One day, I wondered why I couldn't transfer my NFC door access card to my phone, given that my phone is an NFC reader/writer. There must be a way to do this so I don't have to carry the NFC card.
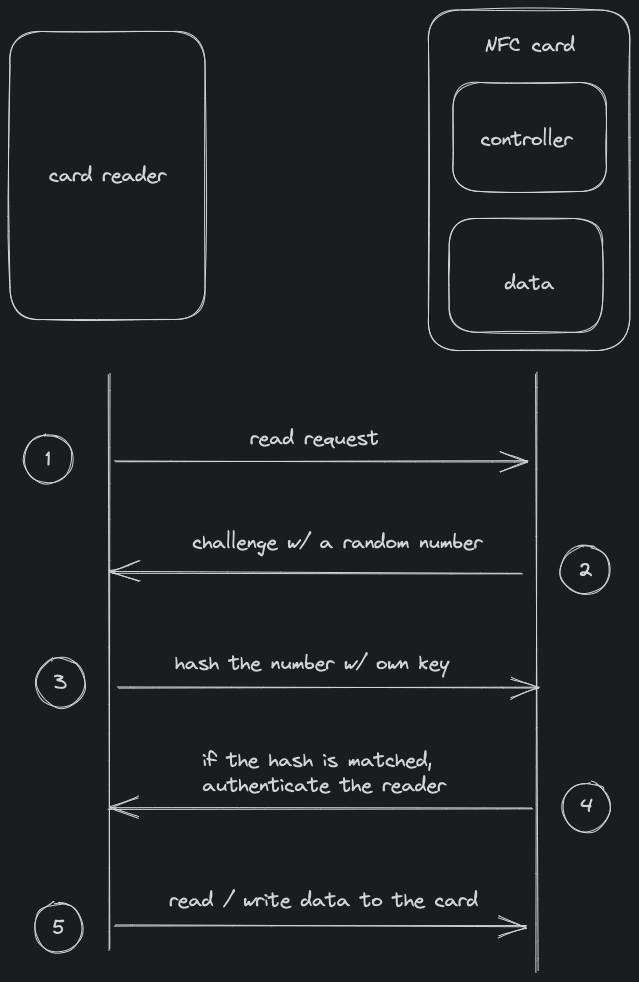
Above is a simplified, high level version of how NFC authentication works. Details like storage sectors, key_a key_b ...etc are all abstracted away.
- reader: send read request to the NFC card
- card: challenge the reader with a random number
- reader: hash the random number with the key correspond the id of NFC card
- card: check if the hash matched with the hash by its own key
- reader: able to read / write if the hash is correct
The key take aways of the above authentication flow are:
- there is a controller in NFC card/tag to restrict the read and write of data
- every NFC card has an ID, reader select corresponding encryption key by the ID
- data are encrypted / decrypted by the key(s)
- you cannot read the data if you don't have the correct key in your reader
So the conclusion is: you need to have the correct encryption key(s), either given by the NFC card owner, or hack it yourself 😏
There are plenty of lib, tools, tutorials to hack the NFC keys. I successfully hacked and copied it onto my Android phone. However, I didn't quite understand what was happening... so I did some research and wrote this article. Hope it helps.
questions?







Top comments (0)