Introduction
Remote Code Execution (RCE) vulnerabilities in web applications are some of the most critical security risks you can face. If exploited, they allow attackers to execute arbitrary code on your server, leading to data theft, server hijacking, or worse. This blog post will dive into how RCE vulnerabilities manifest in Symfony applications and how you can mitigate them with practical solutions and coding examples.
To ensure your website is protected, you can use our free Website Vulnerability Scanner tool to identify vulnerabilities, including RCE risks.
Understanding Remote Code Execution (RCE) in Symfony
RCE vulnerabilities typically occur when an attacker is able to send malicious input to the server which results in the execution of arbitrary code. In the context of Symfony, RCE can arise from various sources, such as unvalidated user input, deserialization flaws, or improper handling of system commands.
Common Causes of RCE in Symfony
Deserialization Vulnerabilities
Symfony applications often use serialized data for storing complex objects. If untrusted data is deserialized, an attacker can inject harmful code.Improper Command Execution
Allowing user input to control system commands (likeshell_exec()) without proper validation can lead to RCE.Insecure File Uploads
If file uploads are not properly validated, malicious files can be uploaded and executed.
How to Prevent RCE Vulnerabilities in Symfony
1. Sanitize User Inputs
Always sanitize inputs from untrusted sources before processing them. For example, use Symfony's built-in validation mechanisms to prevent any harmful inputs.
Example:
use Symfony\Component\Validator\Constraints as Assert;
// Validating a user input to ensure it’s a valid string
$input = "user_input";
$validator = Validation::createValidator();
$violations = $validator->validate($input, [
new Assert\NotBlank(),
new Assert\Type("string"),
]);
if (count($violations) > 0) {
throw new \Exception("Invalid input");
}
2. Avoid Dangerous Functions
Functions like shell_exec() and eval() should never be used with user-controlled input. Always validate and sanitize any input before passing it to system functions.
Example:
// Unsafe
$input = $_GET['command'];
shell_exec($input); // Don't do this!
// Safe alternative
$input = escapeshellarg($_GET['command']);
shell_exec($input);
3. Implement Safe File Uploads
If your application allows file uploads, ensure that you validate the file type and scan for potentially dangerous files like executables.
Example:
$uploadedFile = $_FILES['userfile'];
if ($uploadedFile['type'] !== 'image/jpeg') {
throw new \Exception("Invalid file type");
}
How to Conduct Web App Penetration Testing
Penetration testing is crucial for uncovering vulnerabilities like RCE. At Pentest Testing Corp, we offer professional web app penetration testing services to help you identify weaknesses in your application before they can be exploited.
We use a combination of automated tools and manual testing to conduct thorough assessments, ensuring all vulnerabilities are caught.
For more information, visit our Web App Penetration Testing Services page.
Using Our Free Tool to Check for RCE Vulnerabilities
One of the easiest ways to detect potential vulnerabilities in your Symfony application is by running a security scan with our free tool. Visit Pentest Testing Corp.'s free Website Security Scanner to perform a thorough security check.
Here’s a screenshot of our tool in action:
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
Once the scan is complete, you’ll receive a detailed vulnerability assessment report.
Below is an example of a website vulnerability assessment report generated by our free tool to check Website Vulnerability:
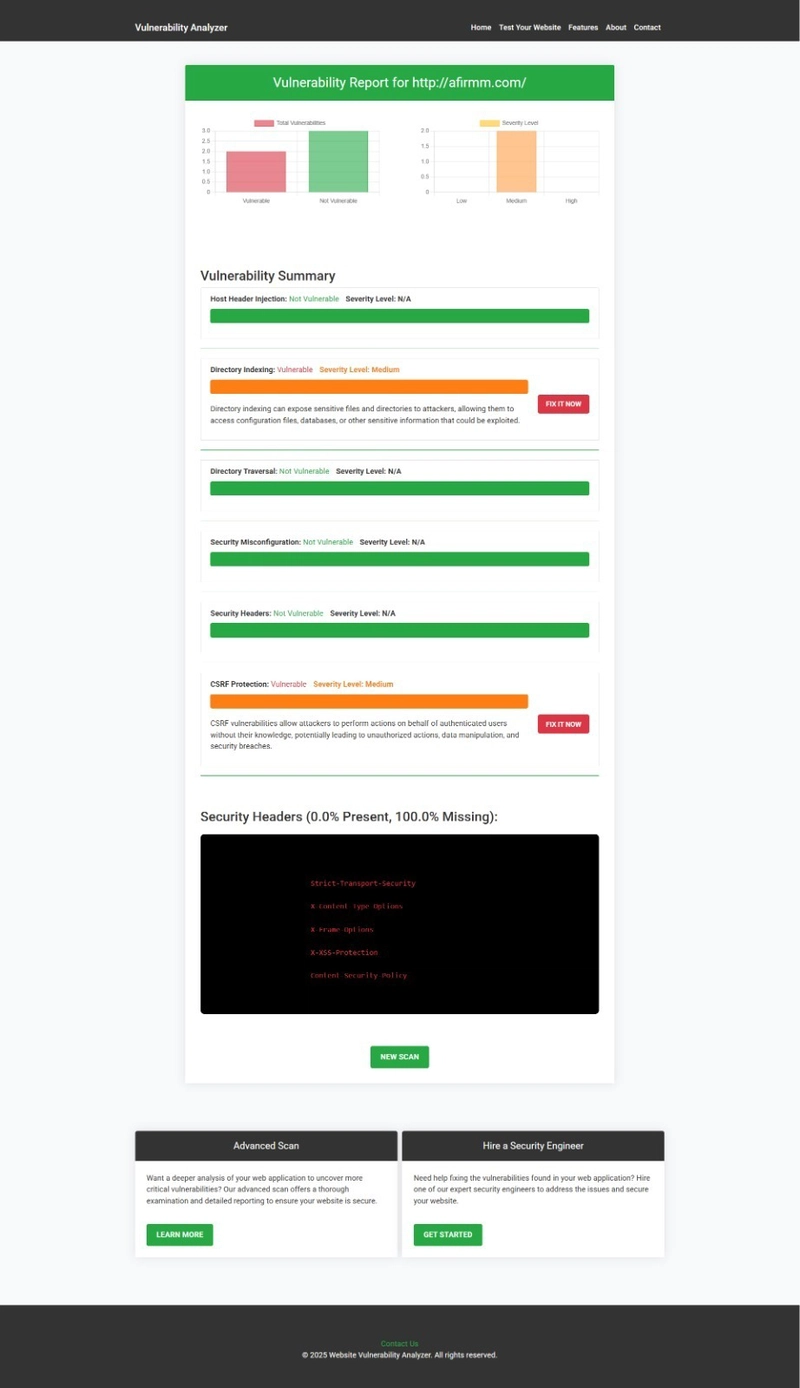 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Additional Best Practices to Secure Symfony Apps
- Enable Symfony Security Features: Make use of Symfony’s built-in security features, such as CSRF protection and authentication mechanisms.
- Patch Regularly: Keep your Symfony application and all dependencies updated. Many RCE vulnerabilities are patched in newer versions.
- Implement Error Handling: Never expose stack traces or sensitive error information to the user.
Conclusion
Preventing Remote Code Execution (RCE) vulnerabilities in Symfony is crucial for securing your web applications. By following the best practices outlined in this post and using our free security checker tool for a Website Security check, you can significantly reduce the risk of RCE and other common vulnerabilities.
For more security tips and guides, visit our blog at Pentest Testing Blog.




Top comments (0)