If you’re at all involved in the WordPress community, it’s likely you’ve heard about a small commercial theme company called pipdig, which has found itself at the center of some very serious controversy.
And while it’s been a little over a week since the scandal broke, people that have been using a pipdig theme or any one of their plugins (specifically pipdig Power Pack (p3)) might find themselves not knowing what to do next.
How it All Started
On March 29, 2019, Wordfence threat analyst Mikey Veenstra published a report about the small theme company pipdig, which also happens to provides hosting services. This report was shocking to the WordPress community and revealed some very serious (and possibly illegal) actions on the part of the pipdig team.
In short, pipdig was found to using its premium plugin, pipdig Power Pack (p3), to create hidden backdoors using obfuscated code built into the plugin that could be used to do the following:
- Give the team at pipdig the ability to grant themselves admin access to sites using the p3 plugin
- Reset the administrator passwords for easy access to sites belonging to others
- Remotely delete the entire database of sites using p3
In other words, Wordfence discovered that any website that used the pipdig Power Pack (p3) plugin, which conveniently comes built into all pipdig themes, was at risk for being used for malicious means – and the site owners had no idea.
And to make matters worse, Veenstra’s report states that “Due to the nature of these backdoors, which make remote calls to Pipdig’s servers as opposed to listening for incoming requests, an inbound firewall rule cannot prevent these actions.”
This means that even if you took the proper measures to secure your WordPress sites from outside threats, you would not be able to stop pipdig from using their plugin to break in and use your site as they see fit.
But Wait, There’s More…
At the same time, Wordfence was investigating the pipdig backdoor issues, Jem Turner, a freelance web developer from the UK, published findings that pipdig was using customer websites to perform small-scale DDoS attacks on a competing theme company. Plus, she found that pipdig was harvesting user data – unbeknownst to users.
In fact, her lengthy and quite technical analysis of the pipdig Power Pack plugin reveals that pipdig was/is:
- Using the servers of their customers to conduct DDoS attacks on competitors
- Manipulating bloggers’ content to change links to competitor WordPress migration services to point to the pipdig site instead
- Harvesting data from people’s websites without permission (which is in direct violation of GDPR)
- Using the harvested data to reset admin passwords and gain access to bloggers’ sites
- Implementing a built-in “kill switch” to drop all database tables
- Disabling other plugins that pipdig deems unnecessary without permission
- Hiding admin notices and meta boxes from the WordPress core and other plugins from the dashboard
And how did this UK-based web developer find out any of this was happening in the first place?
One of her clients came to her asking for help because she noticed her website, that was running a pipdig theme, was acting strangely. So, Turner took it upon herself to check things out (as any good web developer would) and came across much more than she bargained for, claiming she has “…never seen anything like it.”
pipdig’s Reaction to the Accusations
Of course, any company that comes under fire for doing things the wrong way is going to react in one way or another. And pipdig is no different.
To start, the pipdig team quickly released pipdig Power Pack version 4.8.0, with much of the code in question being removed. However, any customer using a pipdig theme, and thus the p3 plugin, that hasn’t updated their plugin to version 4.8.0, is still at risk for a database deletion, a DDoS attack generating from their site, and much more.
Adding to that, so far as we can tell, p3 4.8.0 still has the ability to deactivate plugins on customers’ site without their permission. And since some of the plugins that automatically disable are deactivated alongside admin_init, there’s no way to reactivate them.
It’s also interesting that on March 31, 2019, when all of this was being exposed to the public, pipdig deleted its public Bitbucket repository and replaced it with a “clean one.”
Here’s a look at the cloned repository Wordfence nabbed before the deletion, which dates all the way back to 2015:
And here’s a look at the “new and clean” repository:
To many, this is a clear indication that pipdig is trying to hide something, which does not bode well for any defense they try to cling to.
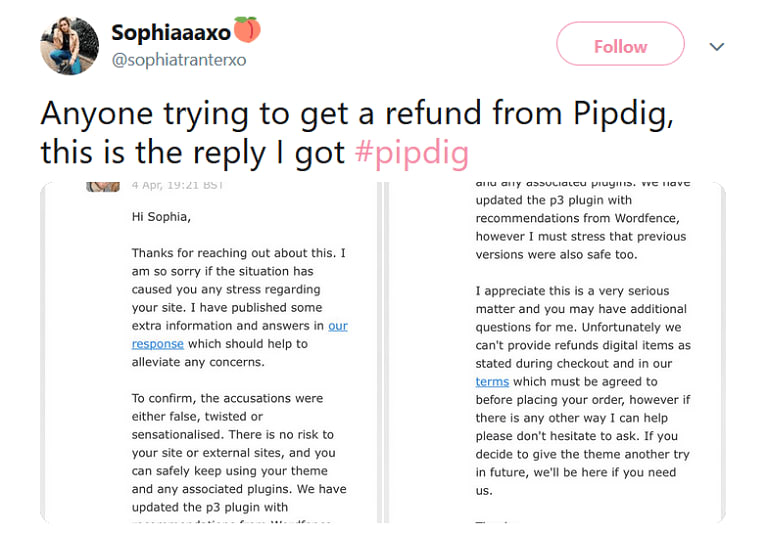
And let’s not forget the way pipdig is handling customer requests for a full refund. No one willingly pays for a product that can single-handedly destroy their website and be hijacked for malicious means. But pipdig is sticking by their “No Refunds” policy, despite the backlash from users.
They have even gone so far as to publicly claim that customer accusations and the finding of Wordfence are “false, twisted, or sensationalized.”
pipdig’s Public Defense
pipdig Creative Director, Phil Clothier, has published a public response to what he claims are accusations and rumors, and this is just some of what he has to say:
- pipdig does not DDoS competitors, “kill” sites or use the pipdig Power Pack plugin to destroy websites
- The built-in “kill switch” Turner references in her analysis was a “…function in an older version of the plugin which could be used to reset a site back to the default settings…This feature has been dug up and labeled a “Kill Switch” for maximum negative impact on us.”
- The “kill switch” function has only been in the p3 plugin since July 2018, which Wordfence found to be false (the first instance of database deletion happened in November 2017)
- Users are the ones responsible for any DDoS attacks, as they had to have added to competitor’s URLs to their own websites
Though pipdig has publicly denied all accusations about their malicious activity, there is really no way to cover up the facts.
As a result, pipdig has been reported to the internet authorities and is under a full investigation. Even their own hosting provider has taken a proactive approach by disabling malicious code found during their own individual investigation.
And Wordfence has this to say about the entire situation (amending their original recommendation to be cautious but not get rid of pipdig altogether just yet):
“Wordfence recommends removing all Pipdig content from your sites, both WordPress and Blogger. Pipdig has demonstrated a willingness to abuse users’ resources to execute unethical, and potentially illegal, activity. Furthermore their repeated denial of solid evidence, and subsequent attempts to conceal it, leave us unable to trust them in the future.”
As a Blogger, What’s Next?
Okay, so you know that pipdig is definitely involved in some shady tactics and you no longer want to be a part of it.
But what are you supposed to do as a pipdig theme owner and p3 plugin user?
For many, changing themes is a stressful ordeal. Time, money, skillset, and love for a working theme are all things to consider when something like this happens. And yet, customers of pipdig are scared to keep using pipdig in light of their recent behavior.
That’s why we’re here to offer some help if you want to get out of being a pipdig customer:
- Request a Refund: if you’ve purchased a pipdig theme in the last 180 days, email a request for a refund despite the “no refund” policy. If they ignore or deny your requests, take it up with PayPal or your credit card/banking provider. Existing consumer protection laws and evidence of false and misleading conduct may be enough to get your money back.
- p3 Neutralizer Plugin: while you’re deciding what steps to take next, use the p3 Neutralizer plugin, which prevents the pipdig Power Pack plugin or your pipdig theme from updating or calling home to malicious pipdig URLs that can harm your site.
- Find a New Theme: we know you might love your pipdig theme. But the beauty of using WordPress is that there are plenty of reliable and non-malicious WordPress themes out there to fit any budget. Check out the WordPress Repository for free themes that are always coded using the highest standards. Or, check out this helpful resource of alternative pipdig themes.
- Get New Hosting: if you happen to use pipdig as your web hosting provider, get rid of them too. Doing business with a company that has gone to such lengths to damage customer websites and cover their tracks is not a company you should entrust your website to.
If you don’t have the time or skills to get rid of pipdig themes, plugins, or hosting services, and want immediate relief from any malicious activity that might be happening on your website right now, get 24-hour malware emergency relief from us here at BitofWP.
Our goal at BitofWP is to:
- Clean up your website in 24 hours or less
- Get rid of all malware while monitoring every step of the way using humans (not machines)
- Provide a three-month clean site guarantee (if problems persist within the three months, we’ll clean your site again for free)
- Upgrade all WordPress core files, themes, and plugins, making sure all malware and bad files are removed
- Get rid of all malware redirects
- Remove website backdoors (like the ones pipdig created in their p3 plugin)
- Rid your site of all pharma attacks
- Help you set up a new theme and get previously deactivated plugins up and running again
We’ll even help you move your website from pipdig hosting to another hosting provider – with zero downtime – so you don’t have to worry about falling victim to pipdig’s malicious ways ever again.
Final Thoughts
This incident goes to show the WordPress community how vulnerable WordPress-specific themes and plugins can be and how little protection people have from those that want to take advantage of their customers. That’s why it’s always recommended to use WordPress software that has been vetted and verified, is routinely updated, and has no problem being 100% transparent.
However, this incident also shows how helpful the WordPress community can be when something bad happens.
WordPress prides itself on banding together and helping people of all skill levels, with varying needs, no questions asked. And as we can see from the different articles that have been published making people aware of the problem, the updates on pipdig’s reaction to the accusations, and the wonderful WordPress users on social media and blog comments offering to help others wanting out as a pipdig customer, the community is doing what it does best – helping each other.
Photo by Hans-Peter Gauster on Unsplash
The post Pipdig Under Investigation (and Your Options If You Want Out) appeared first on WordPress Support Services by BitofWP.





Top comments (0)