What is Hashing?
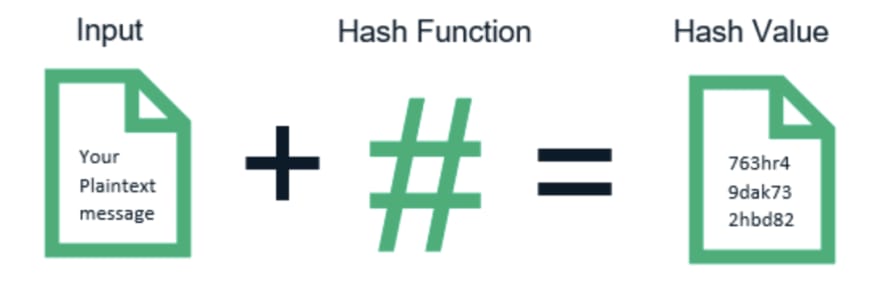
Hashing is the process of creating a key that represents a piece of data in a given context. In other words, “Hashing is using some function or algorithm to map object data to some representative integer value” (FreeCodeCamp.com). Hashing can be used in many different contexts, some of which we will explore in this blog.
How does a hashing function work?
According to Bart Preneel in his article Mash Hash Functions (Modular Arithmetic Secure Hash), “A hash function is a cryptographic algorithm that takes input strings of arbitrary (or very large) length, and maps these to short fixed length output strings.” Essentially, hashing functions are one way to turn identifiable data into an anonymous key, or to create an index for storing a value in a data structure. There are many ways to implement a hashing function. It is important that the hashing function returns the same index for the same input every time it runs, or else the stored data would not be consistently accessible. When creating an index to store data, the produced hash must stay within the storage limit of the data structure.
There are a variety of hashing functions which have advantages for different uses. Three of the most common types of hashing functions are Arithmetic Modular, Truncation, and Folding, according to Jerry Ejonavi’s article Data Structures 101: Implement Hash Tables in JavaScript. These types of functions differ in the way by which they treat their input keys and specifically how they encode them. Below is a brief explanations of these three types from Ejonavi's blog:
Where can we use hashing?
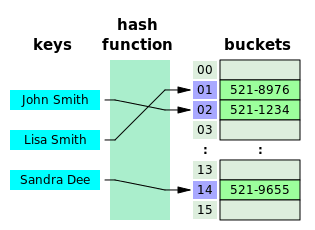
Example 1: Hash Tables
Hash tables are part of the implementation of objects literals in javascript. Hash Tables use a hashing function to take in a key for an item, create an index for that item, which can then be used to store a value associated with the key. Given that the hashing function produces a consistent and reliable result for a given unique key, this can be a helpful tool for data storage.
Example 2: User Passwords Security
When a user is visiting a website, they may need to sign in to access certain usability of the site. In that case each user will have a username and password to provide security. When a user inputs their password that information will be passed to a server to provide access. However, this process introduces security concerns if passwords and user info were moved as plaintext. Hashing is a way to move that information between the client and server with much less risk to the user.
What is the difference between encryption and hashing?
According to William Jackson’s article Why Salted Hash Is As Good For Passwords As For Breakfast, “Encryption is a two-way function” which can be unlocked with the correct key. “Hashing, is a one-way function” that produces a unique index or id which if done well, cannot be decoded. For Additional security, a salt, or a random string of characters, can be added to the key before hashing to introduce an additional element of randomness, therefore producing a stronger hash. Hashing with salt is a common security strategy and helps to protect against malicious hackers using rainbow tables.
In conclusion, hashing has many applications and is an important concept and tool in program development. Hashing can provide accurate and secure data storage, and protect user data from attacks.
Sources:
https://www.freecodecamp.org/news/what-is-hashing/
https://www.educative.io/blog/data-strucutres-hash-table-javascript#function
https://docs.google.com/presentation/d/1RboEl1LSD9WutGQ_GiNKuecKLBFuOywEoZX5jo1QbGE/embed?slide=id.g4c07df579d_0_2414
https://link.springer.com/referenceworkentry/10.1007%2F0-387-23483-7_243#:~:text=MASH%2D1%20and%20MASH%2D2,short%20fixed%20length%20output%20strings.
https://gcn.com/articles/2013/12/02/hashing-vs-encryption.aspx
https://sectigostore.com/blog/hashing-vs-encryption-the-big-players-of-the-cyber-security-world/




Top comments (0)