Introduction
In today's rapidly evolving software development landscape, ensuring code quality and security is of paramount importance. Continuous Integration (CI) has become an essential practice in software development, enabling developers to integrate their code changes frequently and detect issues early in the development lifecycle. One crucial aspect of CI is the test suite, which encompasses various checks to ensure code quality and security. In this blog post, we will explore the pipeline of a CI test suite for a python project, highlighting the different steps involved and the tools utilized.
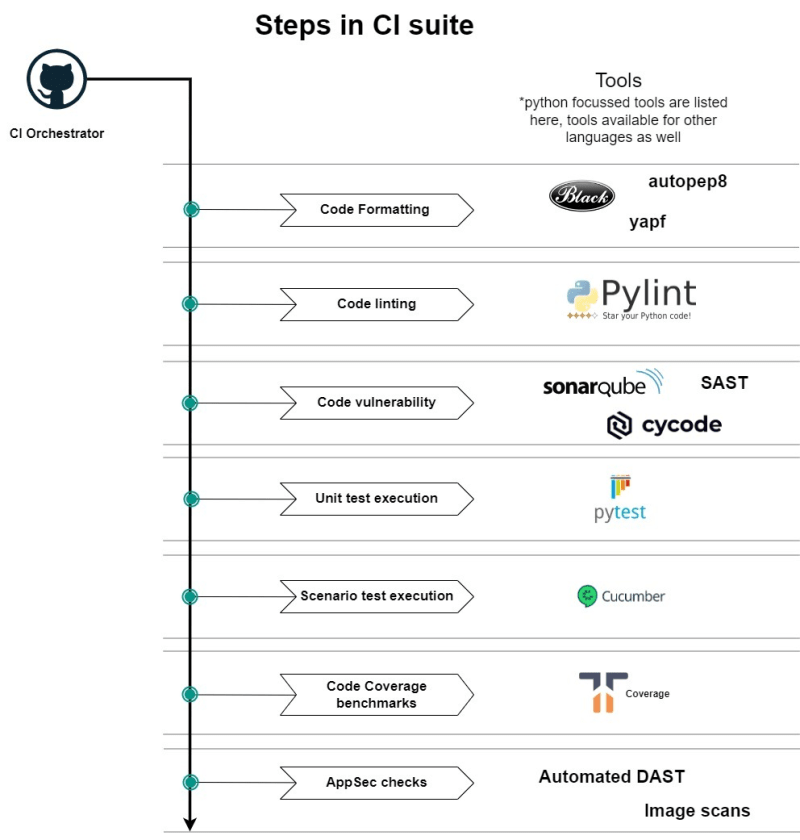
TL;DR Here's an quick overview of CI suite with a wide variety of steps with different tools.
Step 1: Code formatting
Consistent code formatting is vital for maintainability and collaboration within a development team. To enforce a consistent coding style, the first step in the CI test suite is code formatting. There are lots of code formatters available such as,
- Black
- autopep8
- yapf
Black is a popular Python code formatter that automatically reformats code to adhere to a defined style guide. By integrating Black into the CI pipeline, developers can ensure that their code follows consistent formatting conventions, enhancing readability and reducing code review overhead.
Step 2: Code linting
Linting is another crucial aspect of code quality. It helps to enforce the best practices and identifies common pitfalls, improving the overall code quality. Some of the commonly used code linters are as follows,
- Pylint
- Sonarlint (does more than linting)
- flake8
- autopep8
- bandit
Pylint, a widely used Python static code analyzer, performs lint checks to identify potential programming errors, stylistic issues, and adherence to coding standards. Integrating Pylint into the CI test suite ensures that code is thoroughly analyzed for potential issues before merging into the main codebase.
Step 3: Code vulnerability checks
In an era where security threats are prevalent, it is essential to detect vulnerabilities and security hotspots in the codebase. Various tools for these checks are,
- Sonarqube (sonarlint + other checks)
- cycode
Sonarqube, a code analysis tool, performs static security analysis to identify potential security vulnerabilities, such as insecure authentication mechanisms or code that is susceptible to injection attacks. By integrating Sonarqube into the CI pipeline, developers can proactively identify and address security issues, reducing the risk of potential exploits.
Step 4: Unit test cases
Unit testing is a fundamental practice in software development to validate the correctness of individual code units or components.
Step 5: Scenario test cases
Beyond unit tests, scenario or integration tests provide end-to-end validation of the system's behavior.
Behave, a popular Behavior-Driven Development (BDD) framework for Python, allows developers to define test scenarios in a human-readable format. These scenarios describe the expected behavior of the system from a user's perspective. By including scenario test cases in the CI test suite, developers can ensure that the software functions correctly in real-world scenarios and that different components interact seamlessly.
When connected with a reporting tool known as allure, we can checks the results in an interactive UI,
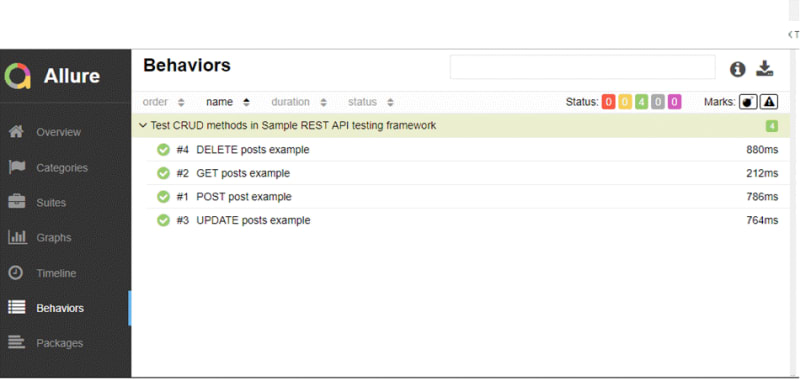
Step 6: Code coverage benchmarks
For section of testing, the coverage benchmarks should be addressed thoroughly. For both unit tests and scenario tests, having a strict coverage percents, helps the development to address and write testcases for the boundary conditions/edge cases. It provides the confidence of unit tests and how much of the code has been tested.
Step 7: AppSec Checks
The security plays a vital role in the development lifecycle. Each section of the security checks can be covered in the pipeline. They include the image scans and DAST.
The image scanning can be done with various scanning tools such as,
- Clair (also being used in ECR)
- Trivy
Tools like Clair provide image scanning capabilities that analyze the container image for known vulnerabilities and adherence to security best practices. Integrating Clair image scan checks into the CI pipeline allows developers to identify and address any security issues before deploying containerized applications.
The DAST checks can be automated up to a certain point, where the code should be able to withstand certain scans and attacks. For eg. SQL Injections can be checked with sqlmap which tests with each and every type of sql injection payload and reports it back to the user.
Conclusion
A strict pipeline of a CI test suite provides a comprehensive approach to ensure code quality and security throughout the software development process. By incorporating code formatting checks, linting, security analysis, unit tests, scenario tests, and image scans, developers can mitigate potential issues early on and deliver robust and secure software.








Top comments (0)