Encryption refers to the encoding of data. As data is sent and transferred from a user to a server, algorithms encrypt data and decrypt the data once it has reached the intended destination. The only way for the data to be decrypted is if that destination provides the proper key. The process of encryption can happen in so many different ways; first we’ll explore the two types of encryption and a couple of protocols & then we’ll take a look at the implications of a few real world examples.
Symmetric & Asymmetric Encryption
There are two leading schemes of encryption: symmetric and asymmetric. Symmetric encryption requires both the sender and receiver to have the same key. When both the sender and receiver have the same key, the algorithm is able to use the same method to encrypt & decrypt and thus is able to process more quickly. However, what must be considered is what happens if the recipient does not have the key… because the key must be sent to them, the key is vulnerable to being intercepted. This is why symmetric encryption is best for use within small, closed networks.
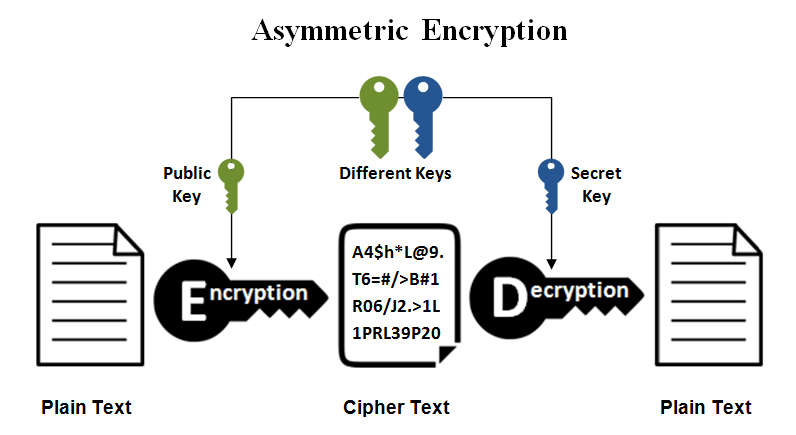
Asymmetric encryption, on the other hand, operates a bit slower but is considered to be more secure. This method utilizes a public key in addition to a private key. It is the public key that encrypts the data... everybody has access to the public key. The only way to decrypt the data, though, is to have access to the private key.
These schemes are deployed within a wide range of cryptographic protocols; each protocol has its own set of rules and methods to determine the functioning of an algorithm. The two you've probably encountered most frequently are Transport Layer Security and Secure Shell.
TLS & SSH: Examples of Encryption Protocols
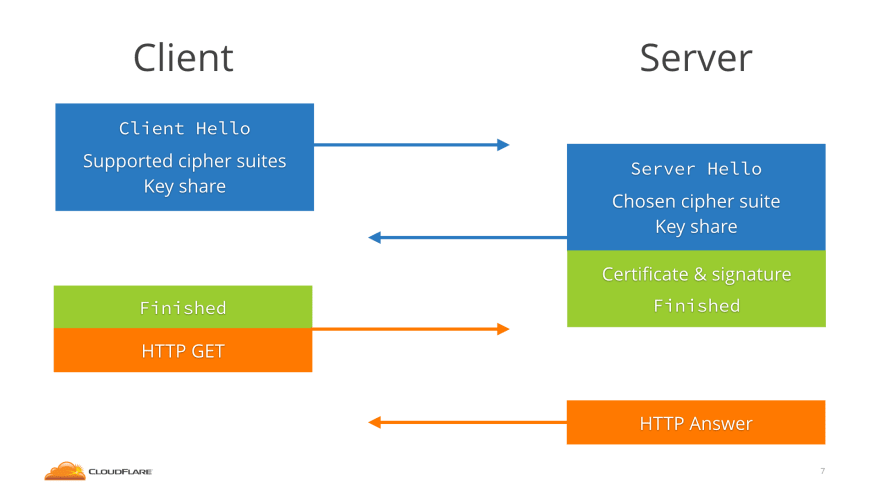
Formerly known as Secure Sockets Layer (SSL), Transport Layer Security (TLS) provides a secure connection between a client and a website's server. The connection between a client and a server begins with a TLS 'handshake' in which asymmetric encryption is used to establish a session-specific key. Once the connection is established, data is transferred via symmetric encryption.
Secure Shell (SSH) allows for network services to be accessed over unsecured networks, and is often used to log into platforms. SSH does this by using asymmetric encryption to authenticate a remote network and consequently its user; all that is needed for authentication is a matching public-private key pair.
Ok, but Encrypted To Which Point?
Encryption protocols all provide secure connections; however, maybe more important is in which direction that connection is secure. Let's place this into context by exploring something that is pretty crucial to our current reality as people living in social isolation: messaging services! They're essential to staying connected these days! Sending a message to someone, whether it is over Facebook, Zoom, Slack, WhatsApp, Signal etc, requires a connection between one user, a server, and another user.
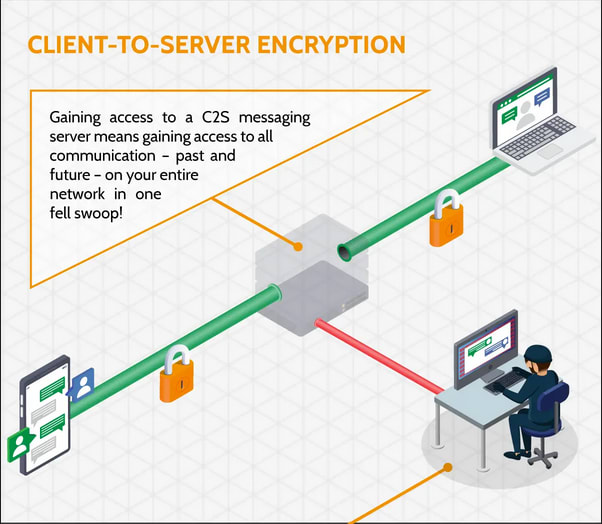
With client-to-server encryption, servers are able to decrypt & store the data it's received from the client. Because that data is sitting decoded in a database, it is susceptible to being intercepted by someone it was not intended for. Think attackers, internet service providers, governments surveilling citizens. When we're sending a message over Slack or Zoom or Facebook, that message is being stored in plaintext on Slack's servers and can be accessed by someone that message was not intended for.
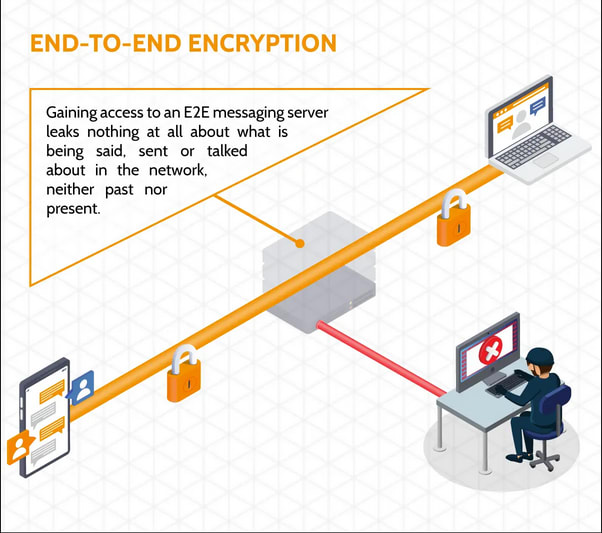
End-to-end encryption, on the other hand, is designed to where the data being sent is only available to the person who is receiving it. The server does not decode the information, generally stores little metadata on the transfer, and simply acts as a traffic router. Examples of this would be Signal, Discord, or WhatsApp.
🔗 🌐 📡 🔗 🌐 📡 🔗 🌐 📡 🔗 🌐 📡 🔗 🌐 📡
In conclusion, plenty of folks have never even considered what happens to the data they shoot into the world wide web and its subsidiaries. As we head into learning about servers and databases, it is my hope that this post was able to prime you with some of the fundamentals of data encryption.






Top comments (0)