This is a walkthrough on the Bounty Hacker room in TryHackMe
This is a beginner room.
I think this could be helpful for CEH preparation, this is not too complex.
These are the steps I followed to get all the answers in the room.
I used nmap to do a port scan on the system.
nmap -sS <IP-address>
I found three open ports:
-- 21 ftp
-- 22 ssh
-- 80 http
We see a website and we have some information on the website.
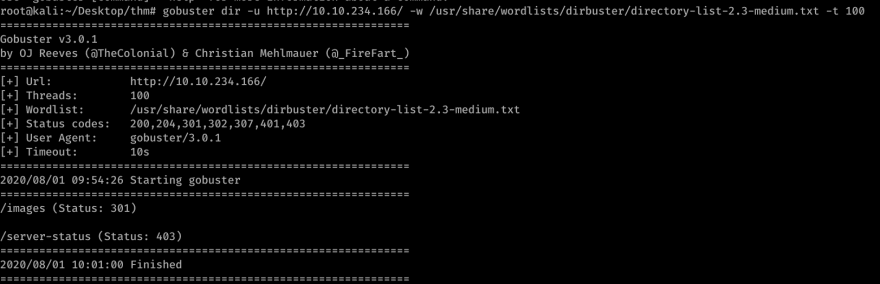
Then I tried to do a sub-directory scan using Gobuster, available in Kali Linux.
gobuster dir -u HTTP://<IP-address>/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
Here the option
dir is for directory scan
-u is for URL
-w is for wordlist
-t is for number of threads to run the scan
The scan does not show much either.
And with this information, we can't do much. So, I went through an aggressive scan:
nmap -A <IP-address>
We can see that the ftp is vulnerable with anonymous login.
Found this useful for this step
ftp <IP-address>
And type Name as anonymous and then no need for a password.
When in FTP can use ? to display a help menu.
To list all the files in your FTP session use ls
We see two files available. task.txt and locks.txt
We can set the local directory using lcd command.
Then we can use the get command to get the files from the system to our system to analyze them.
Check the files using cat command.
First I checked the task.txt file I see that the author is named lin. I assumed that must be the user of the system.
Now I checked the lock.txt this file looks like a password list for the user.
Now we have to brute-force the login for ssh, assuming the username is lin and passwords must be from this list (lock.txt).
I then used the hydra password cracking tool.
hydra -l lin -P locks.txt 10.10.234.166 -t 4 -e nsr ssh
Cracked the password.
Logged in as the user lin with the cracked password.
And at this point, we can exit the FTP connection.
Checked the files in the user directory using ls.
We see the user.txt file containing the user flag.
cat user.txt
Then I tried to pivot to the root directory, to see that we do not have sufficient permissions.
So can we do when we do not have enough permissions?
We can check what else we can do as the user lin using the command sudo -l.
We can see that the user lin can run tar as root.
Then I tried to check that in gtfobins. Found the exploit for that.
Ran the mentioned command and could pivot to root.
Then cd into the root user directory to find the root flag.
There were some dead ends but I could go around them.
Found this room a fun one.








Top comments (0)