There is no doubt that the world's workforce is becoming more remote, particularly in tech as developers can now work from any location in the world. But there are a large number of new obstacles that come with this. The most pressing is security.
Take the current COVID-19 health crisis. From one day to the next, countries are going into quarantine and forcing companies and developers into working remotely. I for one am writing this from my home office in Paris, sipping filter coffee while looking onto the empty streets in a complete lock-down that started last week.
We are all trying to rapidly adjust to a new workflow from our makeshift workstations. As this crisis unfolds, we are seeing a drastic change in the remote infrastructure as it is pushed to its limit. This is creating an unprecedented security challenge that may not be a priority for many companies.
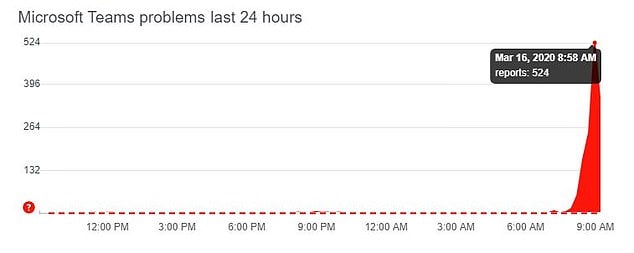
I recently got an alert to say that Microsoft Teams, a platform to help manage remote workers and collaboration, crashed under the new pressure of millions of users. Likewise the video streaming company Zoom, which is now facing serious security breaches, went from 10 million daily users in December to 200 million daily users in March! These are obvious signs of the strain we are putting on digital infrastructure as this crisis unfolds. Teams that are only familiar with being centralized on a secure network, are now at home on a private WiFi network trying their best to keep websites, services, platforms and apps functioning.
Image taken from Downdetecter, 16 March 2020
Why does remote work present a security risk?
Remote working is not necessarily less secure, if done right. It is extremely important for remote teams to have operational frameworks and tools in place to deal with the challenges that are unique to remote teams. Especially when it comes to issues as urgent as security.
If you make secret management too painful for developers, it becomes all too tempting to circumvent the restrictions. Now let's add to this balancing act different geographies, time zones and unreachable co-workers. The temptation to send a secret over Slack, email or to quickly hardcode secrets into the source code becomes increasingly hard to resist.
In addition to internal operational control, we must now also consider external factors, such as unsecured personal wifi-networks and personal machines. These all add to the potential of secrets being leaked into unsecured locations.
The once clear delineation between personal and professional activity suddenly becomes blurred when you are sharing a single machine and mixing personal git repositories with professional repositories. You can easily find yourself in the worst case (yet common) scenario of mistakenly uploading secrets and corporate code into personal repositories. All these factors combined increases the attackable area of the organization, when secrets that were once secured to a central location are now sprawled across multiple platforms and tools.
Unsecured messaging systems like Slack and email are known to be high-value targets for attackers through phishing campaigns. Once an attacker has admin access to your company's Slack, they are a simple search away from gaining access to your sensitive information. The normal conditions that could help identify an external threat also begin to unravel, as IP addresses of all developers can change daily. Currently, the number of reported phishing campaigns has drastically increased with the COVID-19 crisis unfolding as attackers piggy-back onto public panic.
8 steps to making remote work more secure for development teams
1. Get visibility over secrets shared in your repositories
Repositories are not appropriate places to store secrets, it is important that you have complete visibility of not only public repositories but also of your private repositories. Having secrets in private repositories:;
- increases the chances of a secret ending up on a public repository.
- Perhaps more importantly though, now that employees are increasingly working from home, it is more likely company code will end up on unsecured personal workstations or be transiting through unsecured networks, meaning secrets within that source code could be accessible by a malevolent actor.
We recommend signing up to GitGuardians Internal Repository Monitoring to scan your repositories. The tool is free for small teams and will allow you to scan your git history for secrets while continuously scanning incremental changes as well.
2. Establish best practices sharing sensitive information
For a helpful guide on best practices for securing and sharing API keys, you can check out a GitHub cheatsheet here. It’s a great document to share with your staff to make sure they are using the best practices.
3. Know how to remediate compromised credentials
Make sure the steps on how to revoke a credential for each external service is documented along with the impact revoking each credentials will have. You can find here an article about revoking and removing compromised credentials
4. Invest in multi-factor authentication on all services.
2 factor authentication improves security drastically when it comes to services and assets you want to protect. Make sure 2FA is set up on all “Seed” accounts like company emails. (A seed account is an account that can grant access to other services. Email and social media accounts are examples of seed accounts, “log in with Gmail”).
5. Work towards implementing a Zero Trust framework
Depending on the organization it may be appropriate to implement a Zero Trust framework beyond multi-factor authentication. Complete implementation is always a process and a considerable investment but introducing additional Zero Trust measures like SSO and introducing policies to block/limit/approve access decisions to enterprise resources can strengthen security significantly, particularly for remote teams.
6. Encourage a culture of self education
By providing clear and basic information, including how to protect their devices, will help you and employees stay ahead of threats.
Remote workers have access to data, information, and your network. This increases the temptation for bad actors. Warn your employees to expect more phishing attempts, including targeted spear phishing aimed at high profile credentials. Now is a good time to be diligent, so watch out for urgent requests that break company policy, use emotive language and have details that are slightly wrong and provide guidance on where to report those suspicious messages.
7. Practice good security hygiene
Good security practices always go back to basics. Practicing good security hygiene means to rotate vulnerable access credentials regularly and to restrict permissions associated with your keys with role-based access controls.
8. Be prepared for a breach
Regardless of whether your team is working remotely or not, it is important to have an action plan in place in case secrets get shared. Make sure the whole team understands what that plan is and implement a culture of open, transparent communication.
We are certainly facing difficult times that are bringing new challenges at record speeds. It is unfortunate that while we are adapting, there are people out there that are using this as an opportunity to exploit us. GitGuardian is, and always will be free for developers and small teams so if you are working with a remote team, consider implementing the free tools GirGuardian have to allow you to continue thriving during the times ahead.
👉Try GitGuardian | automated secret detection
Free 0$/month
Monitor your public activity anywhere on GitHub
Real-time alerting by email
article originally published on GitGuardian's blog: 8 Steps to keep remote development teams secure



Top comments (0)