Introduction
Cloud environments are always susceptible to security issues. A significant contributor to this problem is misconfigured resources.
Traditional IT Infrastructure was somewhat static; server hardware only changed every few years. With few changes occurring, security was also more static. The modern cloud environment is a much different challenge. In cloud environments, servers, services, and storage are created with automation, resulting in a dynamic and potentially ever-changing server environment.
Standardized policies and regular enforcement of best practices are key to reducing security risks. New automation can be created to enforce these policies on an ongoing basis. Even if the configuration drifts, automation can pull systems back into compliance.
Unencrypted S3 buckets are an example of a configuration setting that could expose enormous quantities of sensitive data. In this article, we will look at using Relay to enforce encryption that is easy to set up and monitor.
Setting Up Relay for AWS
Relay is an online platform with Graphical User Interface (GUI) and Command Line Interface (CLI) for all your cloud automation use cases. In our example, we will be using the GUI web interface.
You will need to set up a Relay account at https://app.relay.sh/signup to create and run a workflow. The workflow will force encryption on specified S3 buckets in your Amazon Web Services (AWS) account.
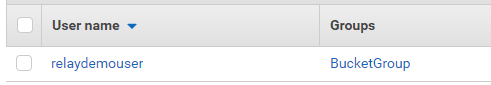
The Relay AWS connection requires creating an Identity and Access Management (IAM) user with permissions to edit S3 buckets. In your AWS console, go to the IAM dashboard and set up an IAM user. For example, under “Access management,” I set up a group called “BucketGroup” and a user named “relaydemouser”. Make sure you keep a copy of the “Access key ID” and “Secret access key” as you will need these. The “Secret access key” is only shown once.
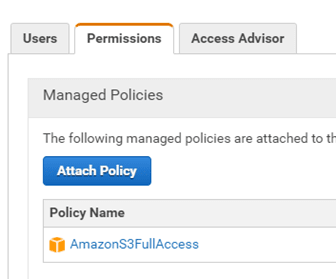
The user/group will need permissions to access the S3 buckets. For the example above, I added the policy “AmazonS3FullAccess” to the permissions of the BucketGroup. Do the same with the user/group you create.
This policy gives the IAM user, or group of users, full access to the S3 buckets, including checking configuration, listing buckets, and encrypting S3 buckets.
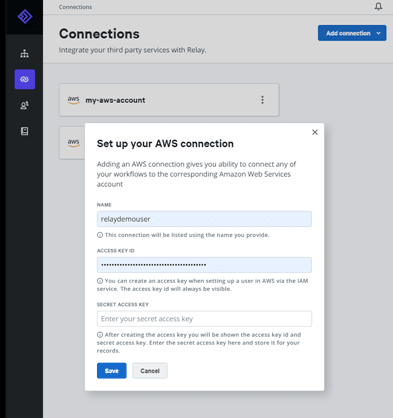
Once you have a user with the required permissions, you can set up the Relay connection configuration. Open the Connections section of Relay and add a connection to AWS with this IAM user.
You can choose any name for the connection but will need to use the AWS “Access key ID” and “Secret access key” for your IAM user as shown below:
Creating a Workflow
Relay has many sample workflows, including one to remediate unencrypted S3 buckets. Use this link to find it, or, from inside the GUI, click on the workflow icon and then Explore workflows. Under the Security heading, you will see “Remediate unencrypted S3 buckets.”
Looking at a new AWS S3 Storage bucket’s properties page, you will see that encryption is disabled by default.
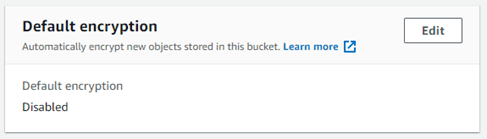
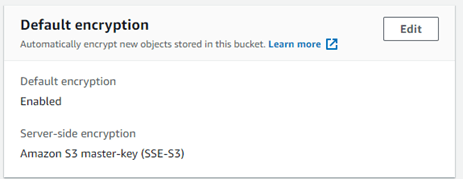
The workflow will enable server-side encryption. After running the workflow, your default encryption settings will look like this:
You can review the workflow contents (code, graph, and so on) then click on the “Use this workflow” button.
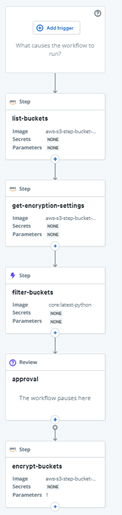
Clicking Try this workflow will bring you to a new workflow dialog with a suggested name. Note that workflow names must be unique within your account. Click on Create workflow and Relay will display the workflow graph:
To run the workflow, click Run in the top right corner of the workflow page. Running the workflow will bring up a dialog showing dryRun = true. Doing a dry run will test the logic but will not make any changes. Go ahead and run the workflow in dryRun mode. Visit the Using Workflows section of the documentation for more information on workflows.
The workflow will stop at the approval step and will not execute the action step to encrypt the S3 bucket. In dryRun mode, the Yes and No approval buttons are disabled. If you rerun the workflow and set the dryRun dialog to false, Relay will stop the workflow at the approval step and allow you to click on “Yes” or “No.” If you click on “Yes,” the flow will continue and encrypt the S3 buckets.
After the workflow is complete, go back to AWS and check the encryption status on your S3 bucket. The buckets that had previously been unencrypted should now be encrypted.
Setting up a Trigger
Relay supports multiple ways to trigger a workflow. We have already walked through the manual trigger, running a workflow manually. You can also schedule a trigger to run automatically, using a process similar to that of a Linux cron job. Relay also supports webhook and REST API triggers. Services which support webhooks can post a JSON payload to Relay when an event happens. The Relay REST API receives JWT-authenticated requests from a remote system and runs a workflow in response. Read all about triggers in the Using Triggers section of the documentation.
For this example, we’ll use a simple schedule trigger to run the workflow at midnight every day. Click on the “Add trigger” button in the first block of the graph to display the Add trigger dialog.
Clicking on “Run a trigger every day” will bring up a code snippet that will be added to your workflow.
Once you save the modified code, you will see that the trigger block in the graph now says it will run every day. A summary of the five digits of Cron time setting ‘* * * * *’ is shown below—an asterisk (*) means no specific value.
| Position | Time Unit | Possible Values |
|---|---|---|
| 1 | Minute | 0 to 59 or * |
| 2 | Hour | 0 to 23 or * |
| 3 | Day of Month | 1 to 31 or * |
| 4 | Month | 1 to 12 or * |
| 5 | Day of Week | 0 to 7 or * Both 0 and 7 represent Sunday. |
When you run the workflow, it will run immediately, plus run automatically every day. You would need to remove or modify the approval step if you want the workflow to run continuously.
You can remove the schedule trigger by deleting the triggers section in the code and saving changes. The graph button will change back to “Add trigger.”
Next Steps
You have configured a workflow to add encryption to AWS S3 storage buckets, and learned to set up a scheduled trigger. As described in this article, many preconfigured workflows make it easy to get started with Relay. Plus, the code is readily available for modification and expansion outside the GUI interface.
Other example Relay flows are available for many Azure, AWS, and GCP tasks.
Check out Relay and start automating your DevOps maintenance today.






Top comments (0)