Emails have become a vital mode of communication in today’s world. However, with the increasing instances of email phishing and spoofing attacks, ensuring email communication’s security has become more critical than ever. One way to achieve this is by using DMARC, which stands for Domain-based Message Authentication, Reporting, and Conformance. DMARC is an email authentication protocol that helps to prevent email spoofing and phishing attacks. In this article, we will discuss DMARC reports and guide you on how to read and analyze them effectively. We will begin by explaining what DMARC reports are and their significance in email security. Then, we will provide you with a step-by-step guide on how to read and analyze DMARC reports. So, let’s get started!
Understanding DMARC Reports
DMARC reports are documents that are based on XML, which give detailed information about email messages that were sent on behalf of your domain. These reports are created by the DMARC receiving servers and are then sent back to the DMARC sending domain. DMARC reports play a crucial role in ensuring email security and preventing phishing and spoofing attacks.
DMARC reports contain important details about the email messages sent from your domain, such as the date and time of the message, the recipient’s email address, and the result of the message. They also provide information about the email authentication process, including DKIM (DomainKeys Identified Mail) and SPF (Sender Policy Framework) authentication. The authentication results show whether the email message passed or failed the authentication checks.
Why DMARC Reports are Important
DMARC reports play a crucial role in maintaining email security and preventing phishing and spoofing attacks. They enable you to analyze and identify any unauthorized use of your domain name, thus helping prevent phishing attacks. Through DMARC reports, you can:
Spot phishing and spoofing attacks: DMARC reports contain details about email messages that didn’t pass the authentication checks. By examining these reports, you can quickly spot any phishing or spoofing attacks that may try to use your domain name.
Keep track of email delivery: DMARC reports provide data about messages that were successfully delivered, and those that weren’t. By monitoring these reports, you can keep tabs on any delivery issues and take action to fix them.
Enhance email authentication: DMARC reports provide information on DKIM and SPF authentication. By going through these reports, you can detect authentication problems and take steps to strengthen the email authentication process.
How to Read and Analyze DMARC Reports:
Reading and analyzing DMARC reports can be a challenging task, especially for those who are new to DMARC. However, by following the steps below, you can effectively read and analyze DMARC reports:
Step 1: Access DMARC Reports
The first step in reading and analyzing DMARC reports is to access the reports. DMARC reports are sent to the email address specified in the DMARC record. You can also access DMARC reports by using DMARC reporting tools such as SimpleDMARC DMARC Checker
Step 2: Understand DMARC Report Headers
The DMARC report headers contain information about the sender, recipient, and the domain. The headers also contain information about the report’s format, version, and date range. Understanding the DMARC report headers is essential for effective analysis of the report.
Step 3: Analyze Authentication Results
The authentication results indicate whether the email message passed or failed the DKIM and SPF authentication checks. A pass result means that the email message was authenticated successfully, while a fail result means that the email message failed the authentication checks. By analyzing the authentication results, you can identify authentication issues and improve the email authentication process.
Step 4: Analyze DMARC Policy Actions
The DMARC policy actions determine how the DMARC receiving servers should handle email messages that fail the authentication checks. The DMARC policy actions include
quarantine, reject, and none. By analyzing the DMARC policy actions, you can identify how the DMARC receiving servers are handling email messages that fail the authentication checks
Step 5: Analyze Sources of Email Messages
DMARC reports provide information about the sources of email messages that were sent on behalf of your domain. By analyzing the sources of email messages, you can identify any unauthorized use of your domain name and prevent phishing attacks.
Step 6: Identify Trends
By analyzing DMARC reports over time, you can identify trends and patterns in email traffic. This can help you to identify any anomalies or suspicious activity.
Step 7: Take Action
After analyzing DMARC reports, you should take appropriate action to improve email security. This may include improving email authentication, identifying and preventing unauthorized use of your domain name, and resolving any delivery issues.
SimpleDMARC makes analyzing DMARC reports simple by providing real-time reporting, advanced analytics, and email notifications. The real-time reporting allows users to see how their emails are being authenticated and delivered, while the advanced analytics feature helps identify trends and patterns in email traffic. Additionally, SimpleDMARC sends email notifications for any changes in DMARC reports or email traffic, ensuring that users are always aware of any issues or vulnerabilities in their email authentication process. With these features, SimpleDMARC simplifies the DMARC analyzing process and makes it easy to identify and address any potential security risks.
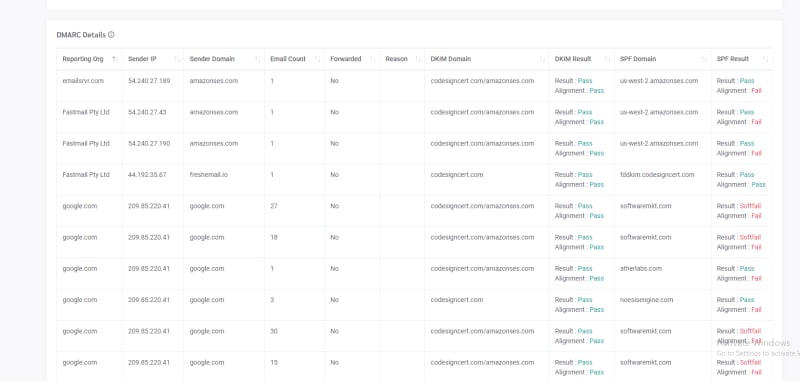
This is how a report in SimpleDMARC looks like:
Conclusion:
DMARC reports are critical for maintaining email security and preventing phishing and spoofing attacks. By analyzing DMARC reports, you can identify and prevent unauthorized use of your domain name, prevent phishing attacks, and improve email authentication. The steps outlined in this article provide a basic guide on how to read and analyze DMARC reports effectively. By following these steps, you can ensure that your organization’s email communication remains secure and protected.



Top comments (0)