What is Encryption?
Encryption is the process of changing plain-text information into a seemingly random, or noncoherent sequence of characters known as cipher text via the implementation of complex mathematical algorithims. The purpose for which is to safely deliver a message to a recipient without worry of it being intercepted by a third party or even tampered with.
But what's the point of changing the message if the person receiving it won't be able to understand it either?

That's where an Encryption key comes in handy. The purpose of the key can be to both encrypt and/or decrypt a message. This allows for the recipient of the encrypted message to actually understand our message.
The Strength of an encryption key is determined by how well a hacker can guess it through brute force. A four-bit key (2^4) has 16 possible combinations, which means the hacker has a pretty good chance of guessing it right. Today's standard is a 256-bit key, which produces at 78-digit number which will probably take that same hacker much much longer to guess.
Why use Encryption?
While encryption today is widely used today in our world of technology anywhere from sending a simple text message to protecting your financial information, it has a long history dating all the way back as far as 600 BC. In ancient wars, the Spartans would use an item called a Scytale, which is a piece of leather wrapped around a wooden pole. The piece of letter would consist of letters when unwrapped, were meaningless. Only when this leather strip was wrapped around a correctly sized rod, would the true message reveal itself.
Fast forward a little ways down the road in 1918, a German engineer by the name of Arthur Scherbius invented the Enigma machine, which was later integrated by the German military to send coded messages. This device was deemed uncrackable by other nations and was considered one of Germany's strongest weapons as it allowed them to send messages without the need to worry that their enemies would be able to decipher it.
It wasn't until the invention of the bombe machine that Germany's infamous Enigma machine met its match. The bombe machine was a large electro-mechanical device used by British cryptologists like Alan Turing to decipher the Enigma machine's coded messages which ultimately change the tides of war in the Allies' favor during World War II. The Imitation Game, which is a fantastic movie which goes more into detail about this topic. It features Benadryl Cucumberpatch as Alan Turing and explains the functionality of his bombe machine much more in depth. But for simplicity purposes, you can consider the bombe machine as one of the first electronic decryption devices.
This was not intended to be a history lesson, but I just wanted to show you the big scope that encryption has in our lives and the benefits of being able to securely send messages across our data and even across the world. Back then, the main purposes of encryption was to prevent our enemies from knowing our secrets. Well, not much has changed. In the context of using encryption in our daily lives, its to prevent hackers from maliciously using the information we send out.
Types of Encryption
There are 2 main types of Encryption, Symmetric and Asymmetric.
Symmetric
We talked briefly about keys and their importance. A symmetric encryption uses only one key to both encrypt and decrypt electronic data. Both parties must have access to this key so that it can be used to decrypt their messages. This method scrambles data so that it cannot be understood by anyone outside of the entities who do not have the key. Typically, symmetric encryptions are faster and able to efficiently send larger pieces of data, albeit less secure than Asymmetric encryption. This is due to the risk of the key being compromised. If any outside party were to have the key, they could use it maliciously to decrypt messages that were intended to be private.
Asymmetric
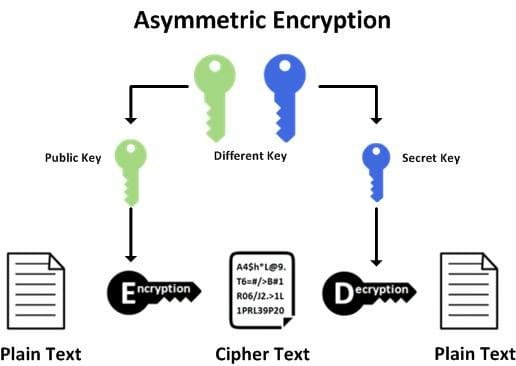
While symmetric encryption uses a single key. Asymmetric uses two keys: a public key, and a private key. The public key is shared with all intended recipients of the message while the private key is known only to the generator of the key. The public key is used to encrypt the message while the private key's purpose is to decrypt. Asymmetric encryption is preferred over its symmetric counterpart when security is prioritized over speed and where personal identity verification is required.
End-to-End Encryption (E2EE)
I felt I should also mention this encryption method as it differs slightly from the above. This encryption method can be mistakenly confused with symmetric encryption because it only requires one key. However, where it differs is the fact that the key to decipher is known only between the sender and recipient. The third party that is responsible for sending the encrypted message does not have access to this key, therefore they do not know the contents within it. This is why certain companies who provide end-to-end encryption services can not provide the texts of their customers over to the police.
Notable Encryption Methods
Data Encryption Standard (DES) [Symmetric]
An outdated, but huge step in data encryption, DES was developed in the 1970s as a proposal for its used in protecting sensitive, unclassified electronic government data. It takes a fixed-length (64bit) of text, or its block size, and turns it into a cipher text of identical length. DES then uses a 64 bit key to change the plain text. Technically only 56/64 of the bits are used by the algorithm to make this change, the remaining bits are used for checking parity, or error detecting code. Those 8 remaining bits are discarded afterwards, making the true key length 56 bits. The process for decryption is the same as in encryption, only in reversed order.Triple Data Encryption Standard (3DES/TDES) [Symmetric]
While the DES was a major milestone in encryption, it's 56bit key is considered short in comparison to its same-era decryption techniques. TDES applies the DES cipher algorithm three times to each data block, which increases the key size of DES without having to create a new block algorithm.Rijndael/Advanced Encryption Standard (AES) [Symmetric]
Formerly known as Rijndael, this algorithm was selected to become the Advanced Encryption Standard by the National Institute of Standards and Technology in 2000. Officially published in 2001, AES operates on a 128, 192, or 256-bit key depending on how many rounds of transformations occur on the plaintext (10/12/14 rounds respectively). Compared to DES' 56 bit key, this is much more secure. DES operates on the Feistel Cipher Principle, which divides the block into 2 before it transforms plaintext while AES works on a substitution & permutation principle. AES is also faster than DES because it uses a more mathematically efficient algorithm.
Blowfish Cipher [Symmetric]
Designed in 1993, this encryption method is still considered strong to this date as there are no notably effective cryptanalysis methods. It was initially designed by Bruce Schneier to be a general purpose algorithm to replace DES. Similarly to DES, this algorithm uses the Feistel Cipher principle and uses a 64-bit block size. However it's key length can range anywhere from 32 bits up to 448 bits and runs the plain text through 16 rounds of transformations. Due to the block size, it is not recommended to use this encryption technique on files larger than 4GB.Twofish [Symmetric]
The Twofish algorithm was amongst the top 5 competitors including the aforementioned winner Rijndael to become the Advanced Encryption Standard. It is the successor to the Blowfish method, however the latter is still more widely used due to it being around longer. While blow fish ciphers data blocks of 64 bits, Twofish ciphers data blocks of 128 bits. One of the key factors that this method was not chosen of Rijndael was due to its encryption speed, although it has been noted to be slightly faster when operating with 256 bit keys.Rivest-Shamir-Adleman (RSA) [Asymmetric]
This method, which derives its name from its designers Ron Rivest, Adi Shamir, and Leonard Adleman, is one of the oldest and widely used algorithms for secure data transmission. As this method is asymmetric, it uses a public encryption key and a private decryption key. The public key is based on two large prime numbers, which are kept secret. Only someone with knowledge of the two prime numbers would be able to successfully decode/decrypt a file. The main reason this method is highly secured is because of the difficulty it takes to factor the produce of the two large secret prime numbers. While secure, this method is also quite slow, making it not suitable to directly encrypt user data. It is more commonly used to transmit shared keys for symmetric-key cryptography.
To Summarize
Understanding data encryption is the first step to keeping your information secure, whether its a private text message or a company email. No matter how you look at it, encryption provides so a lot of protection in the form of:
- Authentication: being able to verify a file/message's origins
- Nonrepudiation: prevents the message sender from being able to deny sending a message.
- Security: prevents unwanted entities from reading your data
- Integrity: verifies that the message/file has not been tampered with since it was sent











Top comments (1)
[[..Pingback..]]
This article was curated as a part of the #55th Issue of Software Testing Notes Newsletter.