Clickjacking is a widely used cyberattack technique where users are tricked into clicking on something without realizing it's harmful. Clickjacking attacks can lead to serious problems like data theft and financial fraud, damaging organizations' reputations.
According to the Javelin 2022 Identity Fraud Study, 22% of U.S. adults have been victims of account takeover attacks. But here's the good part. The Open Web Application Security Project (OWASP) provides key defenses and tips to fight against these threats. They have a detailed guide on clickjacking and identified clickjacking as one of the top three security risks in their latest report.
Here's a comprehensive guide to help you grasp clickjacking, how it operates, and the best practices endorsed by OWASP to combat clickjacking attacks effectively.
What is clickjacking, and how does it work?
Clickjacking is a cunning cyber attack technique that fools users into clicking on hidden elements on a webpage. It works by overlaying a transparent layer on top of the visible content to capture clicks meant for the underlying page.
For example, an attacker could load a bank's website in an iframe, overlay a fake button precisely on top of the "Transfer Funds" button, and trick users into clicking it. The user intends to click the fake button, but their click goes through to the hidden real button, transferring their money without realizing it.
Here's how a clickjacking attack typically works:
- The attacker creates a fake page with a deceptive interface. For example, a button labeled "Claim Your Prize!"
- Load the target website in an invisible iframe behind their fake page.
- Using CSS, precisely position the iframe to overlap key elements like buttons on the target site.
- Trick victims into visiting their page using phishing links.
- When the user clicks the button, their click is hijacked to perform a hidden action on the target site, like submitting a payment.
Clickjacking can lead to severe consequences, ranging from stolen login information to malware installation, data deletion, fund transfers, or even posting social media updates without the user's knowledge or consent.
How to Detect and Prevent Clickjacking
OWASP offers extensive guidance on detecting clickjacking vulnerabilities and implementing effective defenses. As a leading authority on web app security, following OWASP's recommendations is vital for securing against clickjacking.
OWASP suggests creating a basic proof-of-concept page with an iframe loading the target site to test if a website is vulnerable to clickjacking. If the target site loads successfully within the iframe, it likely has insufficient clickjacking protections.
OWASP outlines both client-side and server-side methods to prevent clickjacking attacks:
Client-Side Defenses
- Frame-busting scripts -- JavaScript that prevents the page from being loaded in a frame
- Intersection Observer API -- A modern JavaScript API that detects if a page element is visible to the user, which can identify hidden overlays
- Browser extensions -- Add-ons like NoScript and NoClickjack help block the framing of pages
Server-Side Defenses
- X-Frame-Options header -- Instructs browsers whether a page can be framed or not
- Frame-ancestors directive -- A Content Security Policy directive to allow or deny page framing
- SameSite cookies -- Prevents session cookies from being sent cross-origin, breaking clickjacking attacks relying on sessions
OWASP recommends using multiple defenses together for optimal protection. Relying solely on frame-busting scripts is not enough, as they are prone to failure. A robust clickjacking prevention approach should include security headers like X-Frame-Options and frame-ancestors policies.
What is the OWASP Clickjacking Cheat Sheet, and why do you need it?
The Open Web Application Security Project (OWASP) is a nonprofit organization focused on improving software security. OWASP maintains a series of cheat sheets that act as simplified guides to essential security practices, covering cross-site scripting, authentication, cryptography, and more.
OWASP's clickjacking cheat sheet follows this tradition, providing website owners, developers, and security professionals with a comprehensive guide to defending against clickjacking.
The OWASP clickjacking cheat sheet covers the following:
- An introduction explaining clickjacking risks.
- Clickjacking attack examples.
- Testing methodology to detect vulnerabilities.
- Client-side and server-side prevention techniques.
- Implementation guidance for defenses.
- Tools and resources for protection.
### Download your free Enhanced OWASP Clickjacking Cheat Sheet
The Relationship Between Clickjacking and Website Spoofing
Clickjacking and website spoofing are closely related threats often used in combination during cyberattacks. Here's how:
Understanding Website Spoofing
Website spoofing refers to creating fake websites that mimic the look and feel of legitimate websites. Attackers copy the original website's front-end design, branding, and content to make the fraudulent website appear authentic.
Clickjacking as an Entry Point
Clickjacking is then used to trick users into interacting with the spoofed website. By loading the fake website into an invisible iframe and overlaying decoy buttons, attackers can hijack clicks meant for the decoy website and route them to the spoofed website instead.
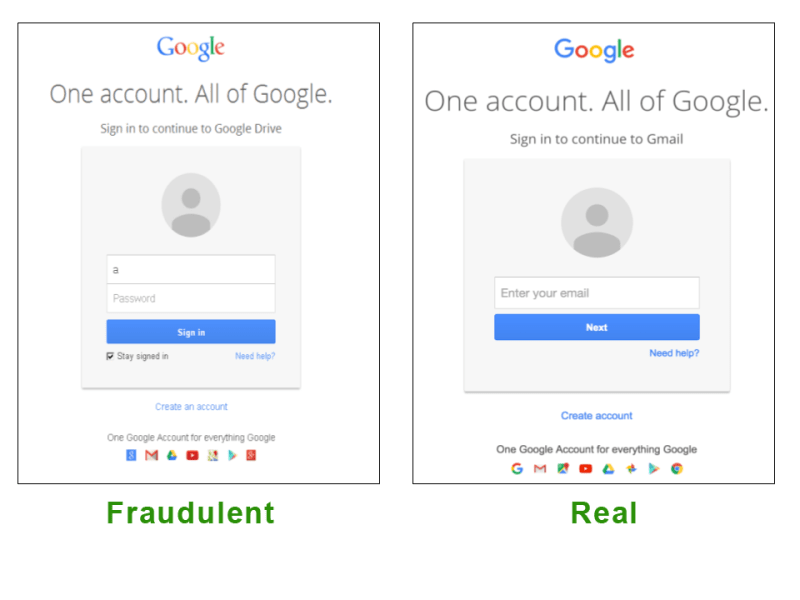 A Deadly Combination at Work
A Deadly Combination at Work
When these techniques unite, attackers can successfully impersonate trusted brands and defraud users. Here's how website spoofing and clickjacking work together:
- 1. The attacker spoofs the target website by scraping and cloning its content. This results in a fake website hosted elsewhere that looks identical to the original.
- The attacker then loads this spoofed website into an invisible iframe on their malicious page.
- Using clickjacking techniques, the attacker overlays fake buttons and links over critical elements of the spoofed site within the iframe.
- When users visit the attacker's page and click the visible decoy buttons, their clicks are hijacked and routed to the spoofed site's hidden elements instead.
- As a result, users unwittingly perform actions and submit data on the fake website, believing they are on a legitimate site.
With its ability to manipulate user interactions, clickjacking provides the ideal delivery mechanism to weaponize spoofed websites and effectively deceive users. Without clickjacking, spoofed sites might struggle to attract users with such ease.
As you can see, defending against one cyber attack is not enough since they are all connected. Businesses must take necessary steps to safeguard their users against all types of attacks. That's where tools like Memcyco come in.
How Memcyco Helps Combat Website Spoofing
Memcyco offers an innovative solution that helps defend against website spoofing attacks. It provides real-time fraud detection and alerting when a website is spoofed or cloned by attackers. When a fake replica of the website is created, Memcyco identifies it and immediately notifies the security team.
In addition, Memcyco's solution protects customers by displaying visual alerts when they access a spoofed website. These alerts use Memcyco's patented spoof-proof digital watermarking technology to indicate that the site is fraudulent. This prevents customers from being deceived and blocks them from submitting data or taking action on the fake website.
Other key benefits of Memcyco include:
- Zero-day protection even before spoofed sites are detected by threat intelligence.
- Agentless implementation without any code changes required.
- Precision attack insights detailing impacted customers and their level of exposure.
- Tamper-proof end-user warnings when accessing spoofed websites.
- Customizable customer alerts tailored to the brand.
This powerful combination of capabilities enables enterprises to proactively combat website spoofing attacks, defend their brand reputation, and safeguard customers from fraud.
Safeguard Your Digital Assets Against Clickjacking
A recommended strategy is following OWASP's guidelines to defend your businesses against clickjacking. However, cyber threats are rapidly evolving, and attackers often combine multiple techniques to gain access to sensitive information. For example, clickjacking is often used alongside website spoofing. Hence, businesses must use specialized tools like Memcyco to help prevent these complex attacks.
Memcyco offers live detection of fake websites and unchangeable alerts, allowing you to warn users about false sites and prevent brand impersonation. Memcyco lets you anticipate threats, build trust, and reassure customers of your online brand's authenticity.
Get started with Memcyco to fortify your online defenses and protect against clickjacking threats.





Top comments (0)