for encryption. We'll see that in the next section.
Enabling CMK for a storage account
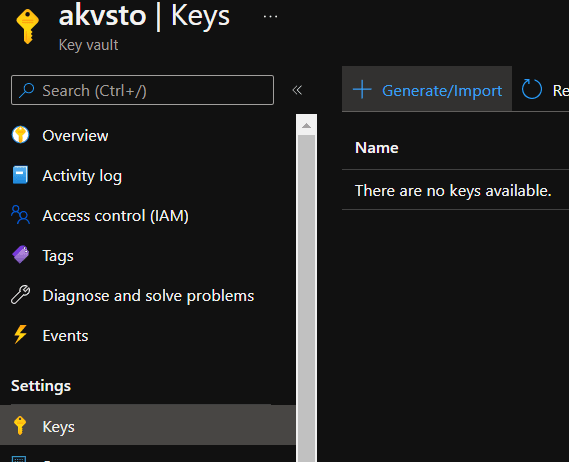
1.Create a new key in Azure key vault in the same region as storage account
2.Click on 'generate/import' under keys as shown below:
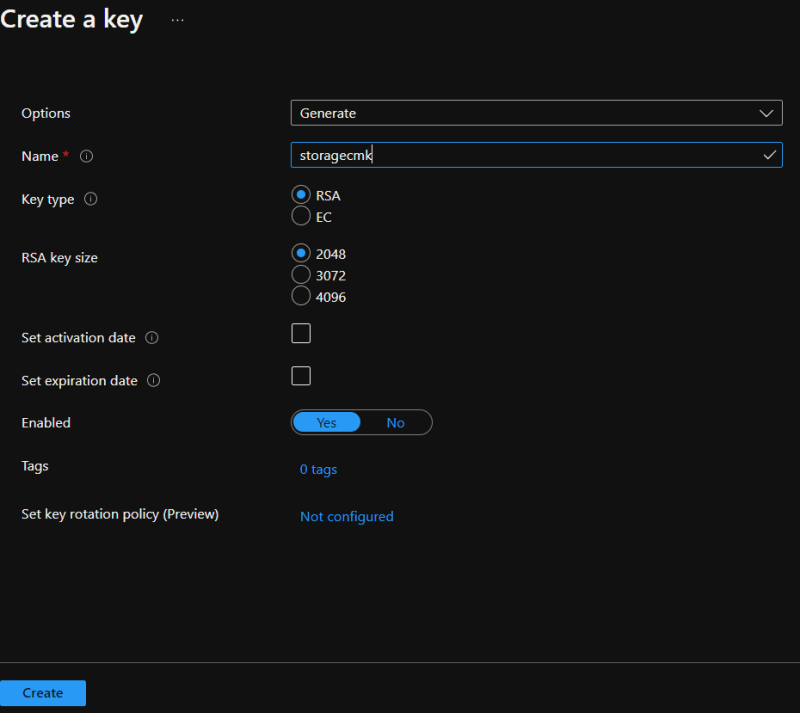
3.Give key a name and leave everything else to default as shown below.
4.Go back to storage account and encryption section.
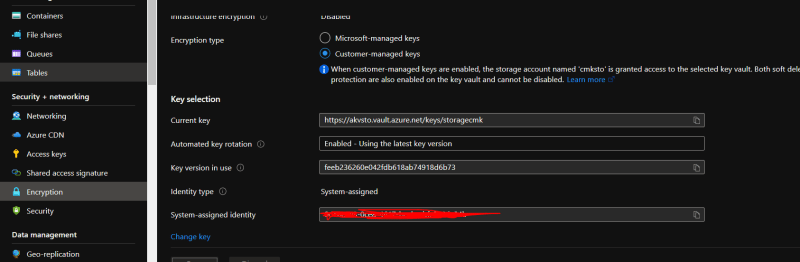
After selecting the key it should show as following. Click 'save' to apply the settings
Once applied it would show that it is now using CMK for storage encryption.
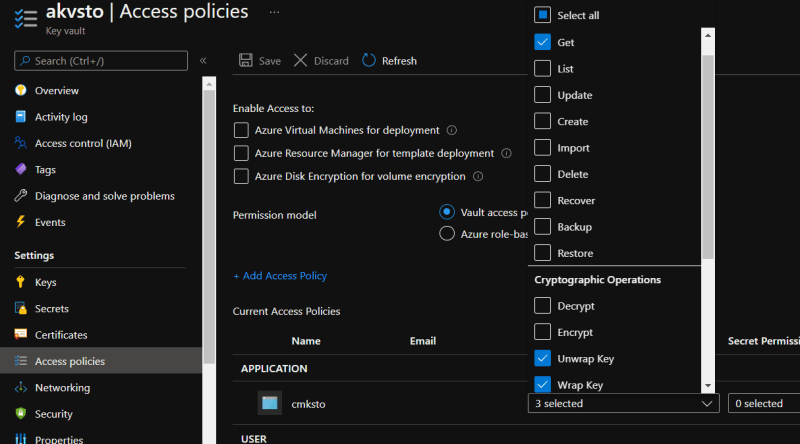
As a part of this applying CMK encryption for storage accounts, it also creates a system assigned managed identity to the storage account and same is granted permission Azure Key Vault with 'get', 'wrap' and 'unwrap' permissions for the managed identity of storage account.
In this blog post, we have seen how to use customer managed keys for storage account encryption.
This brings us to the end of this blog post. Hope you enjoyed reading it.
Happy Learning!!!






Top comments (0)