Introduction
In our digital world, safeguarding web applications is of paramount importance. Imagine your application as a secure vault, and servlet security as the lock that guards it. In this blog post, we'll delve into servlet security step by step and explore the power of various authentication methods that ensure the safety of both our applications and users.
Getting Started with Servlet Security
Imagine having created an impressive web application. Now, how can you ensure that only authorized individuals access it? This is where authentication comes into play – think of it as a secret passphrase granting you access to an exclusive club. Your application wants to confirm your identity before granting you entry.
To implement the first three authentication methods, you'll need to add the following to your tomcat-users.xml file, usually found in Tomcat's conf directory:
this will act as security realm (authentication pprovider)
<role rolename="ADMIN"/>
<role rolename="CUSTOMER"/>
<role rolename="CLERK"/>
<user username="safvan" password="123" roles="CUSTOMER"/>
<user username="user1" password="123" roles="CLERK"/>
<user username="admin" password="^*&^*&hghsd" roles="ADMIN,CUSTOMER"/>
Different Approaches to Verification
1. BASIC Authentication: Simplicity at Its Best
Consider BASIC authentication as a friendly doorman who asks for your name and password. It's like saying, "Hey, I recognize you! Come on in." However, bear in mind that this method is suitable for non-sensitive information.
In BASIC Authentication, the client sends a request containing the username and password in plain text. The server responds with the requested information or an error. The syntax for BASIC Authentication is as follows:
Authorization: Basic <base64-encoded(username:password)>
Since the username and password are base64 encoded, this method is not recommended for real-world applications due to security concerns.
2. DIGEST Authentication: A Secure Puzzle
Next, we have DIGEST authentication. Imagine sending a secret message that gets scrambled before being sent. The recipient deciphers it and verifies your identity. It's like a puzzle only you and the server can solve, ensuring your secrets remain secure.
DIGEST Authentication is a more intricate form of authentication. The client initiates a request to the server, which responds with a nonce (a one-time-use number) and requests the client's authentication. The client then responds with the nonce and an encrypted version of the username, password, and realm (a hash). The server validates the client hash against its own hash, and either provides the requested information or returns an error if the hashes don't match.
To configure DIGEST Authentication in a Java Servlet application, add the following to your web.xml file:
<security-constraint>
<web-resource-collection>
<!-- Define your secure URLs here -->
<url-pattern>/secure-path/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>ROLE_MANAGER</role-name>
</auth-constraint>
</security-constraint>
<login-config>
<auth-method>DIGEST</auth-method>
<realm-name>myrealm</realm-name>
</login-config>
Keep in mind that DIGEST Authentication should be used over a secure connection due to its vulnerabilities.
3. FORM Authentication: Your Personalized Access Card
Now, envision FORM authentication as a personalized invitation to an exclusive event. You fill in your details on the invitation card, and the app welcomes you stylishly. Developers have the flexibility to craft an appealing login page and manage errors gracefully.
FORM Authentication involves sending user credentials within the body of a POST request. This method is widely used for web applications:
<h1 style="color:red;text-align:center;">Login Page</h1>
<form action="j_security_check" method="POST">
<table border="1" bgcolor="cyan" align="center">
<tr>
<td>Username:</td>
<td><input type="text" name="j_username"></td>
</tr>
<tr>
<td>Password:</td>
<td><input type="password" name="j_password"></td>
</tr>
<tr>
<td colspan="2"><input type="submit" value="Login"></td>
</tr>
</table>
</form>
4. CLIENT-CERT Authentication: The Digital Passport
Have you heard of CLIENT-CERT authentication? It's like having a digital passport. Instead of a password, you present your digital certificate – a unique ID only you possess. The server verifies it, and upon confirmation, grants you access. This method is ideal for confidential transactions, such as sharing credit card information.
CLIENT-CERT Authentication involves the client providing a digital certificate for authentication. The server then validates this certificate to ensure its legitimacy.
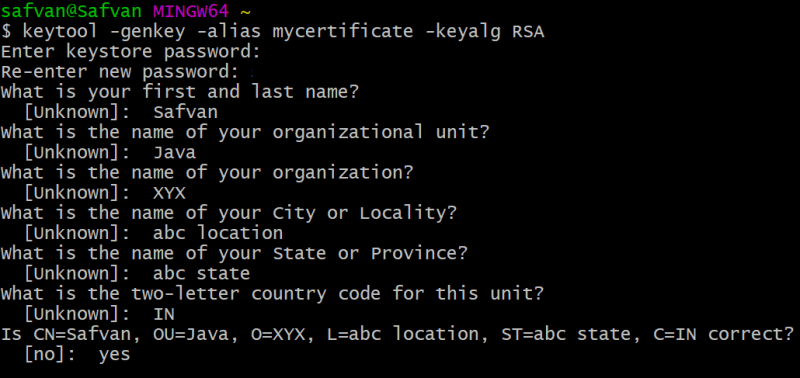
To create Digital certificate using JDK supplied tool (key tool)
To configure CLIENT-CERT Authentication, use the keytool tool provided by the JDK to generate a digital certificate using the RSA algorithm. Here's a sample of how to set it up in the server.xml configuration file:
<Connector
protocol="org.apache.coyote.http11.Http11NioProtocol"
port="8443"
maxThreads="150"
SSLEnabled="true">
<SSLHostConfig>
<Certificate
certificateKeystoreFile="/path/to/mykeystore.keystore" <!-- Default: {user.home}/.keystore -->
certificateKeystorePassword="keystore_password"
type="RSA"/>
</SSLHostConfig>
</Connector>
Blending Modes for Enhanced Security
The exciting news is that you don't have to stick to just one authentication method. With servlet security, you can combine and match these authentication methods, similar to adding various toppings to a pizza. By using BASIC, DIGEST, FORM, and CLIENT-CERT methods in harmony, you can create a robust shield for your application.
Essential Considerations
While these authentication methods provide trustworthy protection, they do have limitations. For instance, CLIENT-CERT requires server support for HTTPS. Therefore, ensure your digital fortress possesses the necessary tools.
Drawbacks of Manual Authentication and Authorization
When it comes to manually securing a servlet, there are certain downsides to be aware of:
- Limited Protection: Manual methods might lack advanced security features offered by specialized security frameworks.
- Complexity: Implementing manual security can be intricate and prone to errors, especially when managing multiple user roles and permissions.
- Maintenance Challenges: Manual security can lead to tightly coupled code, complicating maintenance and updates.
- Inconsistent Implementation: Manual approaches can result in inconsistent security measures across different parts of the application.
- Human Errors: Mistakes during implementation can introduce vulnerabilities.
- Lack of Centralized Management: Managing user accounts, roles, and permissions manually becomes complex as the application scales.
- Limited Auditing: Manual methods might lack comprehensive auditing and logging features.
- Scalability Issues: As the application grows, manual management becomes more complex and can impact performance.
- Expertise Dependence: Manual security relies on developer expertise, which can vary.
- Compliance Challenges: Meeting regulatory requirements can be tough without dedicated security frameworks.
- Integration Limitations: Manual methods might not integrate



Top comments (0)