In our interconnected world, safeguarding digital data is not just a priority; it's a mission. As Java developers, we play a crucial role in this mission, given the widespread use of Java applications across industries, from finance to healthcare. Our responsibility is to ensure that sensitive information remains confidential and secure through the power of encryption.
Why Encryption Matters for Java Developers
First things first: Do you need encryption? It may sound like a simple question, but it's fundamental. Encryption is designed to make data unreadable (ciphertext) and then reversible into its original form (plaintext). However, not everything needs to be reversible. When dealing with passwords, for instance, we use hashing, ensuring that the original text is never recoverable. So, as a Java developer, the first step is to discern when to encrypt and when to hash.
Embrace Encryption for Data Security
Java applications frequently handle sensitive data, including user information, financial transactions, and confidential records. To fulfill our duty as guardians of this data, we must master robust encryption algorithms. This not only protects our users but also safeguards the integrity of our systems.
Symmetric vs. Asymmetric Encryption: Choose Wisely
Before diving into the world of encryption, let's clarify two primary types: symmetric and asymmetric. They each have unique characteristics and use cases.
Symmetric encryption uses the same key for both encryption and decryption. It's fast but less secure when sharing keys. Asymmetric encryption, on the other hand, relies on a key pair (public and private). The public key encrypts, while the private key decrypts. While symmetric encryption excels in encrypting large data volumes, asymmetric encryption shines when securely sharing keys over networks.
Mastering Symmetric Encryption in Java
When implementing symmetric encryption in Java, it's wise to leverage hardware security modules (HSMs) for key management. This simplifies the complex task of handling encryption keys. If HSMs aren't an option, don't worry; we've got you covered.
Let's roll up our sleeves and dive into the world of symmetric encryption in Java using the javax.crypto packages.
Beware of Outdated Encryption Algorithms
Not all encryption algorithms are created equal. Some, like DES (Data Encryption Standard) and 3DES, were once considered secure but are now vulnerable due to advancements in computing and cryptanalysis techniques. Using outdated encryption algorithms in your Java applications is a recipe for disaster, potentially leading to data breaches.
import javax.crypto.*;
import javax.crypto.spec.*;
import java.nio.charset.StandardCharsets;
import java.security.*;
public class EncryptionServiceDes {
private SecretKey secretKey;
private Cipher cipher;
public EncryptionServiceDes(String key) throws GeneralSecurityException {
byte[] keyBytes = key.getBytes(StandardCharsets.UTF_8);
DESKeySpec desKeySpec = new DESKeySpec(keyBytes);
SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("DES");
secretKey = keyFactory.generateSecret(desKeySpec);
cipher = Cipher.getInstance("DES/ECB/PKCS5Padding");
}
public String encrypt(String original) throws GeneralSecurityException {
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
// Encrypt the original data
byte[] encryptedData = cipher.doFinal(original.getBytes(StandardCharsets.UTF_8));
// Encode the encrypted data in base64 for better handling
return Base64.getEncoder().encodeToString(encryptedData);
}
public String decrypt(String cypher) throws GeneralSecurityException{
cipher.init(Cipher.DECRYPT_MODE, secretKey);
// Decode the base64-encoded ciphertext
byte[] encryptedData = Base64.getDecoder().decode(cypher);
// Decrypt the data
byte[] decryptedData = cipher.doFinal(encryptedData);
return new String(decryptedData, StandardCharsets.UTF_8);
}
}
Choose the Right Algorithm and Cipher Mode
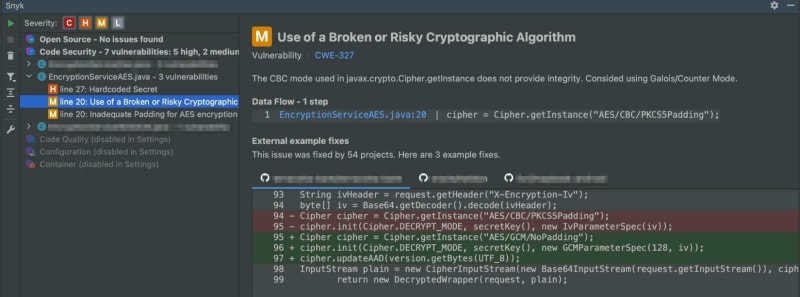
For symmetric encryption, heed the advice of OWASP: opt for AES (Advanced Encryption Standard) with a key length of at least 128 bits, preferably 256 bits. But don't stop there—choose a secure mode too. Avoid ECB (Electronic Codebook) mode, as it lacks message confidentiality. Instead, embrace modes like CCM (Counter with CBC-MAC) or GCM (Galois/Counter Mode) that ensure data's integrity, confidentiality, and authenticity.
import javax.crypto.*;
import javax.crypto.spec.*;
import java.nio.charset.StandardCharsets;
import java.security.*;
import java.util.Base64;
public class EncryptionServiceAESGCM {
private SecretKey secretKey;
private Cipher cipher;
public EncryptionServiceAESGCM(String key) throws GeneralSecurityException {
byte[] keyBytes = key.getBytes(StandardCharsets.UTF_8);
secretKey = new SecretKeySpec(keyBytes, "AES");
cipher = Cipher.getInstance("AES/GCM/NoPadding");
}
public String encrypt(String original) throws GeneralSecurityException{
byte[] iv = new byte[16]; // Initialization Vector
SecureRandom random = new SecureRandom();
random.nextBytes(iv); // Generate a random IV
cipher.init(Cipher.ENCRYPT_MODE, secretKey, new GCMParameterSpec(128, iv));
byte[] encryptedData = cipher.doFinal(original.getBytes());
var encoder = Base64.getEncoder();
var encrypt64 = encoder.encode(encryptedData);
var iv64 = encoder.encode(iv);
return new String(encrypt64) + "#" + new String(iv64);
}
public String decrypt(String cypher) throws GeneralSecurityException{
var split = cypher.split("#");
var decoder = Base64.getDecoder();
var cypherText = decoder.decode(split[0]);
var iv = decoder.decode(split[1]);
var paraSpec = new GCMParameterSpec(128, iv);
cipher.init(Cipher.DECRYPT_MODE, secretKey, paraSpec);
byte[] decryptedData = cipher.doFinal(cypherText);
return new String(decryptedData);
}
}
Identifying Weak Encryption Algorithms
To detect insecure encryption, we can turn to tools like Snyk. By connecting your code repository to Snyk, it identifies insecure cryptographic algorithms and suggests secure alternatives, like AES encryption.
Snyk Code Git Integration
Continuous Improvement is Key
Updating encryption algorithms is crucial, but remember that security evolves. Regularly scan your code for new security issues using static analysis security testing (SAST) tools like Snyk Code for Java. Stay ahead of potential threats and keep your data secure.
Snyk IntelliJ IDEA Plugin
Empower Your Java Development with Snyk Code
Snyk Code is your ally in the battle for secure code. It's a state-of-the-art static application security testing (SAST) tool that identifies vulnerabilities within your codebase. Supporting various programming languages, including Java, Snyk Code offers real-time feedback, integrates into your CI/CD pipeline, and supports popular IDEs. Use it to catch and fix security issues early in your development cycle.
Conclusion: Be a Secure Code Warrior
As Java developers, we are the guardians of data security. Mastering symmetric encryption in Java is not just a skill; it's a responsibility. Choose the right encryption algorithms, stay updated, and empower yourself with tools like Snyk Code. Together, we can ensure a safer digital world for all.
Disclaimer: This article provides educational information about encryption practices. Always follow best practices and consider the latest security recommendations for your specific use cases.




Top comments (0)