When building or maintaining your API, there comes a point when your focus turns toward security. How can you secure your API, or how can you ensure the security of your API?
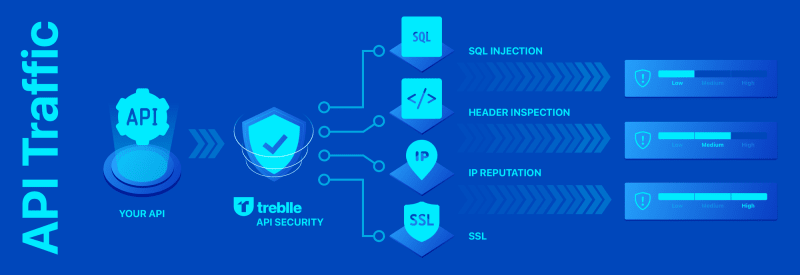
At Treblle, we have been working hard to answer these questions for you. With our upcoming API Security functionality, you can see a more detailed API Security score, from SQL injection to header inspection and IP reputation. All of these factors contribute to how secure your API is. Let's dive into how we can achieve this.
Your API score is evaluated constantly as more requests come through, so you get your security insights in real-time as and when it changes. It ranges from default, which means that there is no threat level, all the way up to high, which means you really should pay attention to this.
Treblle API Security
With all things security, we can only advise you on our findings and assessments. By default, all requests that come into your projects in Treblle start at a level of default, which means that you are good to go. However, we begin analyzing this request, and this level can increase. Even if your request is ranked at default or low, you should still ensure security from your side. We only assess specific criteria. Always remember that attackers will try things nobody thinks of to gain access to your systems.
How it works
SQL Injection
Let's start by talking about SQL Injection, which used to be the most common form of attack - but modern frameworks have begun adding built-in tools to help prevent this. However, it doesn't mean that, as developers, we should rely on these without taking measures ourselves. Attackers will look to gain access or retrieve data from your system using SQL Injection to access your database directly. As you can imagine, even a low threat level here is something to worry about.
IP Reputation
IP Reputation is an interesting metric, as a potential attacker will likely use a proxy or tor network to mask their actual location. However, there is a database that we have access to that is used around the world where these proxies and tor networks are reported, which means that we can spot potential attackers based on commonly used IPs.
Header Authorization
API requests can be protected using an Authorization header so only authorised users can request certain areas of your application. This is a common practice in the development world. However, only some use this. Even public API endpoints should have authorization so that you can identify potential issues with users gaining access or attempting to gain access to places they shouldn't. We can be more confident in the users accessing your API by checking if an Authorization header is available.
SSL
Using an SSL certificate on your API ensures an encrypted network connection between your API and your users. There are many benefits to using an SSL certificate on your API beyond simply encrypting the network traffic, so we recommend using one. From self-signed certificates to purchased certificates, each has different benefits and signing algorithms to ensure the encryption of your network traffic. As well as using an SSL certificate, you can use the Strict Transport Security header to ensure that potential attackers do not attempt to spoof certificates or try and force a HTTP connection to your API.
IDs
One potential place often overlooked by developers is exposing your database IDs in your URLs. While this is a relatively low-level threat, it exposes your resource identification approach, enabling potential attackers to try auto-incrementing the identifier to access resources they should not have access to.
Some Best Practices
One great way to prevent DDoS attacks is to enable rate limiting on your endpoints by using the X-RATELIMIT-LIMIT header, which will stop potential attackers from making persistent requests and block them from fulfilling their requests earlier on in the lifecycle.
Having a consistent content-type header will enable you to ensure that the requests coming into your API are protected against things such as remote code execution and cross-site request attacks. Additionally, using the X-CONTENT-TYPE-OPTIONS header will prevent potential attackers from performing MIME sniffing attacks. Pairing this with the accept header will help ensure no possible mime-type tampering attacks.
Sometimes attackers will attempt to perform a drag-and-drop style clickjacking attack. To protect against this, you can set the X-FRAME-OPTIONS to "deny".
A great and simple way to ensure attackers use the correct HTTP verbs for your endpoints is to lean on the Allow header. This will stop anyone from sending a POST request to your GET endpoint, which can cause challenging issues if you are not careful.
A Proactive Approach to API Security
This is not an exhaustive list of things you can do to ensure your API security. However, it is a handful of things that we at Treblle will be checking for you on each request to ensure that you are as protected as you can be. We always recommend going that extra mile when it comes to security on your APIs - and we will be expanding our new API security functionality to start detecting anomalies for you so that you can take a more proactive approach to security.




Top comments (0)