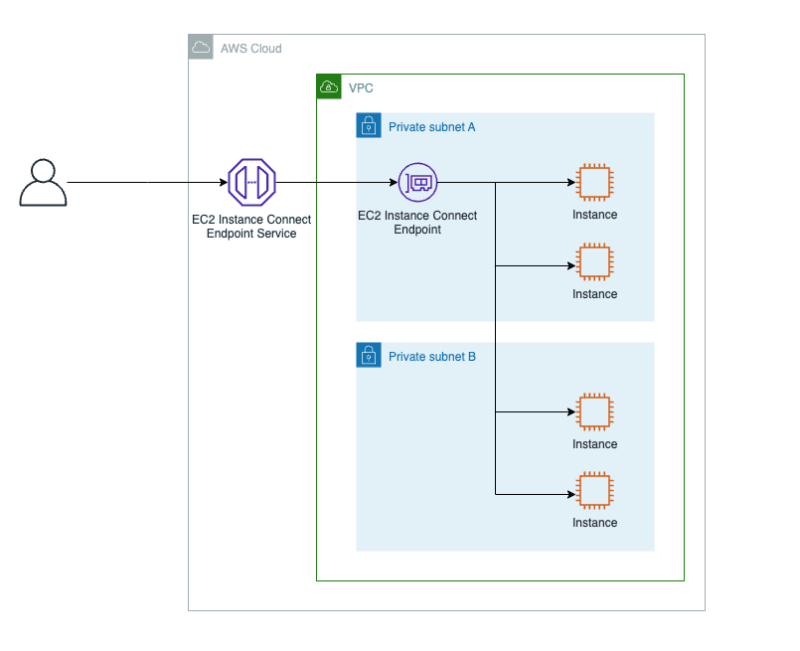
Amazon Web Services (AWS) has unveiled a fresh feature known as the Amazon EC2 Instance Connect (EIC) Endpoint. This innovative feature permits users to establish a secure connection to their instances and various resources within the Amazon Virtual Private Cloud (Amazon VPC) directly from the internet.
Previously, users had to navigate through a somewhat complex process to establish connections. They had to connect to a bastion host with a public IP address set up by their administrator over an Internet Gateway (IGW) inside their VPC. Further, they had to use port forwarding to reach their intended destination. The advent of the EIC Endpoint erases the need for an IGW within their VPC, a public IP address on their resource, a bastion host, or any agent to establish connections to their resources.
The EIC Endpoint marries identity-based with network-based access controls, aiming to meet an organization's security requirements. It promises to provide isolation, control, and comprehensive logging. Furthermore, the EIC Endpoint eases the load on the organization's administrator by removing the operational tasks associated with maintaining and updating bastion hosts for connectivity. It is compatible with the AWS Management Console and AWS Command Line Interface (AWS CLI), while still offering users the flexibility to use tools like PuTTY and OpenSSH.
The EIC Endpoint operates as an identity-aware TCP proxy and provides two operating modes. The first mode allows secure WebSocket tunneling from the workstation to the endpoint using AWS Identity and Access Management (IAM) credentials. This mode enables users to connect to resources in the usual way. Meanwhile, the second mode comes into play when not utilizing the AWS CLI. The Console guarantees secure access to VPC resources by evaluating authentication and authorization before allowing traffic into the VPC.


Top comments (0)