I've been planning to do a write-up about the time I found a high-level security vulnerability in SonyLIV, for quite some time now. Although this happened a couple of years ago, I feel it's still a cool vulnerability to talk about.
SonyLIV for the uninitiated is a streaming platform where you can watch live sports, movies, and tv shows. I would mainly use it for streaming live football matches, especially the UEFA Champions League. Recently they had made a few changes and introduced premium subscriptions, but as a normal user, you were given a 2-minute trial while watching premium content.
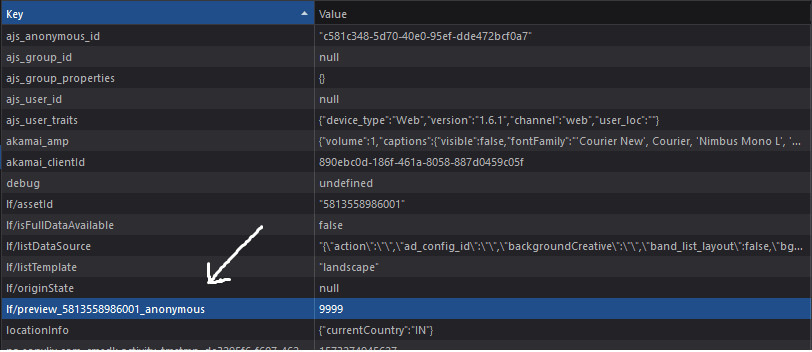
So here I am waiting for my favourite team's (Man Utd) match to start which was still half an hour away. As a web developer, I was curious to see how the premium feature was implemented and started poking around in the hope that I would find something interesting. I immediately ran Burp Suite and began intercepting requests to understand the flow of the app. After a few minutes, while checking how the cookies were set, I noticed something interesting in local storage.
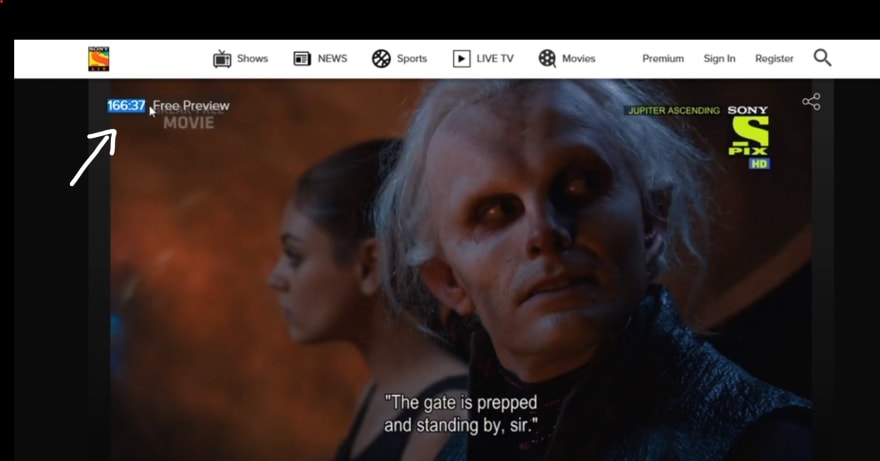
The default value was set to 120, meaning 2 minutes. I modified it to 9999 (~ 166 mins). To my surprise, it didn't work. After a few minutes of tinkering I realized, it only works if we modify the value before the video gets loaded.
I increased the time limit for the Man Utd match and watched it for free!
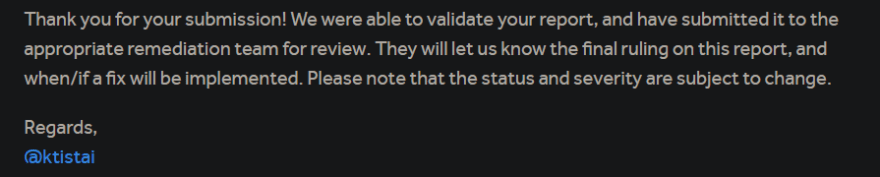
The next morning I made a POC and sent it to Sony. After a few days, Sony's security team acknowledged the bug and fixed the vulnerability.
My main takeaway from this experience is that we grossly overestimate how difficult security vulnerabilities are to find and perform. In most cases, the more severe the issue, the simpler it is to reproduce!
Thank You For Reading 👍
Check out my other articles or get to know me at vinaybomma.github.io




Top comments (0)