Introduction
Authentication and Authorization are key in application development. They are the backbone of security and user management, controlling resource access and maintaining data integrity and privacy. With the rise of cyber threats, these systems are rapidly evolving in complexity and significance.
In this article, we will dive into some noteworthy open-source projects in this space, each with unique features that make them stand out. We're focusing on projects that are actively maintained, well-documented, thoroughly tested, and widely recognized for their quality and user base.
Please Support Us
If you find this post helpful,please give OPAL a star on GitHub! Your support helps us make access control easier and motivates us to write more articles like this one.
Let's get started!
Authentication
Let's start with authentication. The process of checking if someone is who they say they are has come a long way from just asking for a password. Here are some cool open-source projects to help you implement a secure and robust authentication process into your app.
Hanko.io
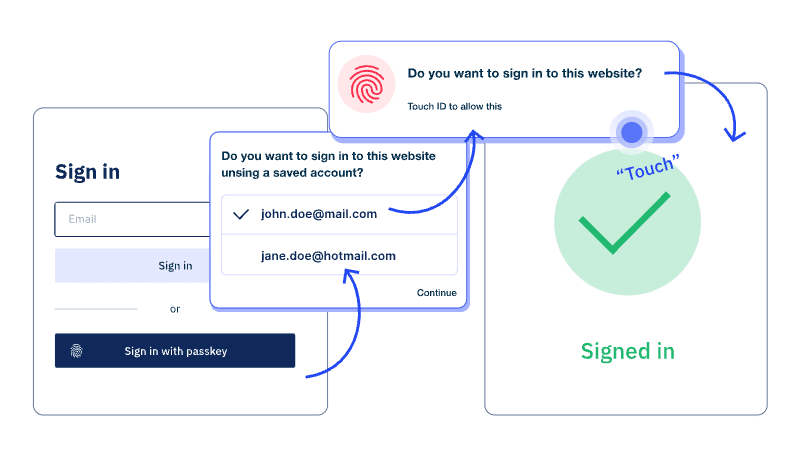
Hanko is an open-source authentication solution that's big on passkey-based authentication, like Apple and Google. It comes with a backend for authentication, OAuth SSO, user management, and JWT issuing. Plus, it offers web components for onboarding and login, as well as a client package for using the Hanko API.
Developers can dive in with a live example or quickstart app, with options for local use. Hanko Elements offer frontend integration backed by guides and examples. Enterprise or Hanko Cloud users can use SAML SSO.
Hanko stands out with its focus on passwordless authentication and its toolkit. Its affiliation with the FIDO Alliance and track record with FIDO and WebAuthn-based authentication add credibility.
Zitadel
ZITADEL is an open-source identity infrastructure platform. It combines the simplicity of Auth0 with the open-source commitment of Keycloak, providing multi-tenancy, secure login, and self-service functionalities. It supports various protocols such as OpenID Connect, OAuth2.x, and SAML2.
If you're just starting out, ZITADEL offers a range of deployment options to suit your needs, including Linux, MacOS, Docker compose, Knative, and Kubernetes. For a more managed experience, ZITADEL Cloud is available. It has a free tier that offers all the features of the open-source version.
One of the significant distinguishing features of ZITADEL is its multi-tenancy architecture. It's perfect for B2B customer and partner management, supporting both CockroachDB and Postgres databases. With an API-first design, ZITADEL is an excellent choice for your identity infrastructure needs.
SuperTokens
SuperTokens is an open-source project that provides you with a bunch of great features like secure login, session management, and multi-factor authentication. Its architecture consists of three components: Frontend SDK, Backend SDK, and SuperTokens Core, each handling different authentication aspects.
The SuperTokens open-core model provides you with free usage and no user limits. Plus, it simplifies OAuth protocols, making it an excellent choice for developers hunting for customizable Authentication solutions.
Authorization
Unlike Authentication, Authorization deals with granting users access to parts of the application once they’ve logged in based on user permissions. You might be familiar with Role-Based Access Control (RBAC), one of the most common approaches to managing this type of access. The future of authorization, though, lies in fine-grained control and policy-as-code approaches, as simple RBAC is rarely enough with today's complex applications.
Here are some great projects that allow you to build more future-proof Authorization:
AWS’ Cedar Language
Cedar is a new open-source policy language and engine created by AWS. Designed to provide a solution for implementing Policy as Code, it supports RBAC and ABAC, and provides quick data retrieval and scalable real-time evaluations. Plus, it even supports Automated Reasoning for policy optimization and validation.
Implemented as Rust crates, it’s quite easy to integrate it into your app. It's made of a few components, including a main cedar-policy crate for authorization and validation, a CLI, a parser, evaluator, and a policy formatter.
With Cedar's user-friendly syntax and thorough documentation, defining and testing policies is a breeze!
OpenFGA
OpenFGA is a high-performance authorization engine inspired by Google Zanzibar. It streamlines application permissions and integrates fine-grained authorization, supporting in-memory data storage and database modules like PostgreSQL 14 and MySQL 8. It offers HTTP and gRPC APIs along with SDKs for Node.js/JavaScript, GoLang, Python, and .NET.
For swift setup, OpenFGA uses Docker and Docker Compose. However, the default configuration with memory storage is not for production environments. Instructions for production deployment are in the official documentation.
OpenFGA has been utilized by Auth0 FGA since December 2021. The memory storage adapter is for development purposes, while PostgreSQL and MySQL Storage Adapters are ready for use in production.
Designed for Relationship-Based Access Control (ReBAC), OpenFGA also addresses Role-Based and Attribute-Based Access Control use cases. Its user-friendly modeling language integrates seamlessly with existing code via various SDKs. OpenFGA targets millisecond response times for authorization checks, ensuring scalability for all projects.
OPAL
OPAL, the Open Policy Administration Layer, operates as a dynamic layer for policy engines like Open Policy Agent (OPA) and AWS' Cedar Agent. It detects real-time policy and data changes, ensuring policy agents are consistently up to date. This synchronization extends across various services, such as APIs, databases, and SaaS solutions.
In integration scenarios, OPAL amplifies the functionality of policy engines. For OPA, OPAL enhances its decoupling of policy and code by maintaining real-time policy agent updates. Similarly, with AWS Cedar, OPAL facilitates integration across diverse environments, from other clouds to local or on-premise setups.
OPAL is accessible as Python packages with an in-built CLI and as Docker images. It operates on a client-server stateless architecture, with OPAL servers publishing updates over a PubSub channel and clients fetching data to update OPA instances. Comprehensive resources, including documentation and how-to guides, support users in integrating OPAL effectively.
Overall, OPAL's real-time policy administration capabilities make it a valuable tool for cloud-native applications, reflecting its adaptability and utility in various authorization contexts.
Frontend/Fullstack Frameworks
Frontend and Fullstack frameworks are crucial in implementing successful authentication and authorization systems. They provide the tools and environments to create user interfaces and efficiently manage backend services.
NextAuth.js
NextAuth.js is an open-source authentication solution designed for modern applications, specifically tailored for next.js, a widely-used React framework. It offers flexibility, supporting a range of authentication methods such as OAuth 2.0+, OpenID Connect (OIDC), popular sign-in services, and email or passwordless authentication. NextAuth.js can be integrated with any backend system, operating independently of the runtime environment.
In terms of data management, NextAuth.js can function with or without a database and is compatible with various systems, including MySQL, MariaDB, Postgres, Microsoft SQL Server, MongoDB, and SQLite.
Security is prioritized in NextAuth.js design, promoting passwordless sign-in mechanisms and implementing measures like Cross-Site Request Forgery (CSRF) tokens, restrictive cookie policies, and encrypted JSON Web Tokens (JWE).
Lastly, the package provides advanced configuration options and TypeScript support. Developers can set custom routines for account sign-in control, JWT encoding/decoding, and cookie security policies. The libraries are developed with type safety, enhancing their robustness in development contexts.
Supabase
Supabase is a friendly open-source toolset that's packed with robust authentication and access control features. It employs a hosted PostgreSQL database for managing user data and permissions. Its key features are JWT-based authentication and authorization mechanisms and auto-generated REST and GraphQL APIs for efficient integration. Supabase ensures secure and best-practice-compliant data access, making it a comprehensive backend solution for developers.
Access Control Miscellaneous
Authentication and authorization encompass a range of unique features for advanced use cases. Projects in this category offer solutions for more specialized aspects of auth and access control.
JWT - jose
The jose library is a comprehensive JavaScript module providing robust support for JSON Object Signing and Encryption (JOSE). It caters to a wide range of functionalities including JSON Web Tokens (JWT), JSON Web Signature (JWS), and JSON Web Encryption (JWE).
Key features include JWT support, handling of encrypted JWTs, support for JWS and JWE, and compliance with standards such as RFC7515 (JWS), RFC7516 (JWE), and RFC7519 (JWT). Designed for versatility, jose works across various web-interoperable runtimes like Node.js, browsers, and Cloudflare Workers. Its zero-dependency feature makes it lightweight and easily integrated into diverse project environments.
All in all, jose is a super flexible solution for the complex security needs of your web applications. Whether you're working on auth or access control mechanisms, jose is here to make your life easierץ
OAuth Server - Hydra
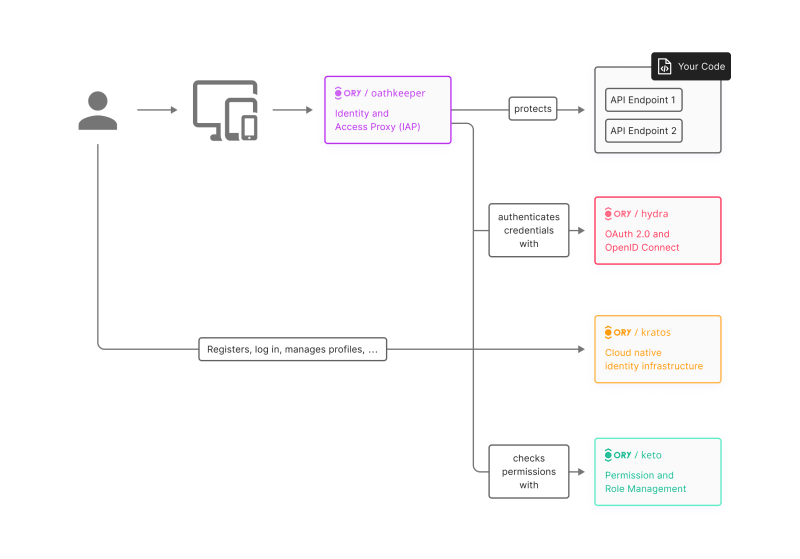
Not every application requires a dedicated OAuth server, but for those that do, it's a critical component due to stringent security requirements, the need for scalable user management, and complex integration ecosystems. Hydra, an OpenID Certified OAuth 2.0 Server and OpenID Connect Provider, is optimized for low-latency, high throughput, and low resource consumption, making it an ideal choice for such scenarios.
Hydra is designed to connect with existing identity providers, enabling flexible integration with various authentication workflows. It's part of the Ory Network, providing a robust infrastructure for modern security needs, including scalable identity management, support for various authentication methods, and low-latency permission checks. This makes Hydra a preferred choice for developers requiring a specialized, secure, and scalable OAuth server for their applications.
Single Sign On (SSO) - Keycloak
In today's interconnected digital landscape, Single Sign-On (SSO) technology is crucial, allowing users to log in once for access to multiple systems. Keycloak, an open-source identity and access management solution, provides a centralized platform for managing user authentication across various applications, enhancing user experience and security.
Keycloak seamlessly integrates with existing LDAP or Active Directory servers and provides SSO capabilities for user convenience. It streamlines user authentication by supporting social logins and authenticating users with existing OpenID Connect or SAML 2.0 Identity Providers.
Adherence to standard protocols, such as OpenID Connect, OAuth 2.0, and SAML, enhances Keycloak's interoperability and security. In addition to traditional role-based authorization, it offers fine-grained authorization for detailed permission and policy management.
In conclusion, Keycloak's extensive features and seamless integration with existing systems and protocols make it an excellent choice for developers implementing secure and user-friendly access control.
Zero Trust - OpenZiti
Amid evolving cyber threats, OpenZiti has become essential, encapsulating the zero-trust security model of "never trust, always verify." OpenZiti signifies a shift in secure, open-source networking. It combines a scalable networking mesh, smart routing, secure entry points, and SDKs for application integration.
OpenZiti enforces Zero Trust and Application Segmentation by imposing access controls on individual applications within a network and requiring client identities backed by provisioned certificates. It also enables services to operate 'dark,' not exposing open ports for external connections, which enhances security. Additionally, OpenZiti facilitates seamless end-to-end encryption by embedding its SDKs into client and server applications.
In addressing modern network security challenges, OpenZiti offers a robust solution for organizations aiming to implement zero-trust principles.
Conclusion
In conclusion, the world of open-source authentication and authorization is vast and diverse, constantly evolving to meet modern security demands. As developers, staying updated with these projects is crucial, as is understanding their unique offerings and how they can be applied in our work. We encourage you to explore and support these open-source projects, contributing to their growth and helping to shape the future of secure, user-friendly applications.
Like this article? Please support our open source project OPAL in GitHub by staring it.








Top comments (0)