🚀 Introduction
In the dynamic realm of cloud infrastructure, the deployment of AWS Transit Gateway stands out as a revolutionary solution. This robust networking service enables seamless connectivity and efficient management of resources across multiple Amazon Virtual Private Clouds (VPCs). Join us on a journey where we unravel the intricacies of AWS Transit Gateway deployment, unlocking new possibilities for your organization's network architecture.
🎯 Objective
Our primary objective is to demystify the deployment process of AWS Transit Gateway, empowering organizations to build a flexible and scalable network infrastructure. From enhanced connectivity to simplified management, our exploration aims to equip you with the knowledge to optimize your network resources and elevate your cloud experience.
🚀 Use Case
Let's dive into a real-world scenario that demonstrates the tangible benefits of AWS Transit Gateway deployment for different departments within your organization.
Sales Department:
Imagine a scenario where the Sales team operates across various regions, each with its dedicated VPC. With AWS Transit Gateway, seamless communication is established between these VPCs, ensuring that sales applications and data are easily accessible. This not only enhances collaboration but also accelerates sales processes, contributing to increased efficiency and faster decision-making.
Marketing Department:
For the Marketing team, running campaigns often involves diverse applications and services distributed across different VPCs. AWS Transit Gateway streamlines the connectivity, allowing marketing resources to interact effortlessly. Whether it's accessing analytics data or coordinating marketing tools, the deployment ensures a unified and efficient network, boosting overall productivity.
HR Department:
In the HR domain, privacy and secure communication are paramount. AWS Transit Gateway facilitates a secure network environment, ensuring that HR-related applications and databases are interconnected with enhanced security measures. This ensures confidential employee data is transmitted securely, aligning with compliance standards and bolstering data integrity.
This use case exemplifies how AWS Transit Gateway deployment caters to the distinct needs of various departments within your organization, fostering collaboration, security, and efficiency.
Transit Gateway Features:
Hub and Spoke Architecture:
Description: AWS Transit Gateway follows a hub-and-spoke architecture, allowing centralized connectivity and management.
Global Reach:
Description: Transit Gateway supports a global network that spans multiple AWS Regions, providing a unified and scalable solution.
Inter-Region Peering:
Description: Facilitates peering between Transit Gateways in different regions, enabling seamless communication across regions.
VPN and Direct Connect Attachment:
Description: Connects remote networks using VPN and AWS Direct Connect, providing secure and reliable communication.
Routing Control:
Description: Offers flexible and granular routing control, allowing customization of the traffic flow within the network.
Network Manager Integration:
Description: Integrates with AWS Network Manager, simplifying the management of global networks and providing a centralized view.
Scale Out:
Description: Scales horizontally to accommodate a growing number of VPCs and on-premises networks, ensuring scalability.
Security Integration:
Description: Seamlessly integrates with AWS security features, allowing the enforcement of security policies across the network.
CloudWatch Metrics and Monitoring:
Description: Provides CloudWatch metrics for monitoring network performance and enabling proactive management.
Resource Group Tagging:
Description: Supports resource group tagging, making it easier to organize and manage resources within the Transit Gateway.
Multicast Support:
Description: Enables multicast traffic support, allowing the transmission of data to multiple recipients simultaneously.
Centralized Network Inspection:
Description: Facilitates centralized network inspection and monitoring for enhanced visibility and control.
Transit Gateway Connect:
Description: Introduces Transit Gateway Connect for simplified VPN connectivity and better traffic engineering capabilities.
VPC Ingress Routing:
Description: Offers VPC Ingress Routing, allowing for more granular control over the egress path of traffic leaving a VPC.
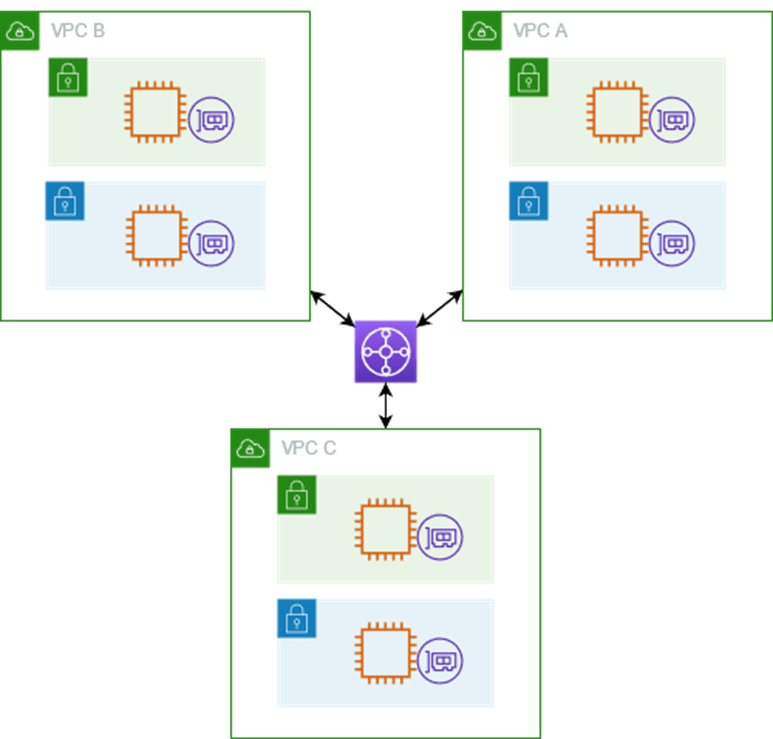
🛠️ Solution Diagram
Tools & Technologies Covered:
- AWS cloud
- AWS vpc
- AWS subnets
- AWS internet gateway
- AWS route tables
- AWS security groups
- AWS EC2 machine
- Transit Gateway
TRANSIT GATEWAY DEPLOYMENT
- Create VPCs
- Create Subnets
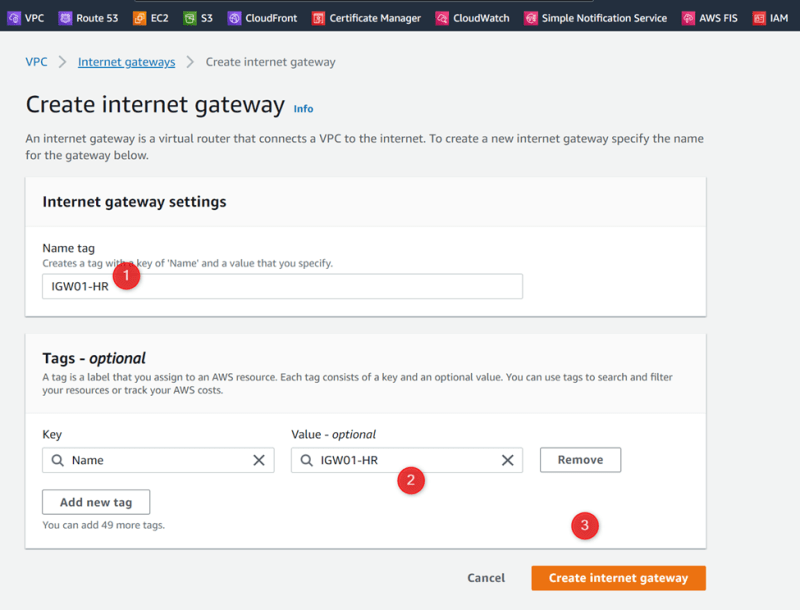
- Create internet gateway
- Attach internet gateway to VPCs
- Create route tables • Subnet association • Add route entries
- Create security groups
- Transit gateway • Create transit gateway • Attach VPCs to transit gateway • Add routes between transit gateway and vpcs • Launch EC2 webservers in each vpcs • Test the transit gateway connectivity
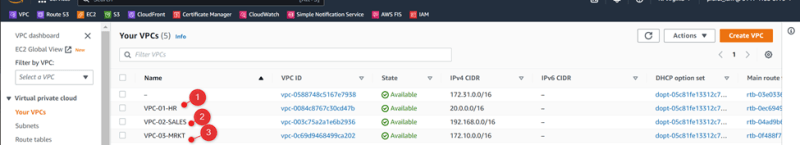
Create VPCs
VPC VPC CIDR Block Availability Zone Availability Zone CIDR Block
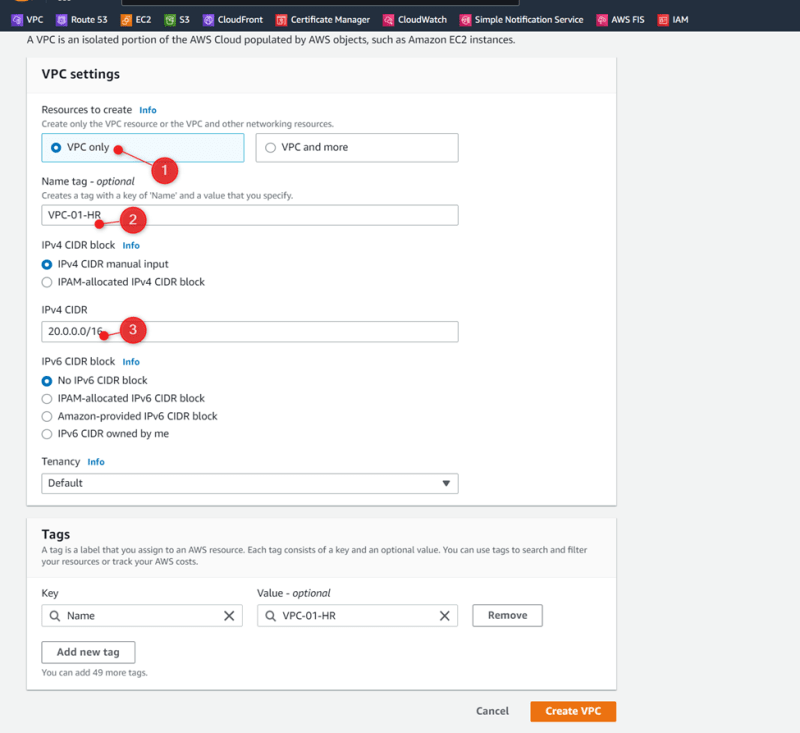
VPC-01-HR 20.0.0.0/16 Us-east-1a 20.0.0.0/24
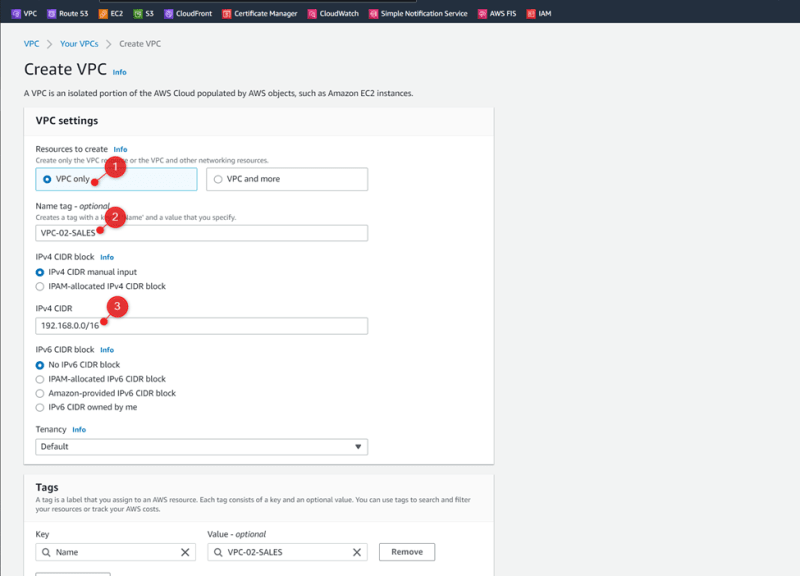
VPC-02-SALES 192.168.0.0/16 Us-east-1a 192.168.0.0/24
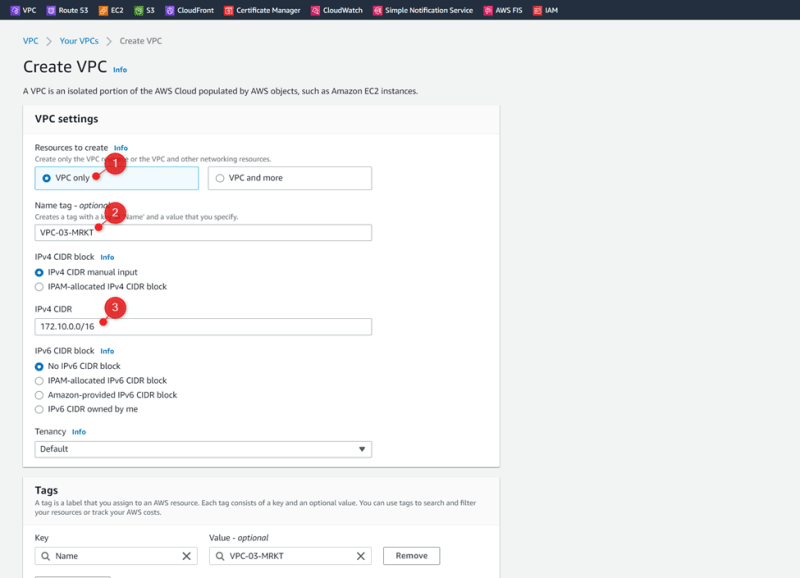
VPC-03-MRKT 172.10.0.0/16 Us-east-1a 172.10.0.0/24
Create VPC-01-HR
Create VPC-02-SALES
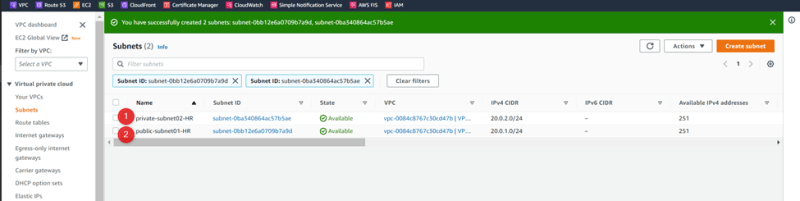
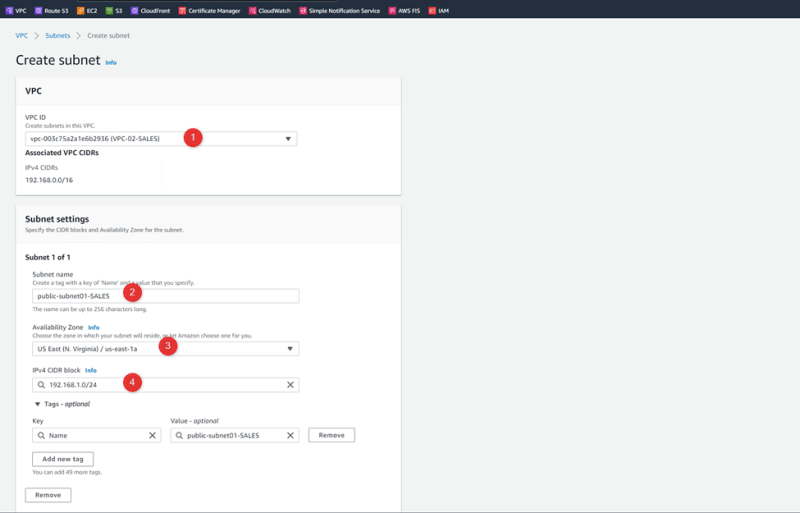
Create Subnets
VPC VPC CIDR Block Availability Zone Availability Zone CIDR Block
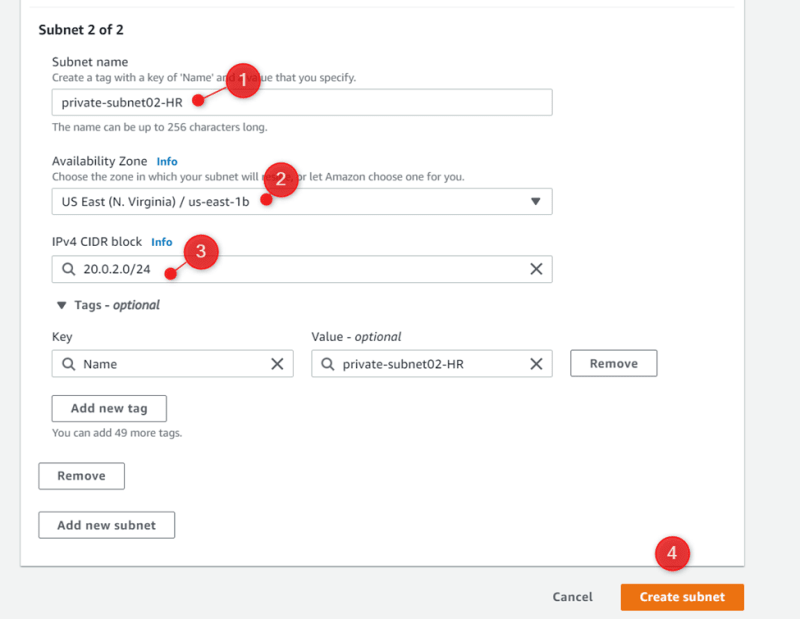
VPC-01-HR 20.0.0.0/16 Us-east-1a 20.0.0.0/24
Public-subne01-HR Us-east-1a 20.0.1.0/24
Private-subnet02-HR Us-east-1b 20.0.2.0/24
VPC-02-SALES 192.168.0.0/16 Us-east-1a 192.168.0.0/24
Public-subnet01-SALES Us-east-1a 192.168.1.0/24
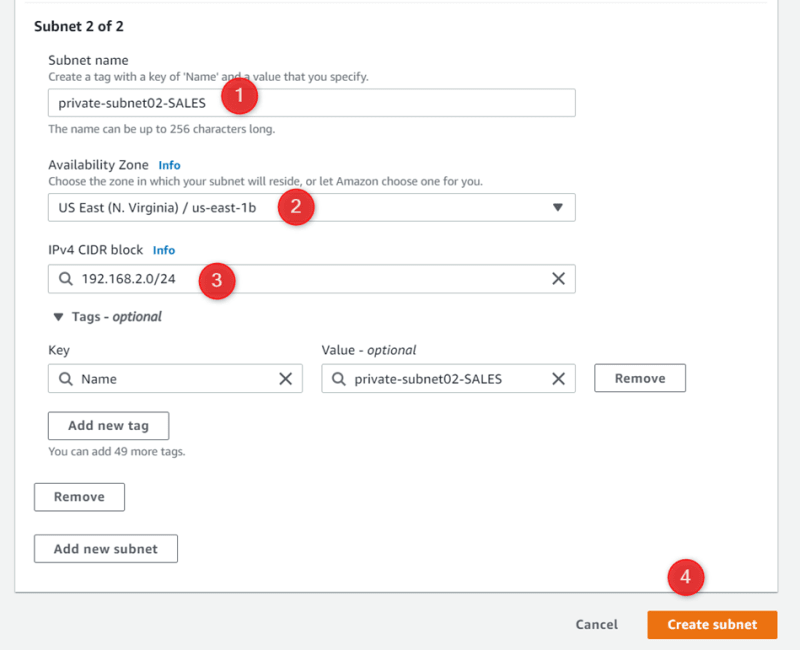
Private-subnet02-SALES Us-east-1b 192.168.2.0/24
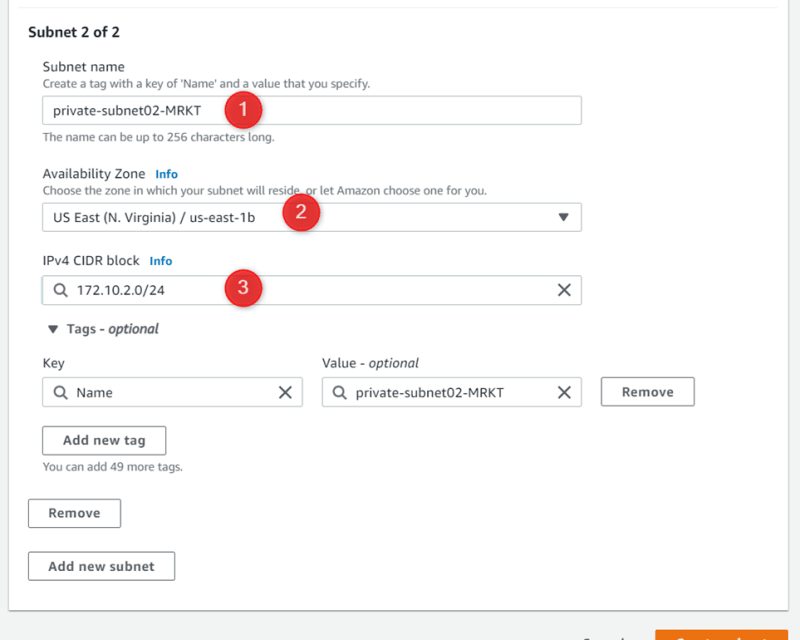
VPC-03-MRKT 172.10.0.0/16 Us-east-1a 172.10.0.0/24
Public-subnet01-MRKT Us-east-1a 172.10.1.0/24
Private-subnet02-MRKT Us-east-1b 172.10.2.0/24
VPC-01-HR 20.0.0.0/16 Us-east-1a 20.0.0.0/24
Public-subne01-HR Us-east-1a 20.0.1.0/24
Private-subnet02-HR Us-east-1b 20.0.2.0/24
VPC-02-SALES 192.168.0.0/16 Us-east-1a 192.168.0.0/24
Public-subnet01-SALES Us-east-1a 192.168.1.0/24
Private-subnet02-SALES Us-east-1b 192.168.2.0/24
VPC-03-MRKT 172.10.0.0/16 Us-east-1a 172.10.0.0/24
Public-subnet01-MRKT Us-east-1a 172.10.1.0/24
Private-subnet02-MRKT Us-east-1b 172.10.2.0/24
Internet Gateway VPC-01-HR IGW01-HR 172.10.0.0/24
VPC-02-SALES IGW02-SALES 172.10.1.0/24
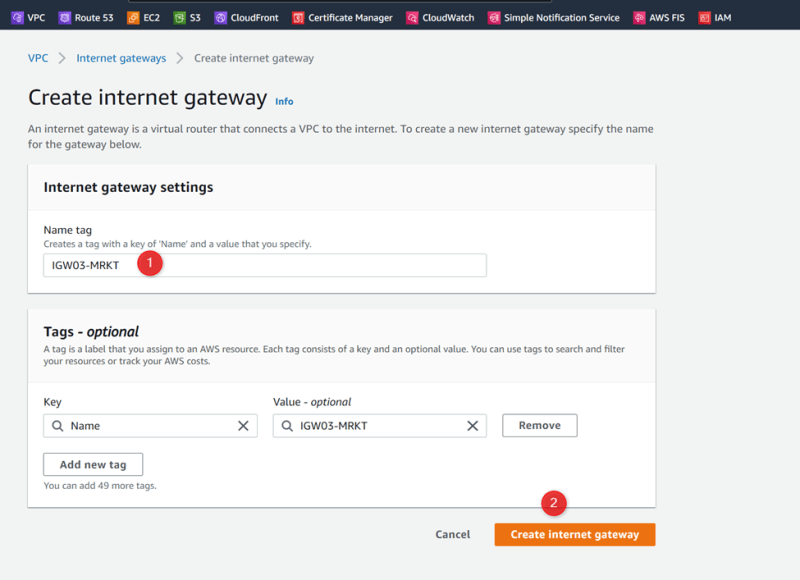
VPC-03-MRKT IGW03-MRKT 172.10.2.0/24
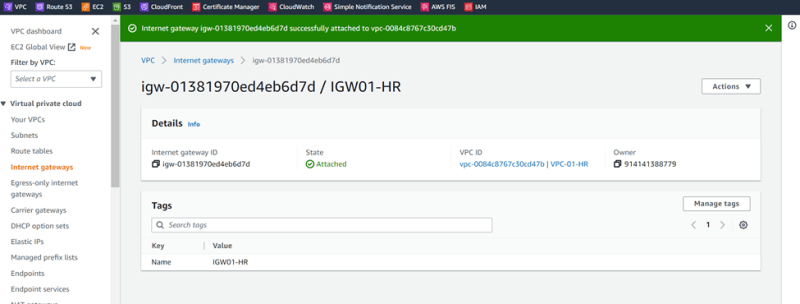
VPC-01-HR IGW01-HR
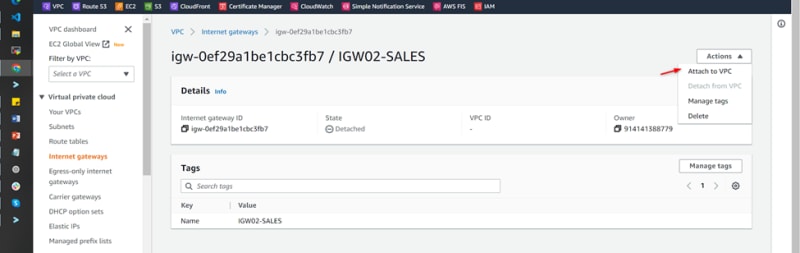
VPC-02-SALES IGW02-SALES
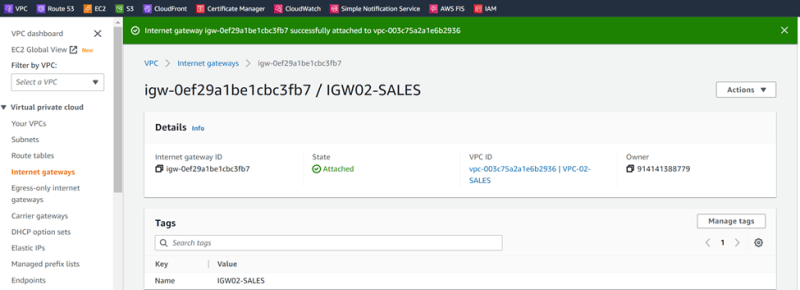
VPC-03-MRKT IGW03-MRKT 172.10.2.0/24
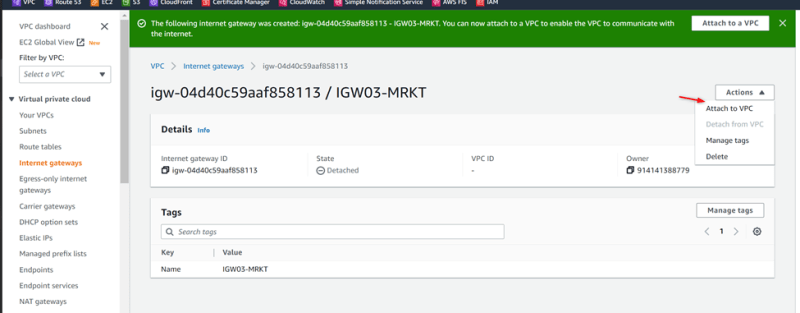
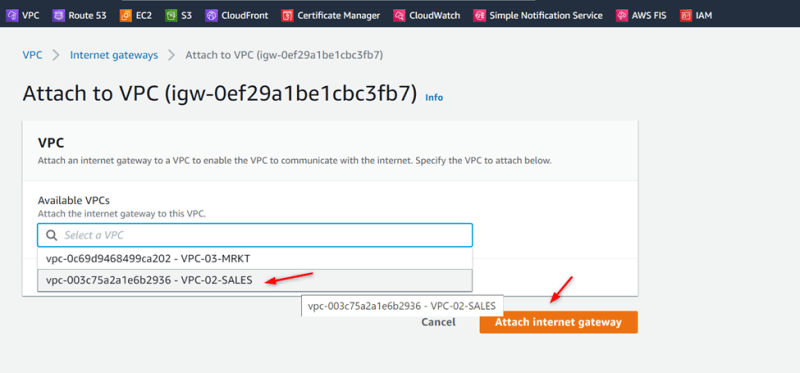
Attached to VPC
VPC Route Tables
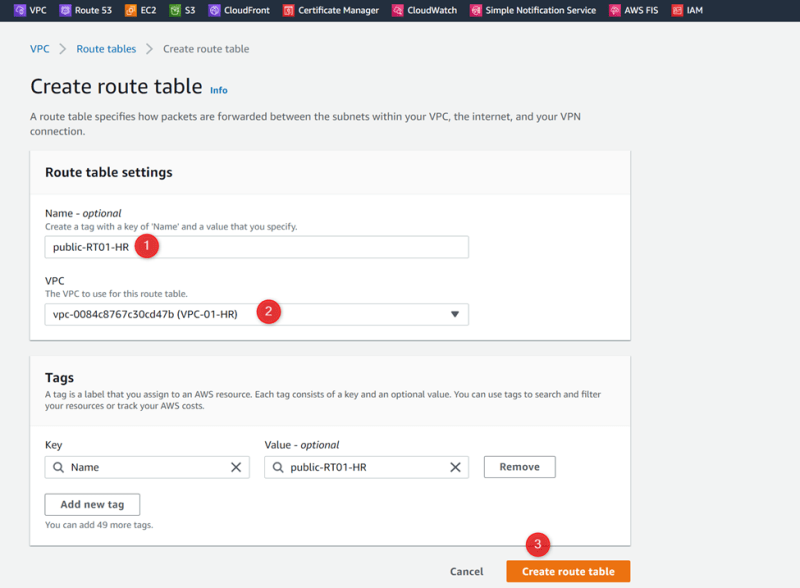
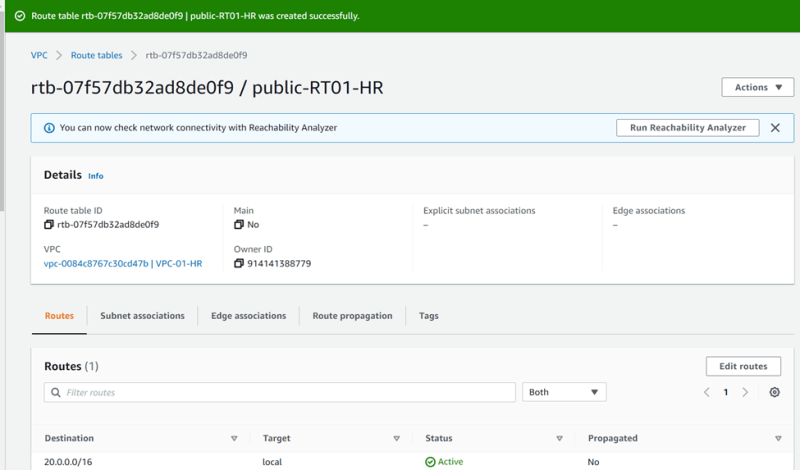
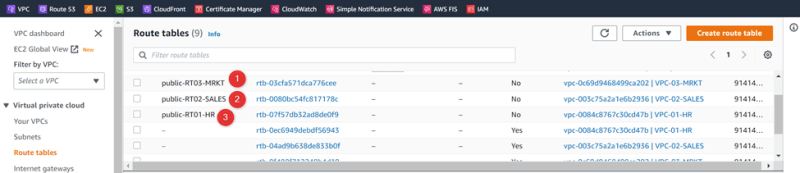
VPC-01-HR Public-RT01-HR
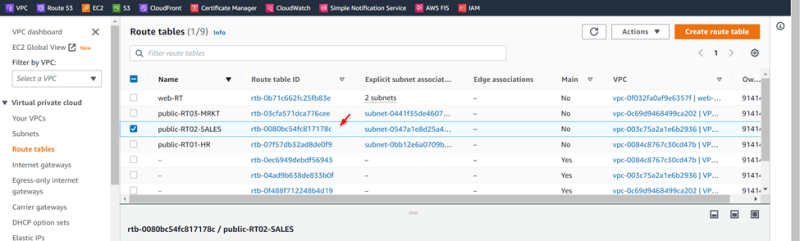
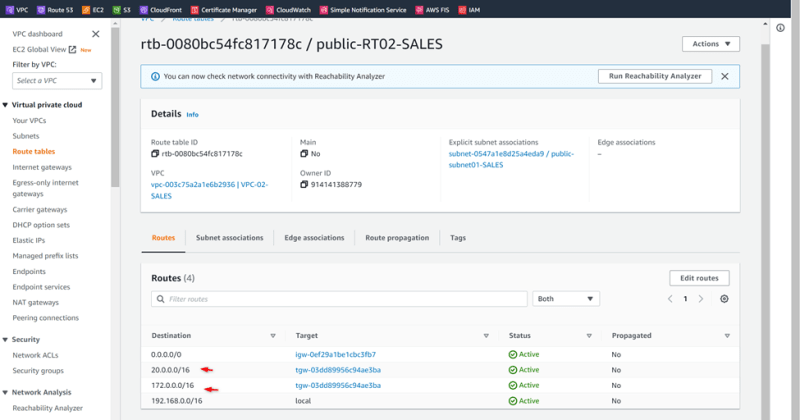
VPC-02-SALES Public-RT02-SALES
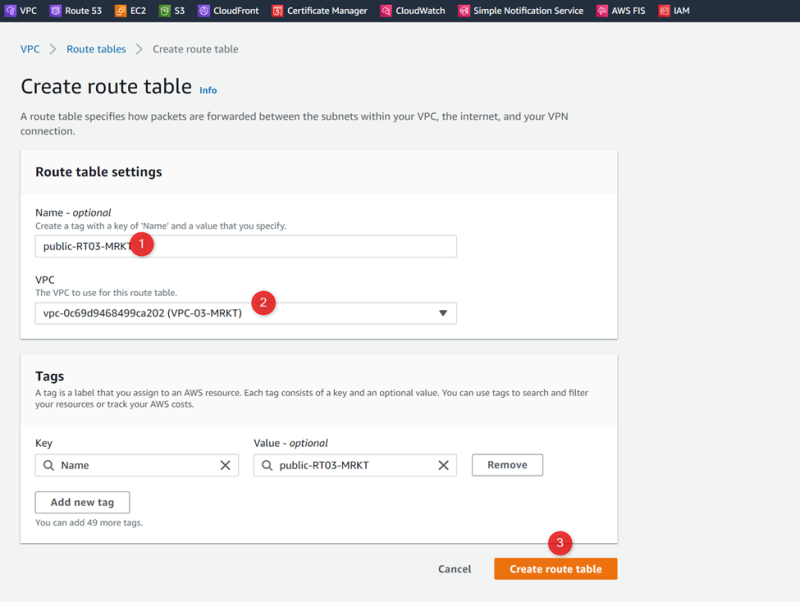
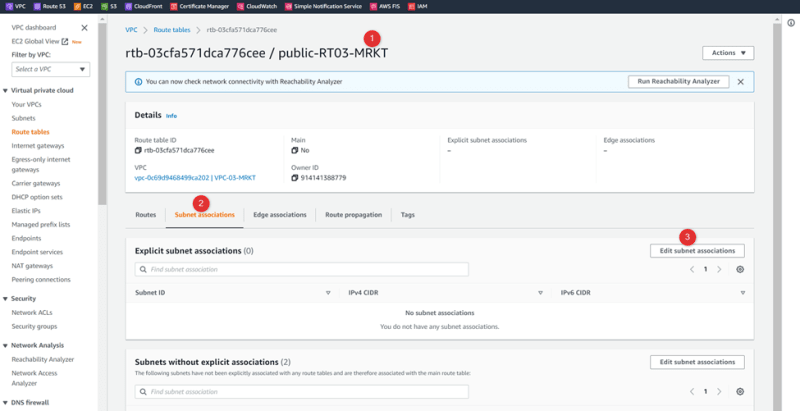
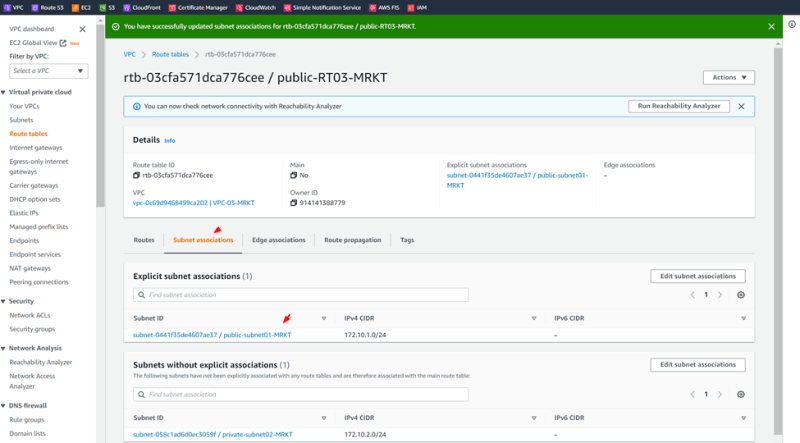
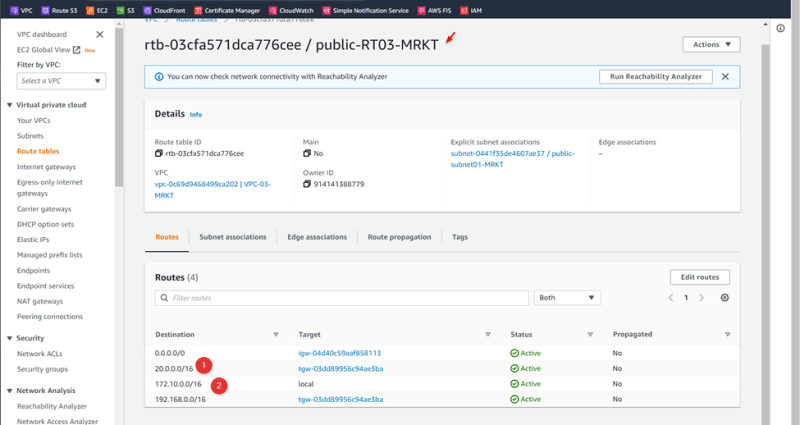
VPC-03-MRKT Public-RT03-MRKT
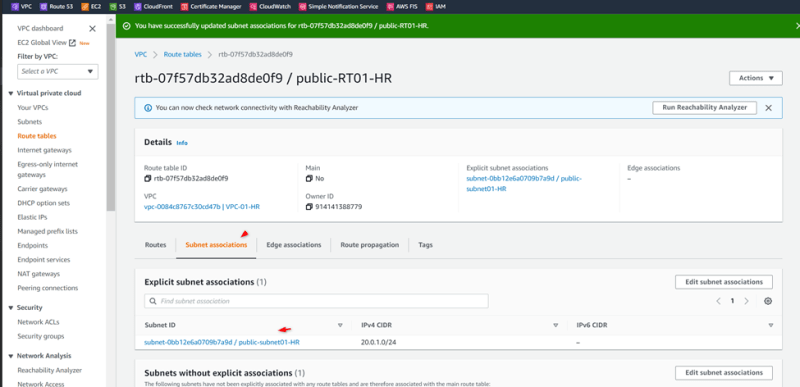
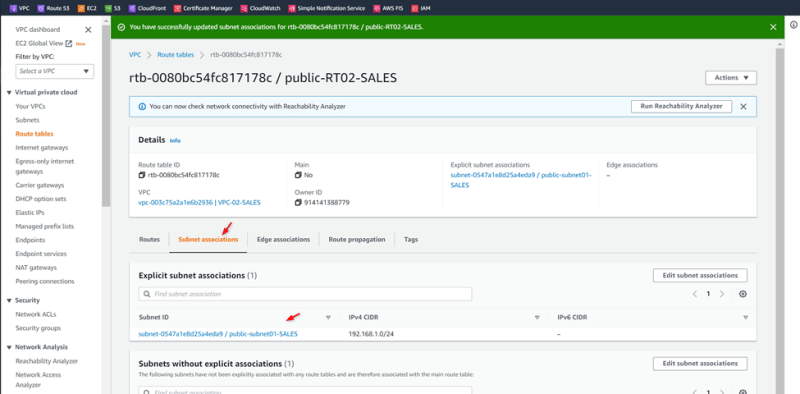
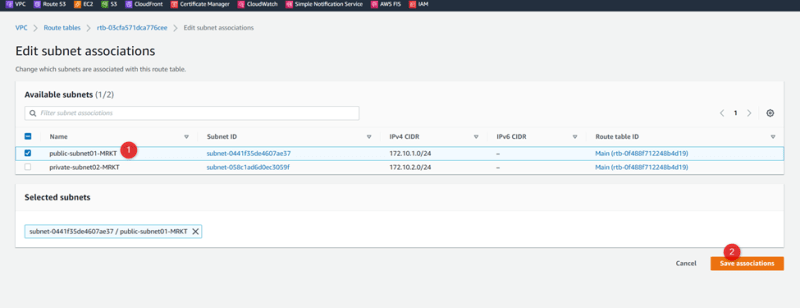
Associate public HR subnet
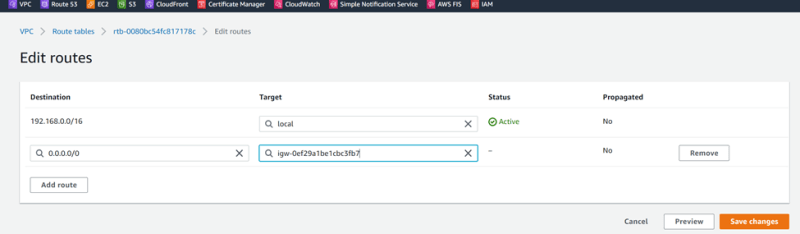
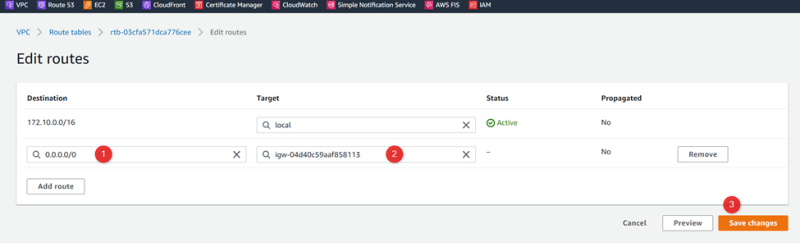
Create Route Public-RT03-MRKT
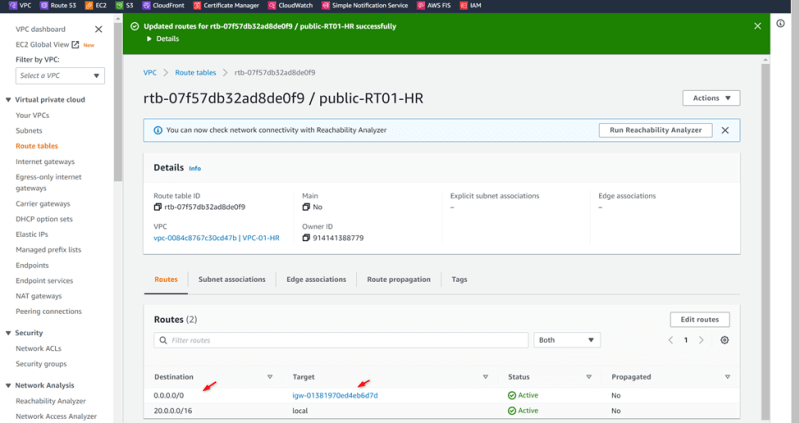
Add igw
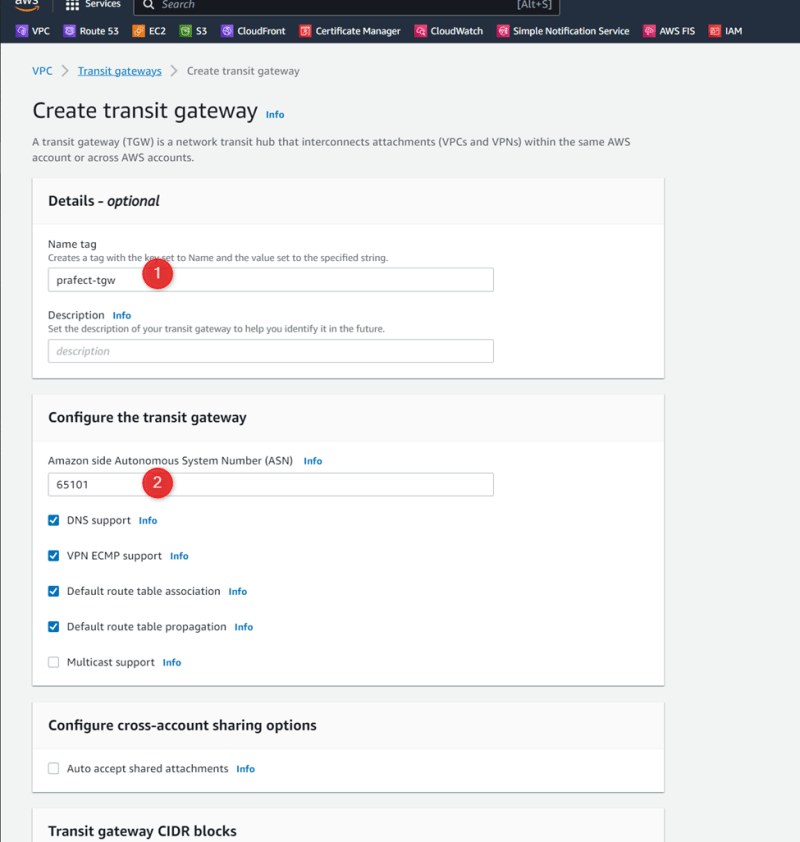
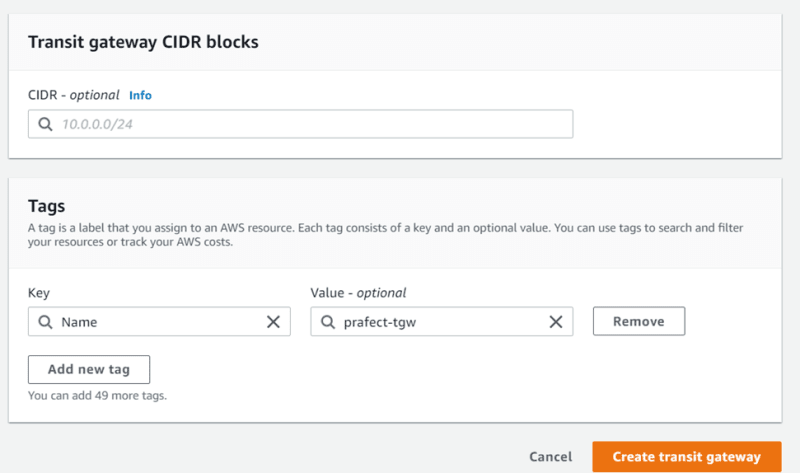
Transit gateway: prafect-tgw
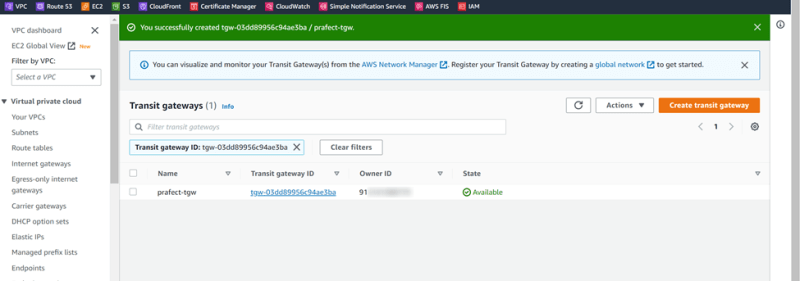
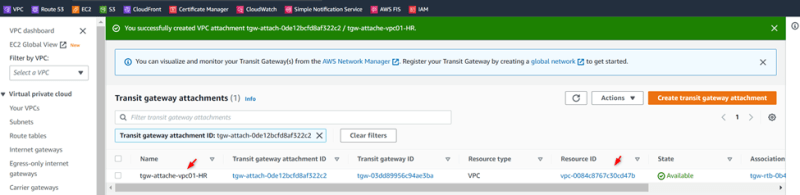
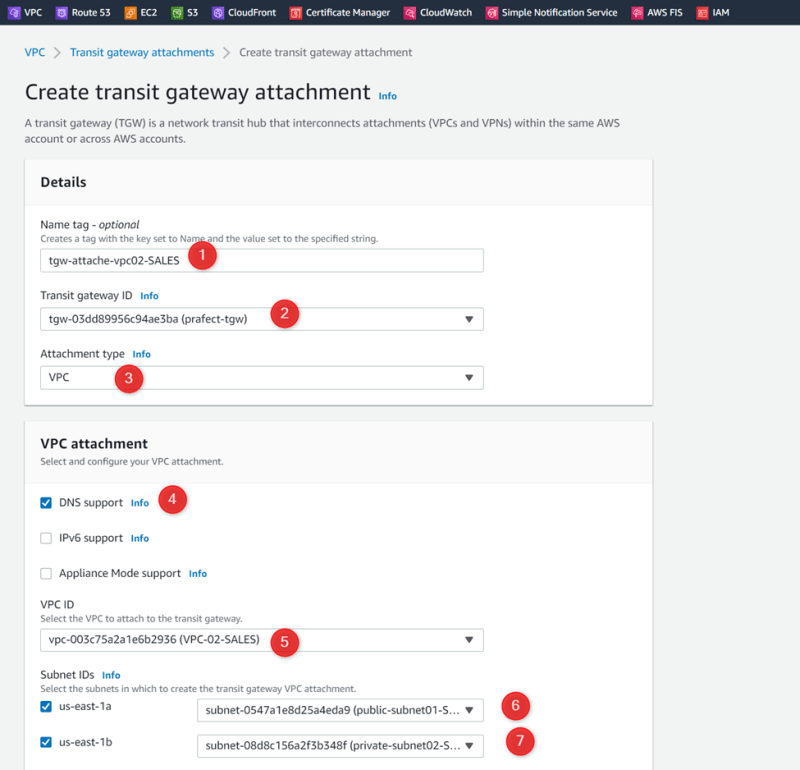
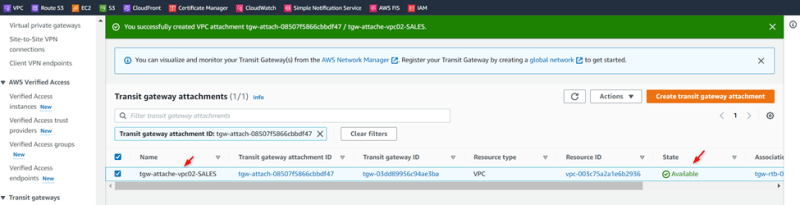
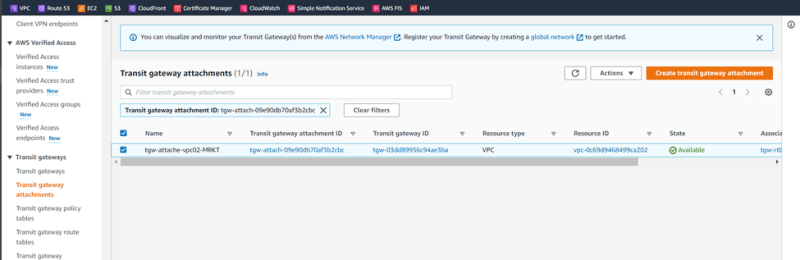
Create Transit gateway attachments:
Attachment01: VPC01-HR
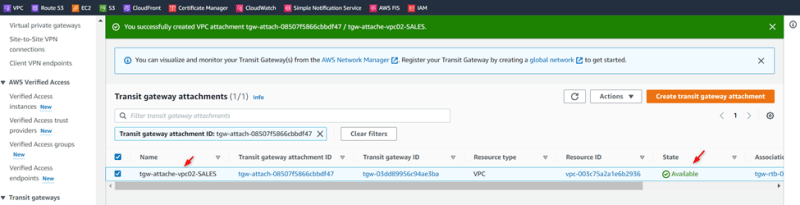
Attachment02: VPC02-SALES
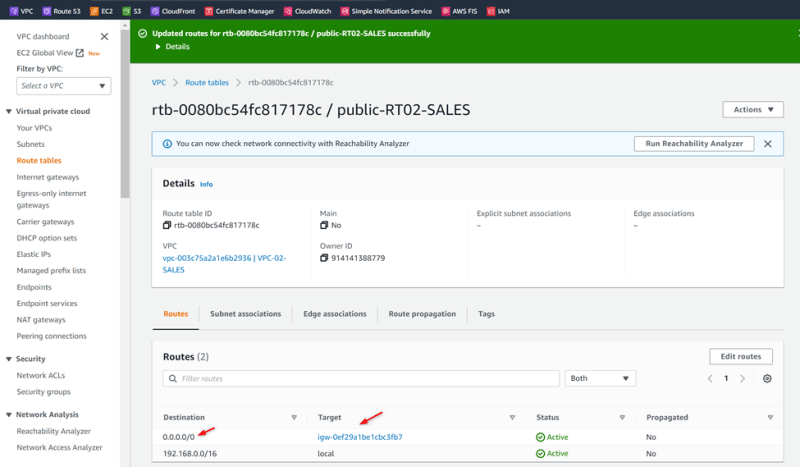
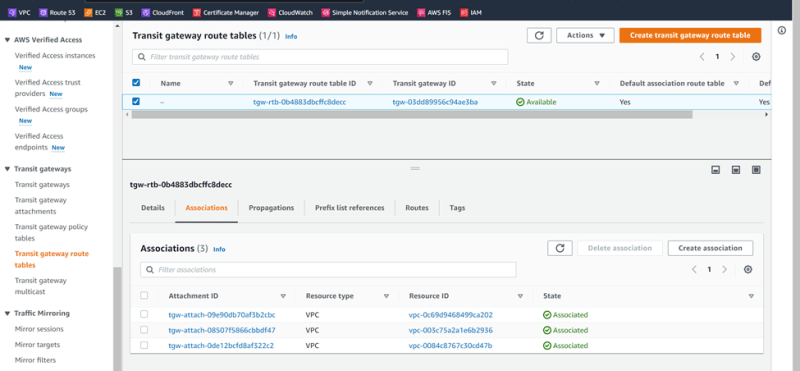
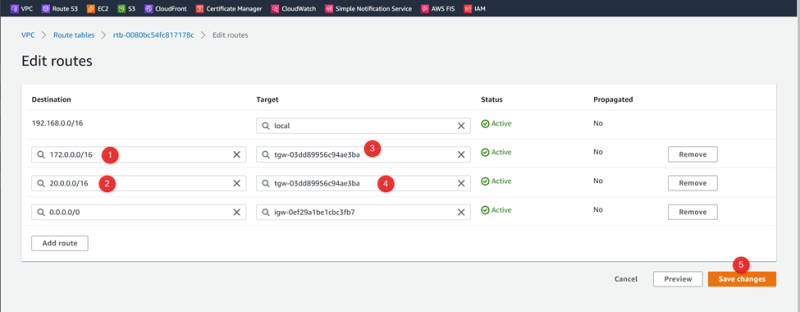
Routes

Update Route Tables of VPCs
VPC VPC CIDR Block Availability Zone Availability Zone CIDR Block
VPC-01-HR 20.0.0.0/16 Us-east-1a 20.0.0.0/24
VPC-02-SALES 192.168.0.0/16 Us-east-1a 192.168.0.0/24
VPC-03-MRKT 172.10.0.0/16 Us-east-1a 172.10.0.0/24
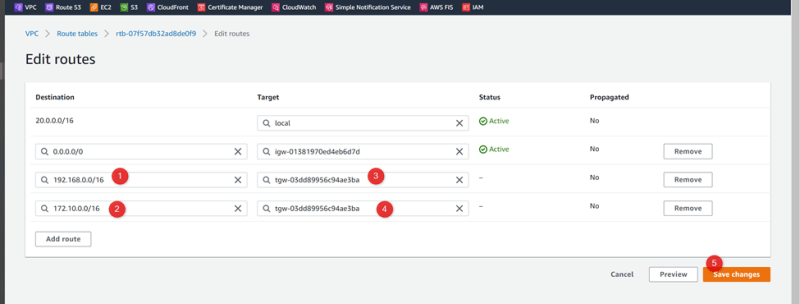
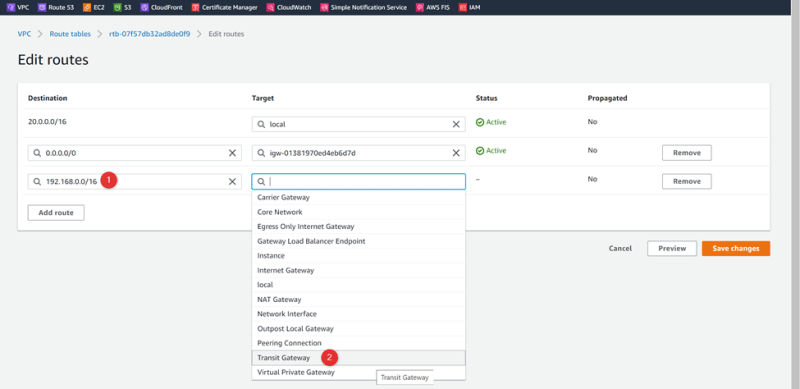
Add cross routes for VPC01-HR
Go to Route Table : public-RT01-HR
Add TGW routes for VPC02-SALES and VPC03-MRKT
VPC-03-MRKT 172.10.0.0/16
Add Cross route for VPC02-SALES
Select VPC02-SALES
Add routes for VPC01-HR and VPC03-MRKT
VPC-01-HR 20.0.0.0/16 Us-east-1a 20.0.0.0/24
VPC-03-MRKT 172.10.0.0/16 Us-east-1a 172.10.0.0/24
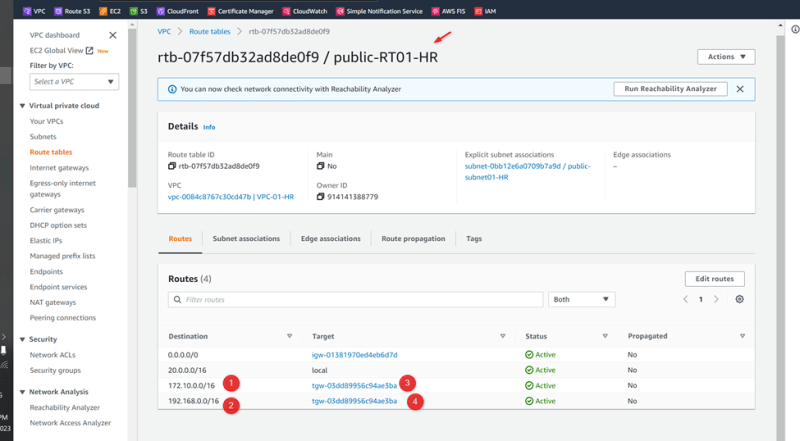
VPC VPC CIDR Block Availability Zone Availability Zone CIDR Block
VPC-01-HR 20.0.0.0/16 Us-east-1a 20.0.0.0/24
VPC-02-SALES 192.168.0.0/16 Us-east-1a 192.168.0.0/24
Select Route table VPC-3-MRKT
VPC01-HR
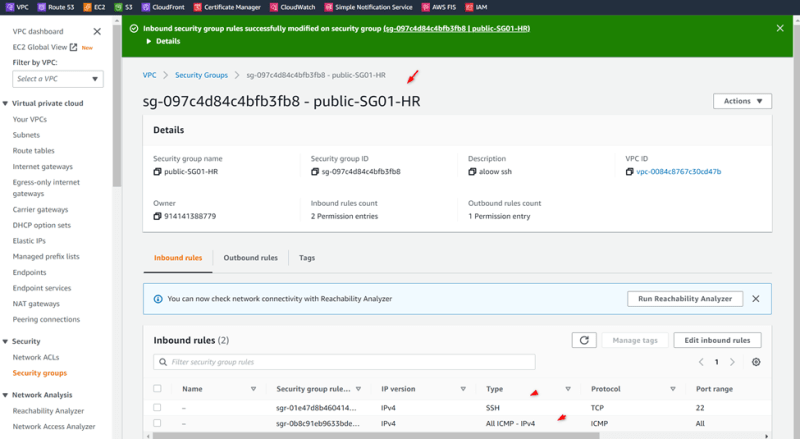
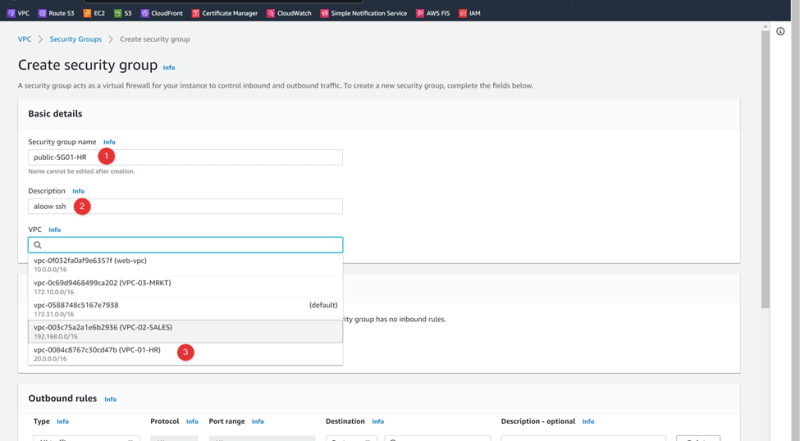
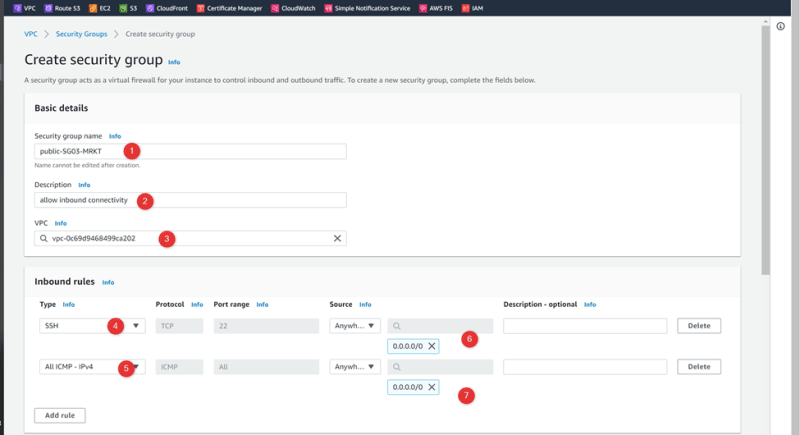
Security Group: Public-SG01-HR
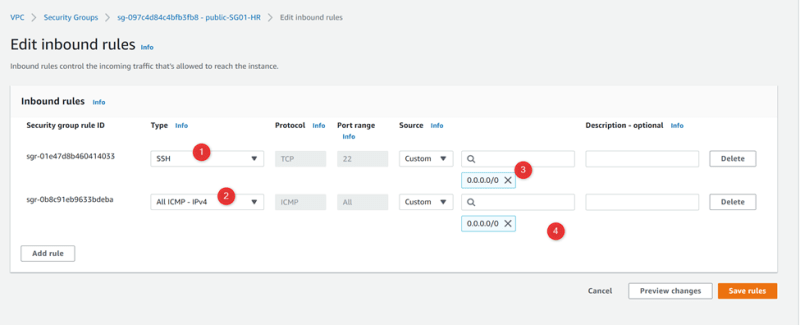
Rule 1: All SSH , 22, source: 0.0.0.0/0
Rule 2: All ICMP, All, source: 0.0.0.0/0
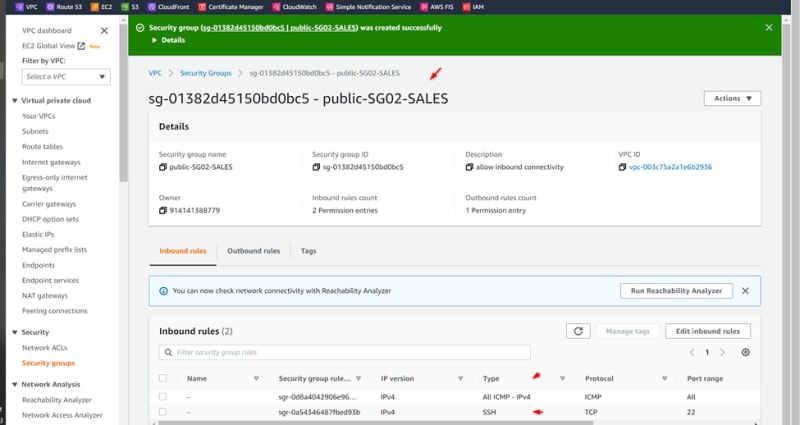
VPC02-SALES
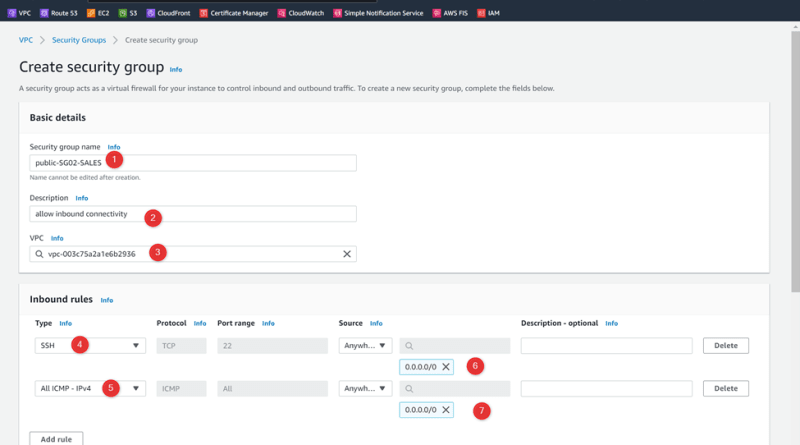
Security Group: Public-SG02-SALES

Add rules:
Rule 1: All SSH , 22, source: 0.0.0.0/0
Rule 2: All ICMP, All, source: 0.0.0.0/0
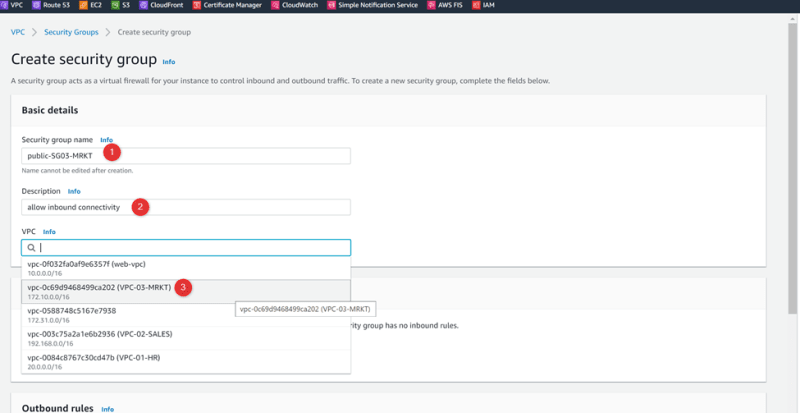
VPC02-MRKT
Security Group: Public-SG03-MRKT

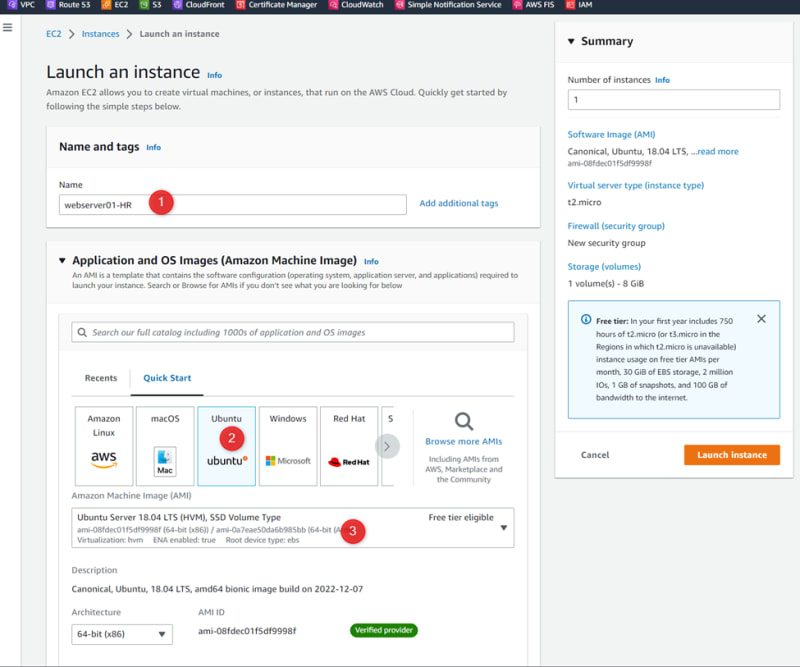
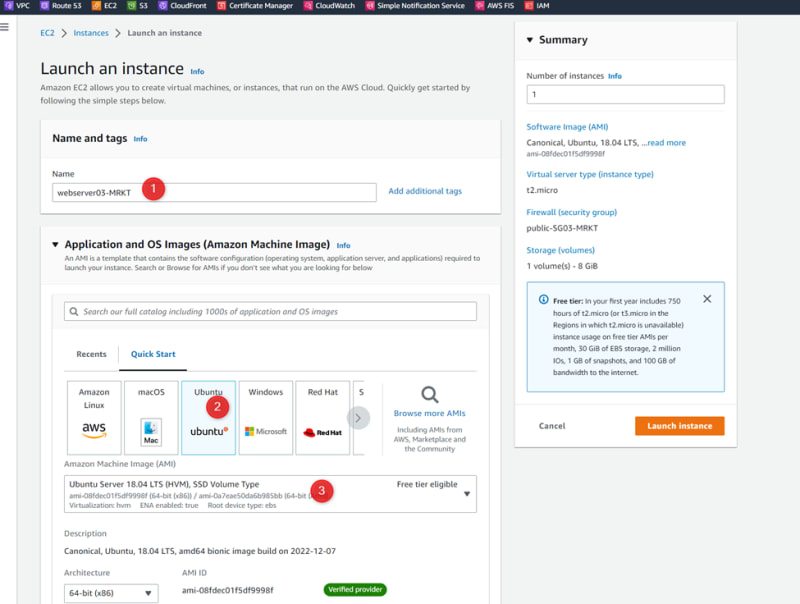
Launch EC2 machines in each VPC’s
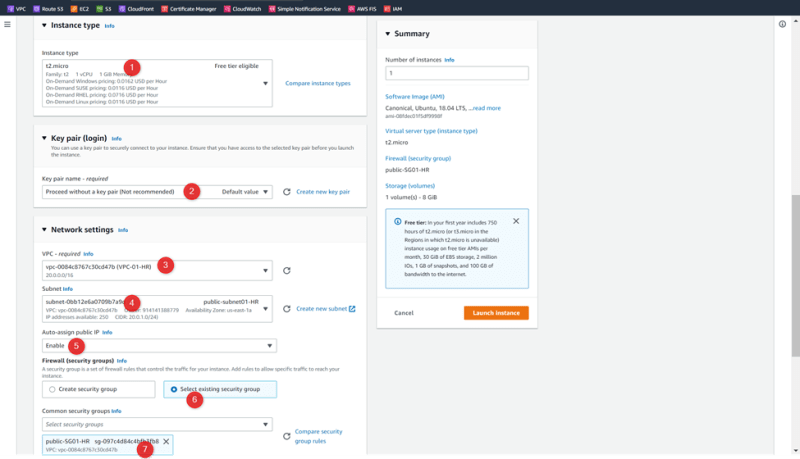
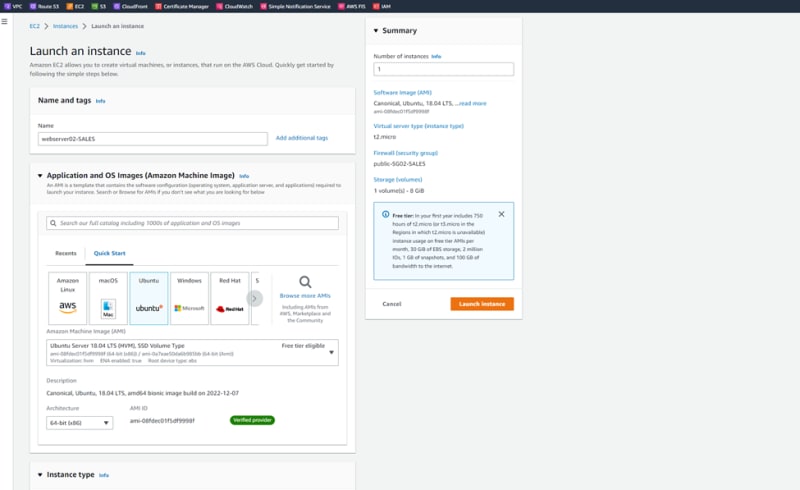
Repeat the same steps for VPC02-SALES & VPC03-MRKT
Launch webserver02-SALES
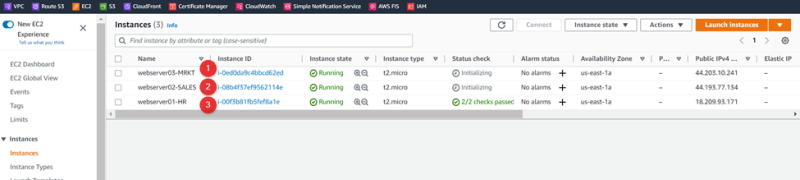
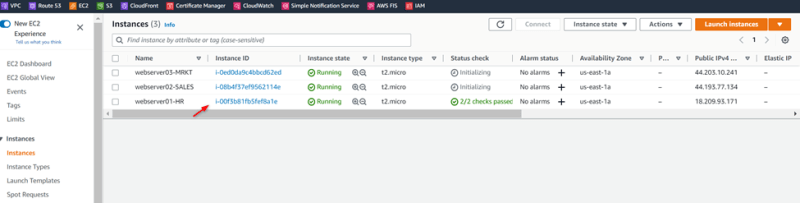
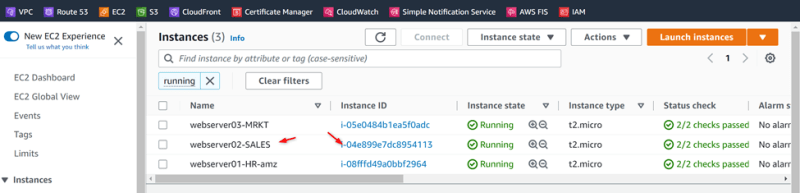
Verify the Connectivity from All VPC’s Webservers with each other
Check connectivity via TGW
Connect to EC2 webserver01-HR from VPC01-HR
Ping private IPs of VPC02-SALES – webserver02-SALES and VPC03-MRKT-webserver03-MRKT
Open webserver01-HR and connect
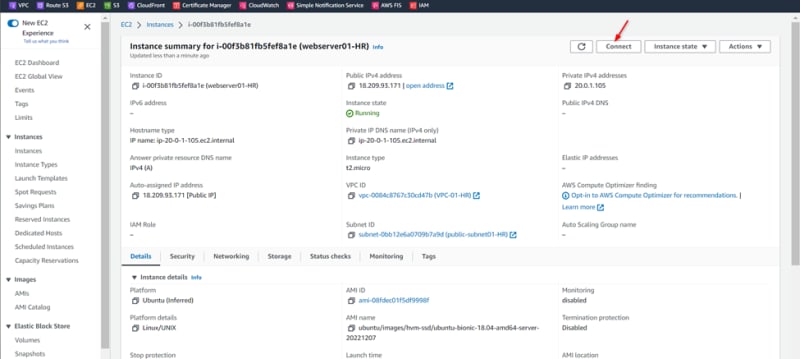
Get the Private IPs of both the webservers
Webserver02-SALES
Private ip: 192.168.1.173

Test the connection: Test 1 – From VPC01-HR to VCP02-SALES
Expected: The ping should return the ICMP response
Ping 192.168.1.173

Actual: The ping has returned the ICMP response
Ping successful to private ip from webserver01-HR to webserver02-SALES which are on two different departments’ VPC’s and connected through TGW
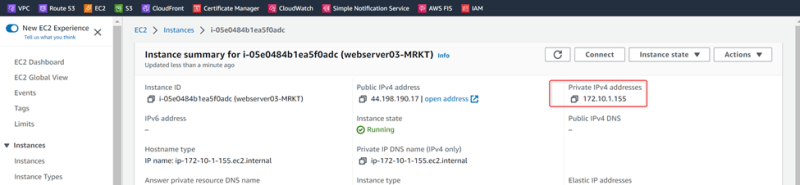
Webserver03-MRKT
Private ip: 172.10.1.155
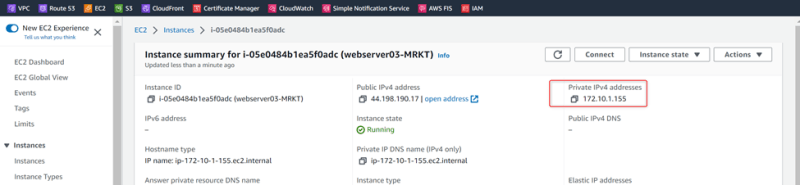
Test the connection: Test 2 – From VPC01-HR to VCP02-MRKT
Expected: The ping should return the ICMP response
Ping 172.10.1.155
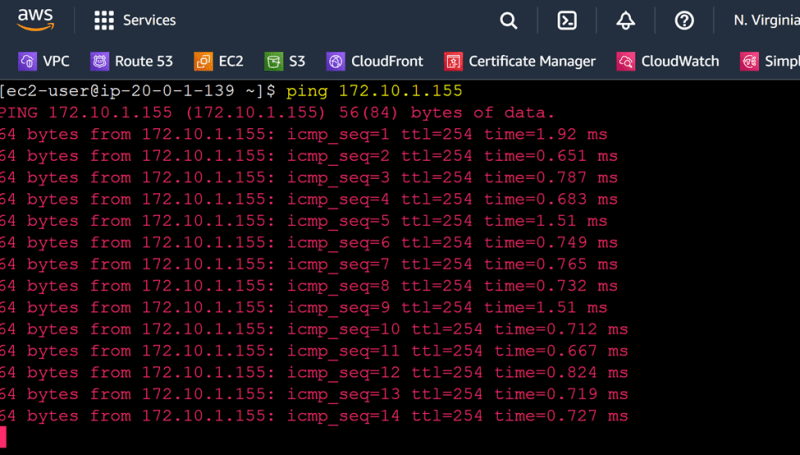
Actual: The ping has returned the ICMP response
Ping successful to private ip from webserver01-HR to webserver03-MRKT which are on two different departments’ VPC’s and connected through TGW
Connect to EC2 webserver02-SALES from VPC02-SALES
Ping private IPs of VPC01-HR – webserver01-HR and VPC03-MRKT-webserver03-MRKT
Open webserver02-SALES and connect
Webserver01-HR
Private ip: 20.0.1.139
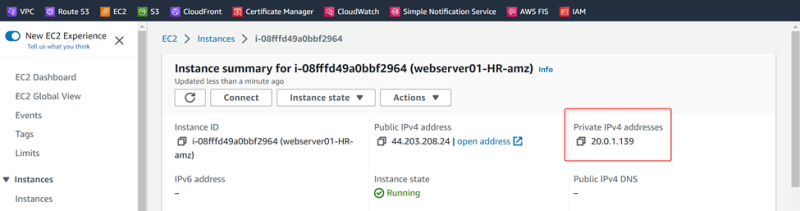
Test the connection: Test 1 – From VPC02-SALES to VCP01-HR
Expected: The ping should return the ICMP response
Ping 20.0.1.139
Actual: The ping has returned the ICMP response
Ping successful to private ip from webserver02-SALES to webserver01-HR which are on two different departments’ VPC’s and connected through TGW
Webserver03-MRKT
Private ip: 172.10.1.155
Test the connection: Test 2 – From VPC02-SALES to VCP02-MRKT
Expected: The ping should return the ICMP response
Ping 172.10.1.155
Actual: The ping has returned the ICMP response
Ping successful to private ip from webserver02-SALES to webserver03-MRKT which are on two different departments’ VPC’s and connected through TGW
Clean up project
In conclusion, the deployment of AWS Transit Gateway stands as a pivotal solution that seamlessly connects and manages the networking needs of various departments, including Sales, Marketing, and HR. This robust infrastructure allows for efficient communication, data transfer, and collaboration across the organization's different segments. By leveraging the power of AWS Transit Gateway, businesses can achieve enhanced scalability, simplified network management, and improved overall performance. As we navigate the evolving landscape of cloud technologies, embracing solutions like AWS Transit Gateway becomes integral to fostering a more connected, streamlined, and future-ready enterprise. Here's to unlocking the full potential of network architecture and paving the way for innovation in the digital era.
Connect with me on these platforms and stay updated with the latest in Cloud/DevOps technology and development! 🚀🔗😊
🌐 Website: praful.cloud 🚀
🔗 LinkedIn: Connect with me on LinkedIn 🤝
💻 GitHub: Explore my projects on GitHub 📂
🎥 YouTube: Check out my tech tutorials on YouTube 🎬
📝 Medium: Read my tech articles on Medium 📚
🔗 Dev.to: Follow me on Dev.to for cloud/devops-centric content 🖥️








































Top comments (0)